Data link protection method and device
A data link, normal data technology, applied in the field of data communication, can solve problems such as interruption, reduce system stability and anti-attack ability, and achieve the effect of avoiding interruption, improving stability and anti-attack ability
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
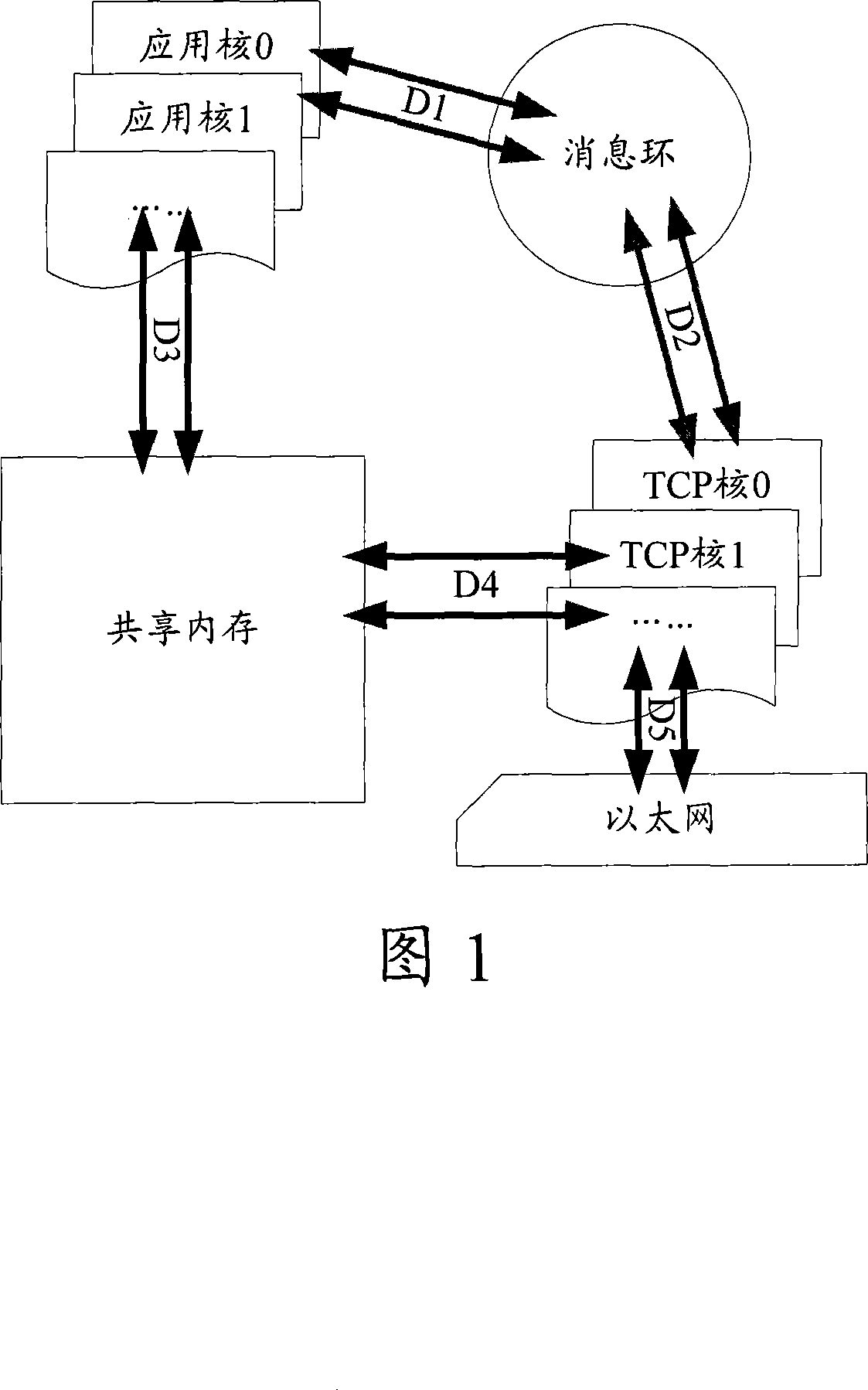
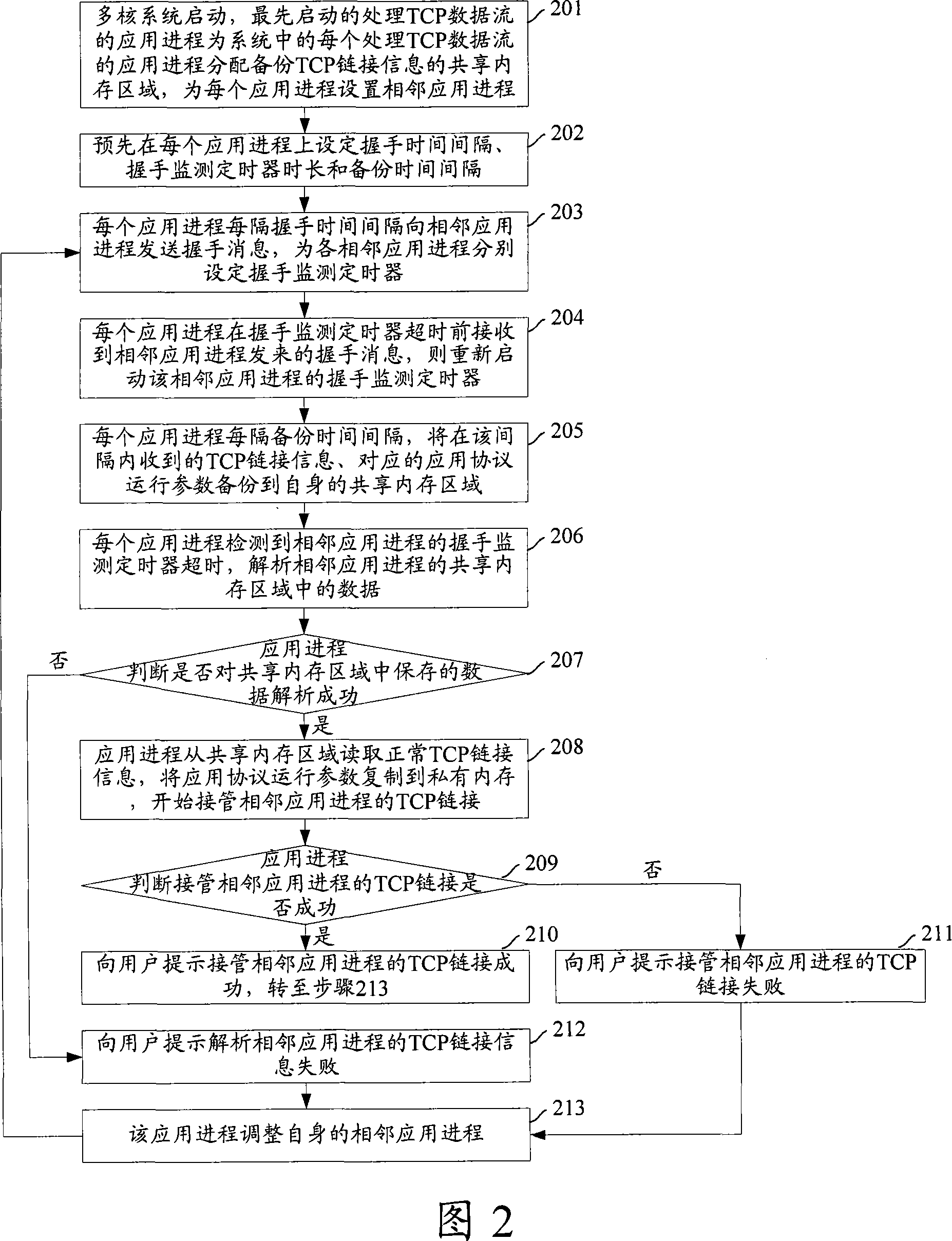
[0066] Fig. 2 is the flowchart that realizes data link protection in the multi-core system that runs Linux operating system in SMP mode provided by the embodiment of the present invention, as shown in Fig. 2, its specific steps are as follows:
[0067] Step 201: The multi-core system is started, and the first started application process for processing TCP data streams allocates a shared memory area for backing up TCP link information to each application process in the system for processing TCP data streams, and assigns a shared memory area for each application process The adjacent application processes are respectively set, and the allocation principles of the shared memory area and the setting principles of the adjacent application processes are sent to each application process.
[0068] The application process that processes the TCP data stream that starts first usually applies for a piece of continuous shared memory after it is started, and then distributes the shared memory...
Embodiment 2
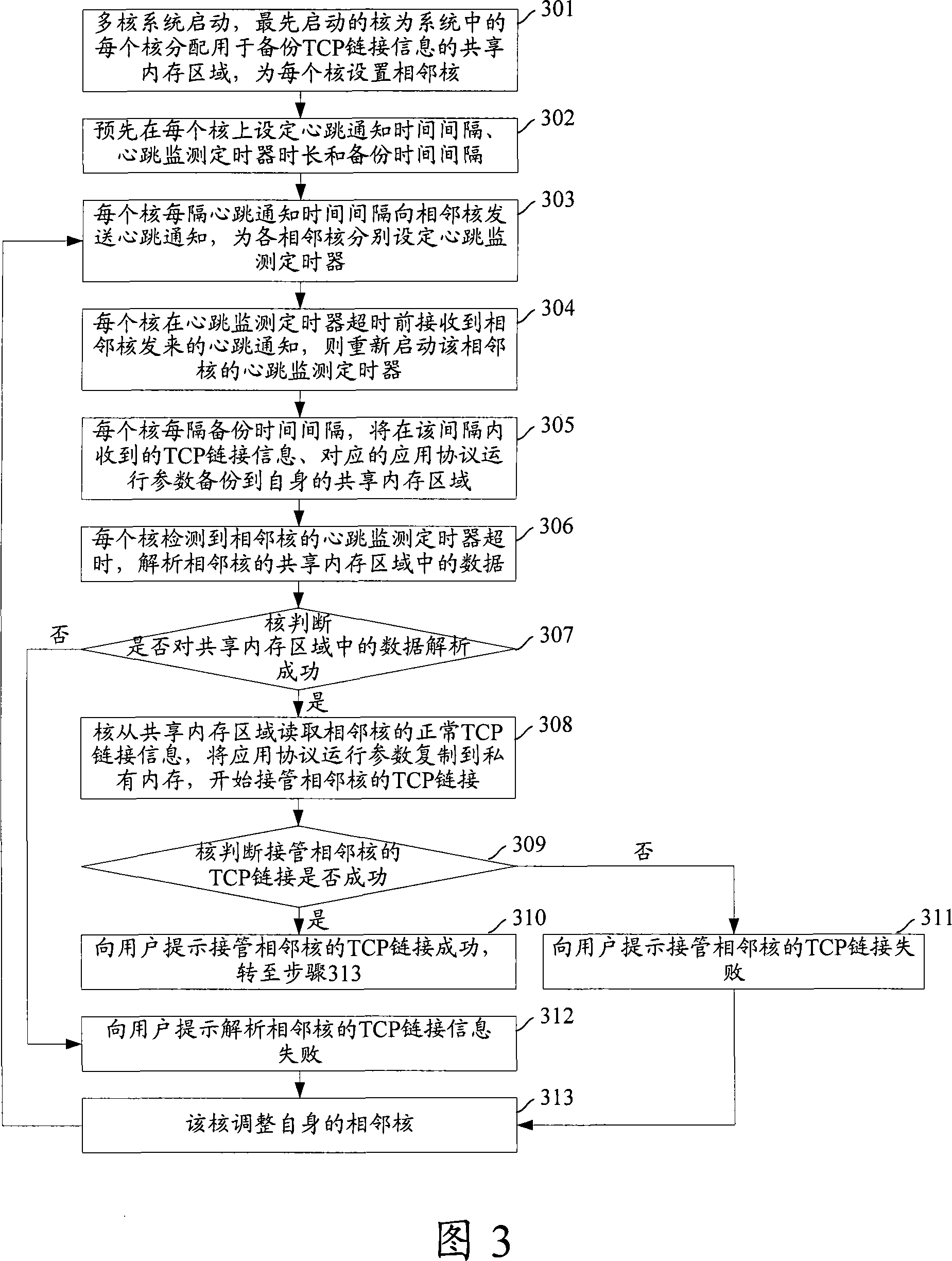
[0098] Fig. 3 is the flow chart that realizes data link protection under the multi-core system that runs the single-thread application program without operating system on each core that the embodiment of the present invention provides, in this embodiment, because each core runs a single Thread application, therefore, each single-thread application can be uniquely identified by the identification of its core, as shown in Figure 3, the specific steps are as follows:
[0099] Step 301: The multi-core system is started, and the core that starts first allocates the shared memory area required for backing up the TCP connection information for each core running a single-threaded application program, and sets adjacent cores for each core, and the shared memory area will be shared The memory allocation policy and adjacent core setting policy are sent to each core.
[0100] After the first started core is started, it usually applies for a piece of continuous shared memory, and then dist...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com