Management method for terminal equipment starting service in radio communication network
A technology of wireless communication network and terminal equipment, which is applied in the field of management for the safe use of network resources by mobile terminals
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
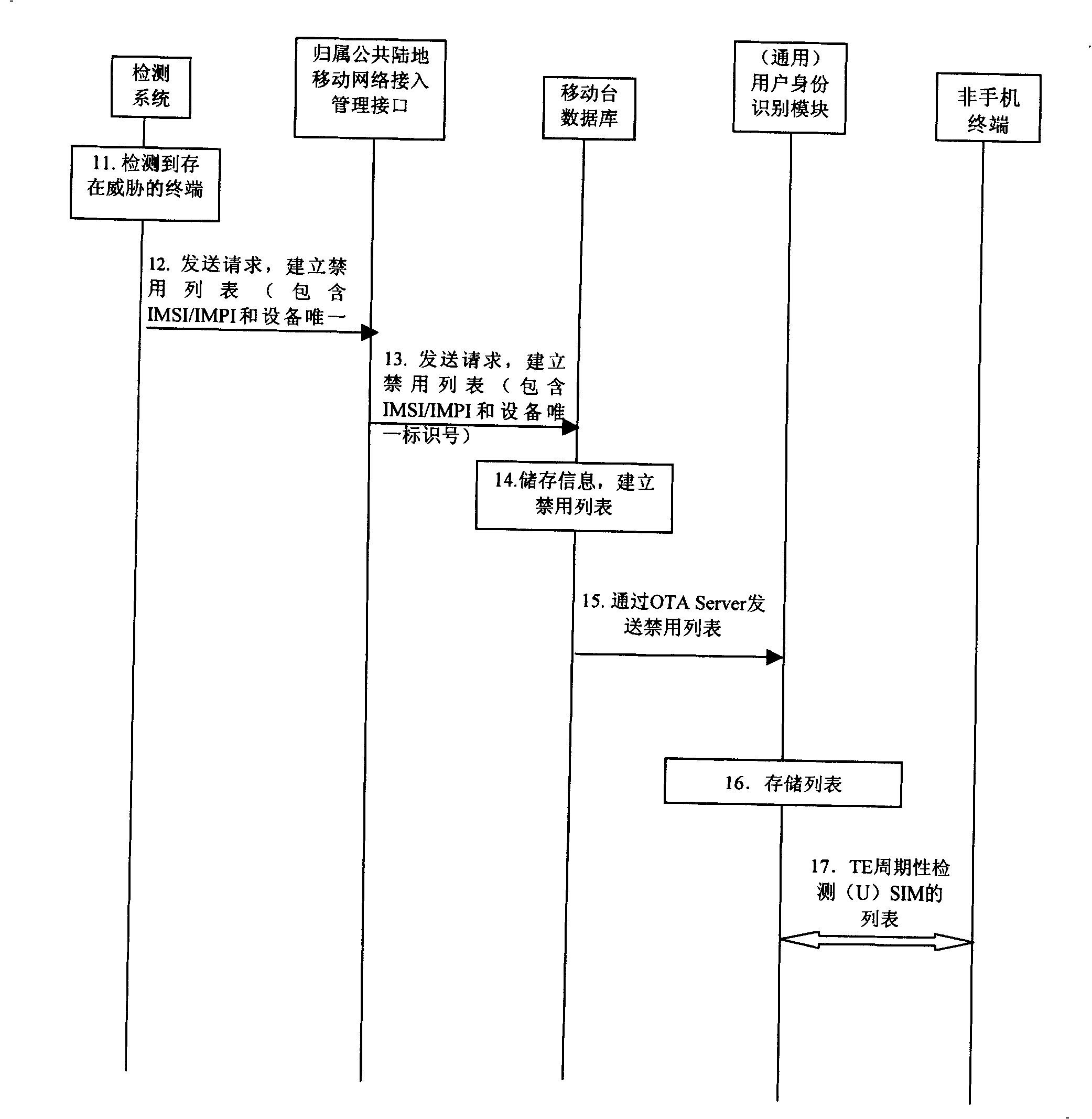
[0088] In the embodiment provided by the present invention, when the identification system detects a terminal with a threat, its specific implementation is as follows:
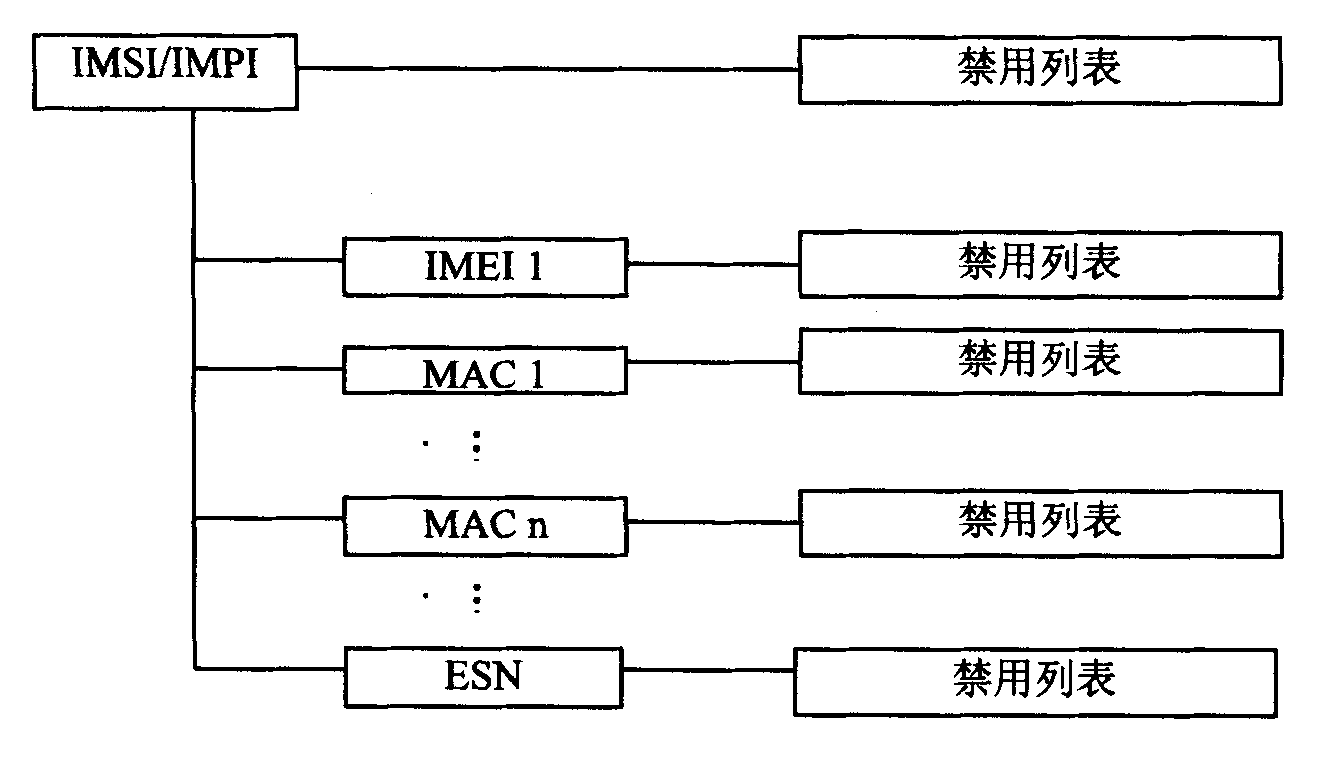
[0089] When the system detects a terminal device with threats, the HPLMN management interface will store the restricted services of the terminal in the MS database in the form of a list, generate a forbidden list in the MS database, and then the MS database will send this list through the OTA server to the (U)SIM card.
[0090] The process of this implementation is as follows figure 1 As shown, the detailed steps are as follows:
[0091] Step 11: Identify the terminal that the system detects a threat. The terminal may be a mobile phone or a non-mobile terminal. If it is a mobile phone, it can be processed according to the existing technology, or it can be processed by other settings. Of course, it can also be executed. Step 12, adopt the processing method provided by the present invention, if it is a non-mob...
Embodiment 2
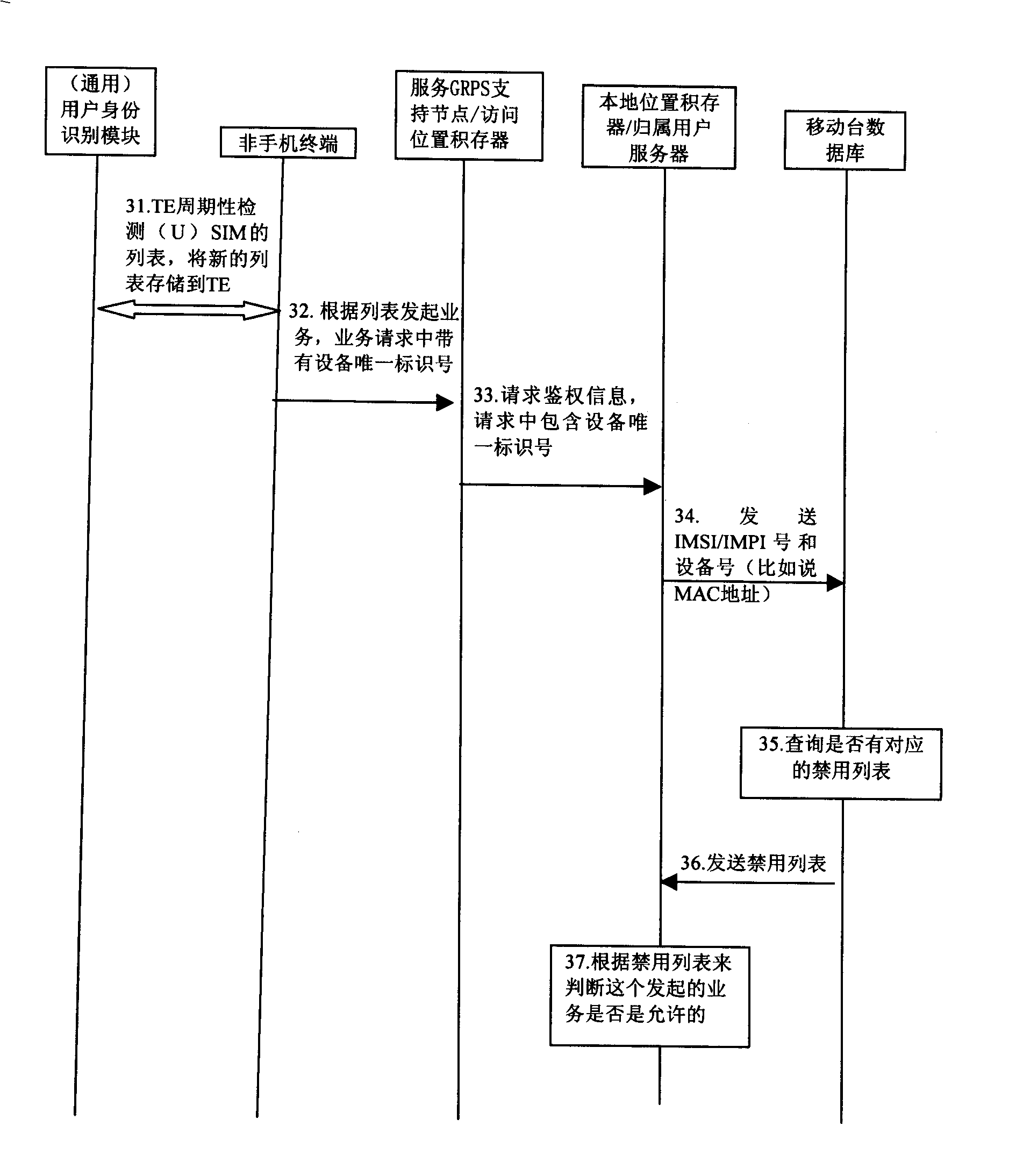
[0118] In this embodiment, the non-mobile terminal utilizes (U)SIM card information to access the network through the mobile communication system for authentication, thereby accessing the mobile network. The corresponding processing flow is as follows: image 3 As shown, it specifically includes the following steps:
[0119] Step 31, the TE periodically detects the forbidden list information in the (U)SIM card, and timely updates the forbidden list information stored in the TE according to the forbidden list in the (U)SIM card.
[0120] Step 32, TE initiates a service request carrying a device unique identification number via SGSN (Serving General Packet Radio Service Support Node) / VLR (Visitor Location Register) according to the forbidden list, and the service is not a restricted service in the forbidden list after detection;
[0121] This detection can perform preliminary detection on services initiated by non-mobile terminals, and can effectively prevent some prohibited ser...
Embodiment 3
[0136] In this embodiment, the WLAN UE (equipment for wireless local area network) uses the information of the (U)SIM card to still authenticate through the WLAN access network, so that the detailed implementation process of accessing the mobile communication network is as follows: Figure 4 As shown, the details are as follows:
[0137] Step 41, the WLAN UE periodically detects the information of the forbidden list in the (U)SIM card, and updates the forbidden list information in the WLAN UE in time;
[0138] Step 42, the WLAN UE initiates a service to the PDG (Packet Data Gateway) according to the forbidden list, and initially detects the service initiated by the WLAN UE;
[0139] Through the initial detection process, if the service initiated by the WLAN UE is a prohibited service in the prohibited list, it will be restricted and cannot be initiated, otherwise, the corresponding service can be initiated normally;
[0140] If there is no corresponding forbidden list in the ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com