Group calling authentication method for cluster system
A trunking system and group call technology, applied in the direction of radio/induction link selection and arrangement, selection of devices, etc., can solve the problems of slow call origination and slow call speed for users to join the call later, to overcome the slow speed and reduce Waste, the effect of ensuring a high-quality experience
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
no. 1 example
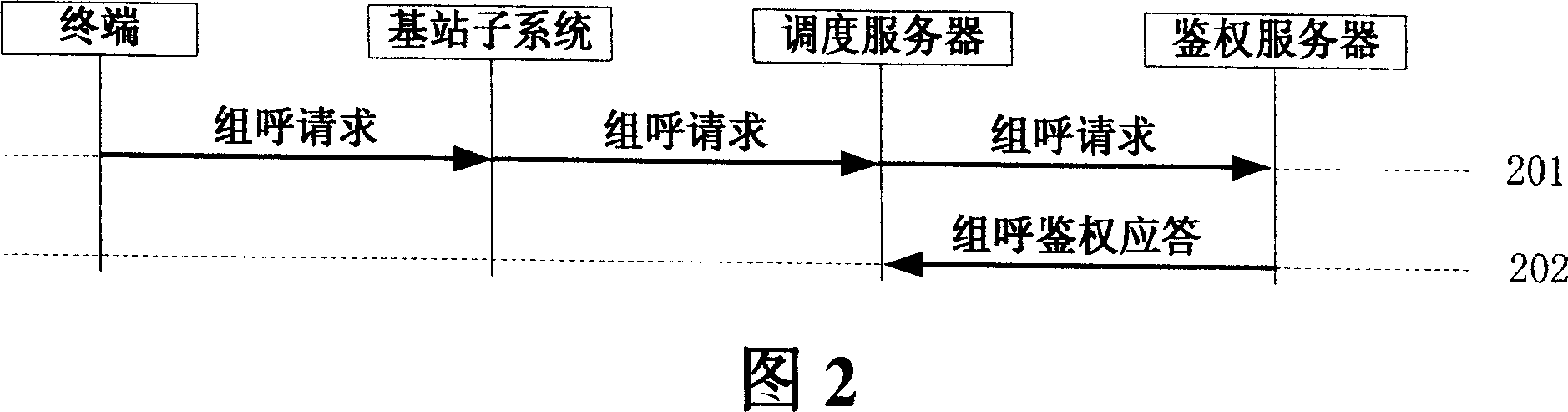
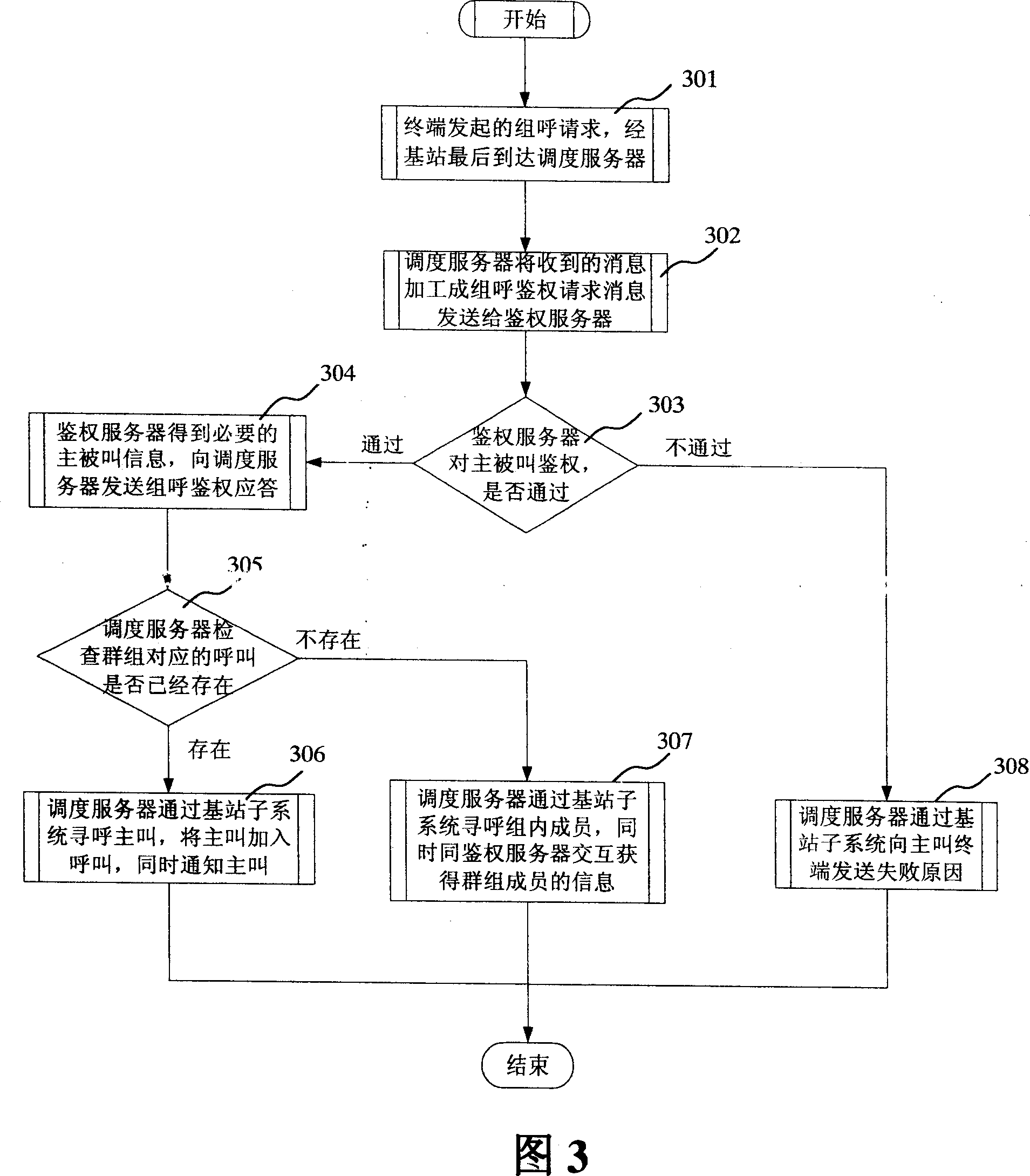
[0049] The first embodiment of the present invention is mainly realized by sending a group call request by a terminal user, as shown in Figure 3, which includes the following steps:
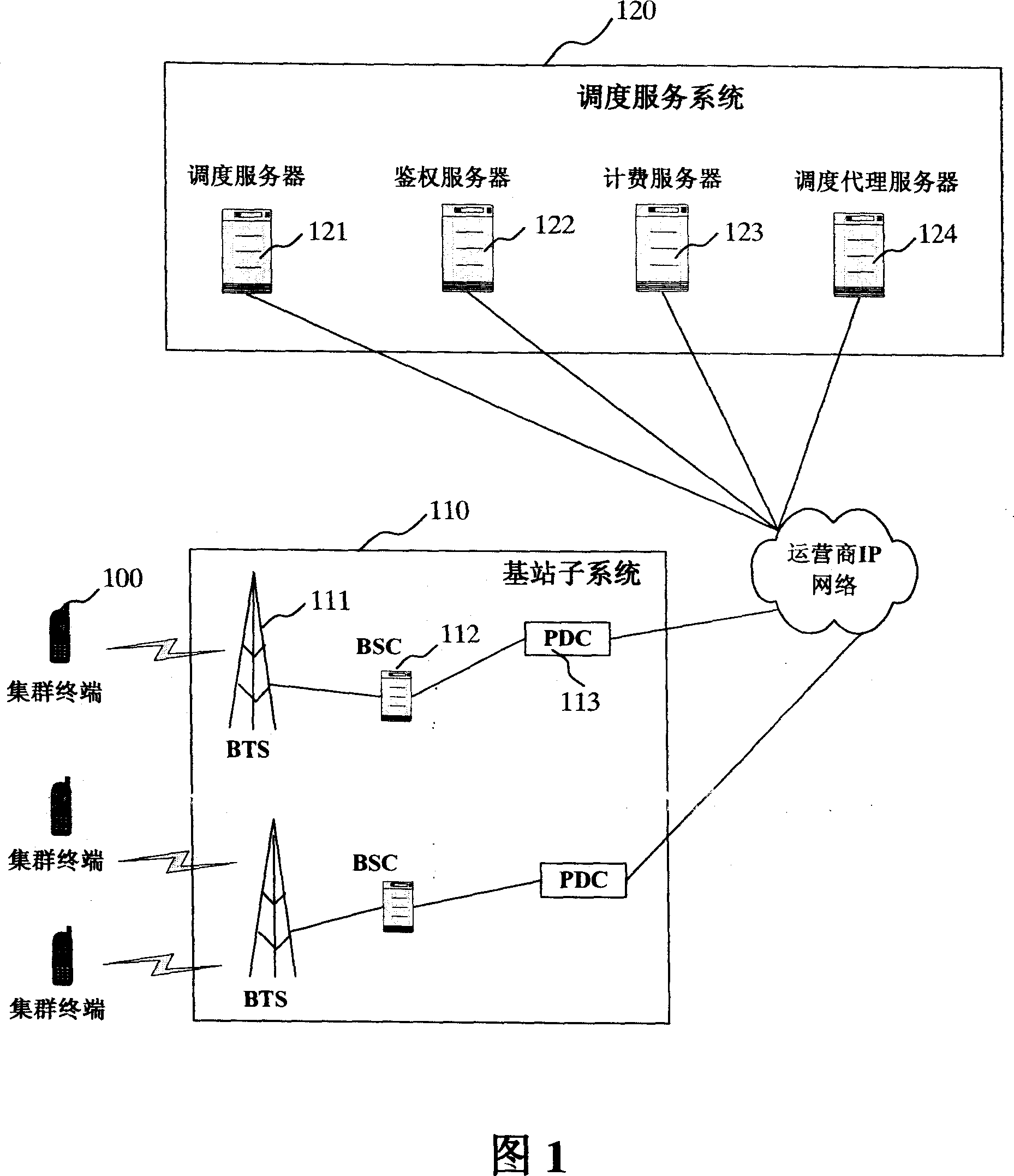
[0050] Step 301: The cluster terminal user dials a group number to initiate a group call, and the request reaches the dispatching server through the base station subsystem.
[0051] Step 302: The scheduling server takes out the attributes of the cluster terminal in the received request message, and at the same time takes out the group number and other attributes of the called group in this call, and then processes it into a group call authentication request message and sends it to the authentication server .
[0052] Step 303: The authentication server receives and analyzes the contents of the message sent by the dispatching server, and then authenticates the calling party and the called party, that is, judges whether the trunking terminal is legal, whether it has the right to initiate a group ca...
no. 2 example
[0083] The second embodiment of the present invention is realized by the dispatcher sending a group call request, comprising the following steps:
[0084] Step A, when the dispatcher (according to dispatching requirements) needs to call a group, he sends a group call request through the group call menu of the dispatching proxy server, and the request arrives at the dispatching server through the dispatching proxy server;
[0085] Step B: the scheduling server constructs a group call authentication request message according to the dispatcher calling and called group information in the request message, and sends it to the authentication server;
[0086] Step C: The authentication server takes out the content in the above request message received, obtains the information of the calling dispatcher and the number of the called group, and then judges whether the dispatcher is legal and has the authority to initiate the group call. Whether the group exists and whether it is legal, if t...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com