Wireless terminal and method for mutual locking and unlocking with user recognition card
A user identification card and wireless terminal technology, which is applied in the field of wireless terminals and their interlocking and unlocking with user identification cards, can solve the problems of complicated implementation process of machine-card interlocking and unlocking and the inability of wireless terminals to be unlocked, and achieves the realization of machine-card interlocking and unlocking. The locking process is flexible and simple, avoiding the inflexible unlocking method, and the machine-card interlocking process is more effective
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0051] The technical solution of the present invention will be described in more detail below with reference to the drawings and embodiments.
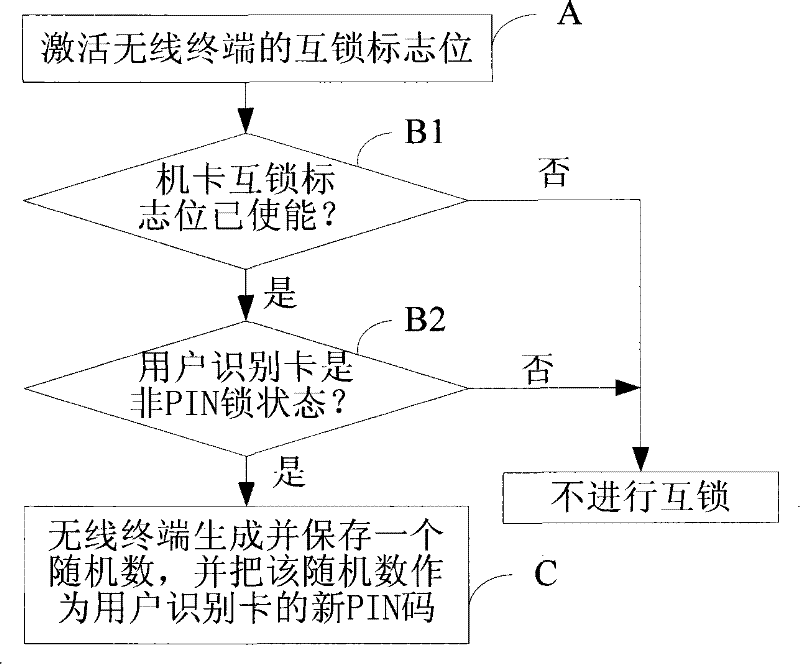
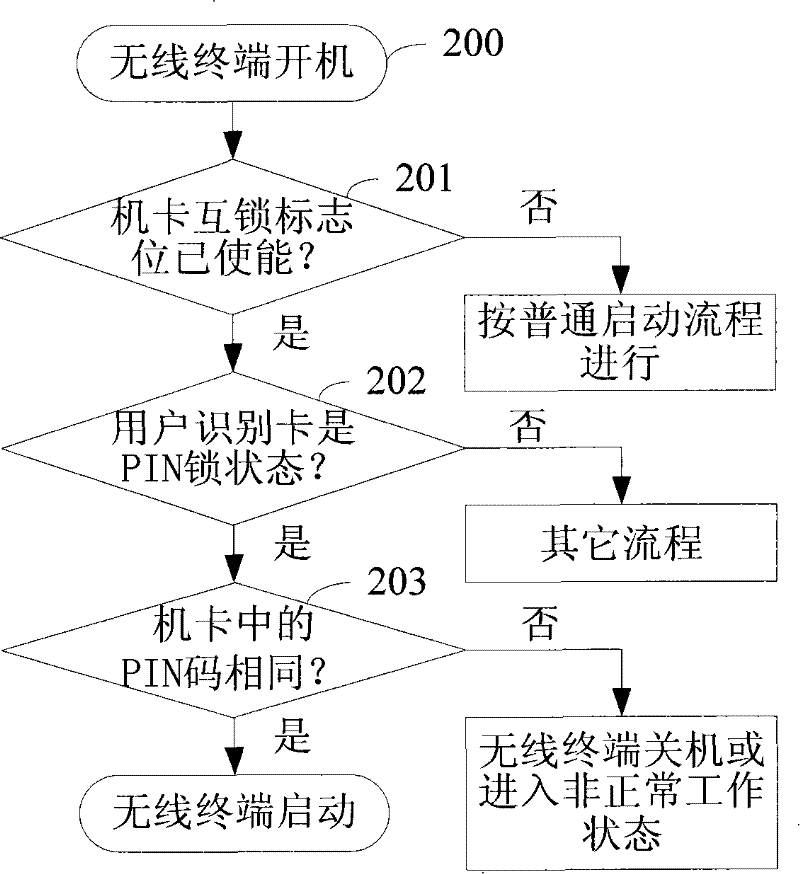
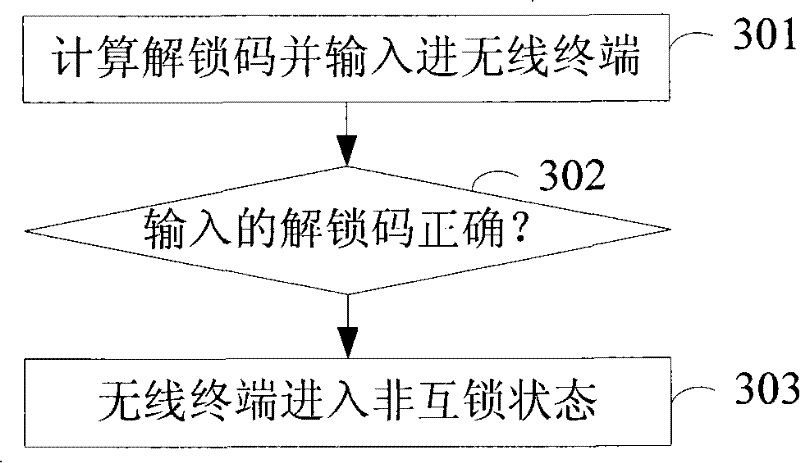
[0052]The invention provides a method for interlocking a wireless terminal and a user identification card, and an unlocking method. The basic idea of the present invention is: first add the processing code of the machine-card interlocking in the wireless terminal and set the machine-card interlocking flag; when interlocking is required, input information through the keyboard, or through the Software, or operate the wireless terminal through the CDMA (Code Division Multiple Access) air interface, etc., so that the wireless terminal enters the interlock state, as long as there is a user identification card in the wireless terminal when it is started next time, and this user If the identification card is in the "PIN (Personal Identification Number) Code Prohibited State", then the wireless terminal and the user identification card will ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com