Method for getting service key
A service key and service technology, applied in the field of authentication, can solve the problems of reducing network security, operator losses, user and NAF threats, etc., to eliminate security risks, reduce losses, improve service reliability and network security. Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
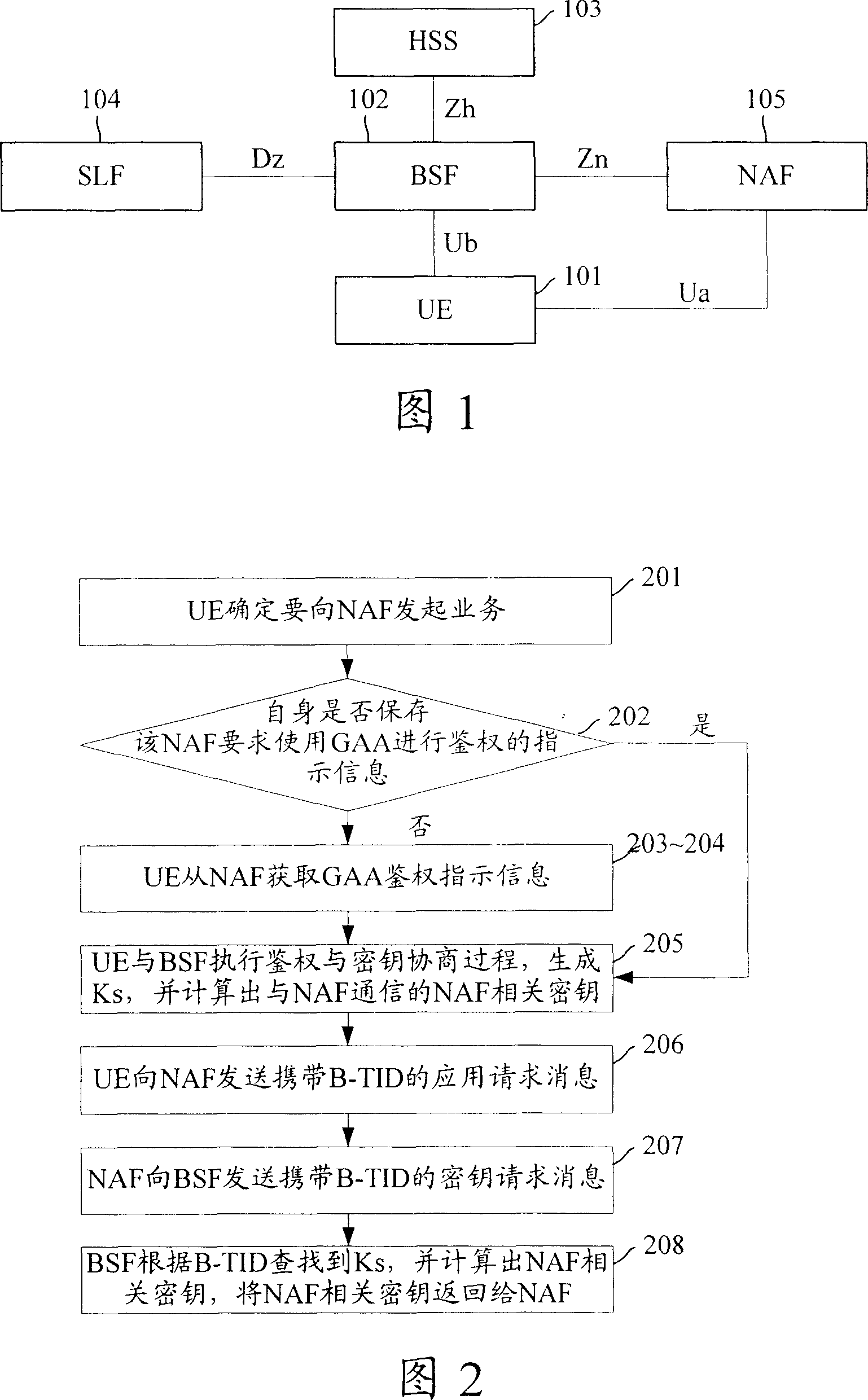
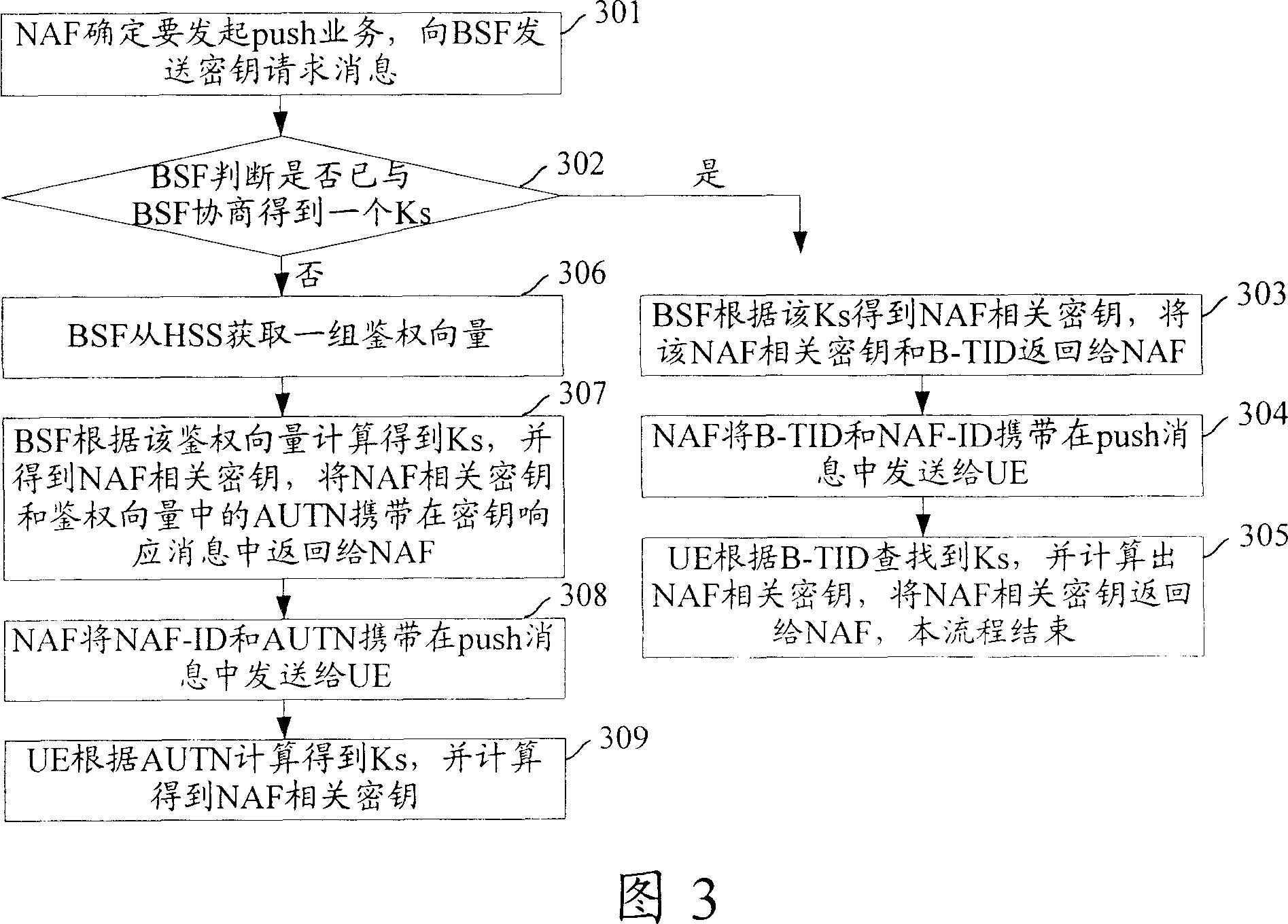
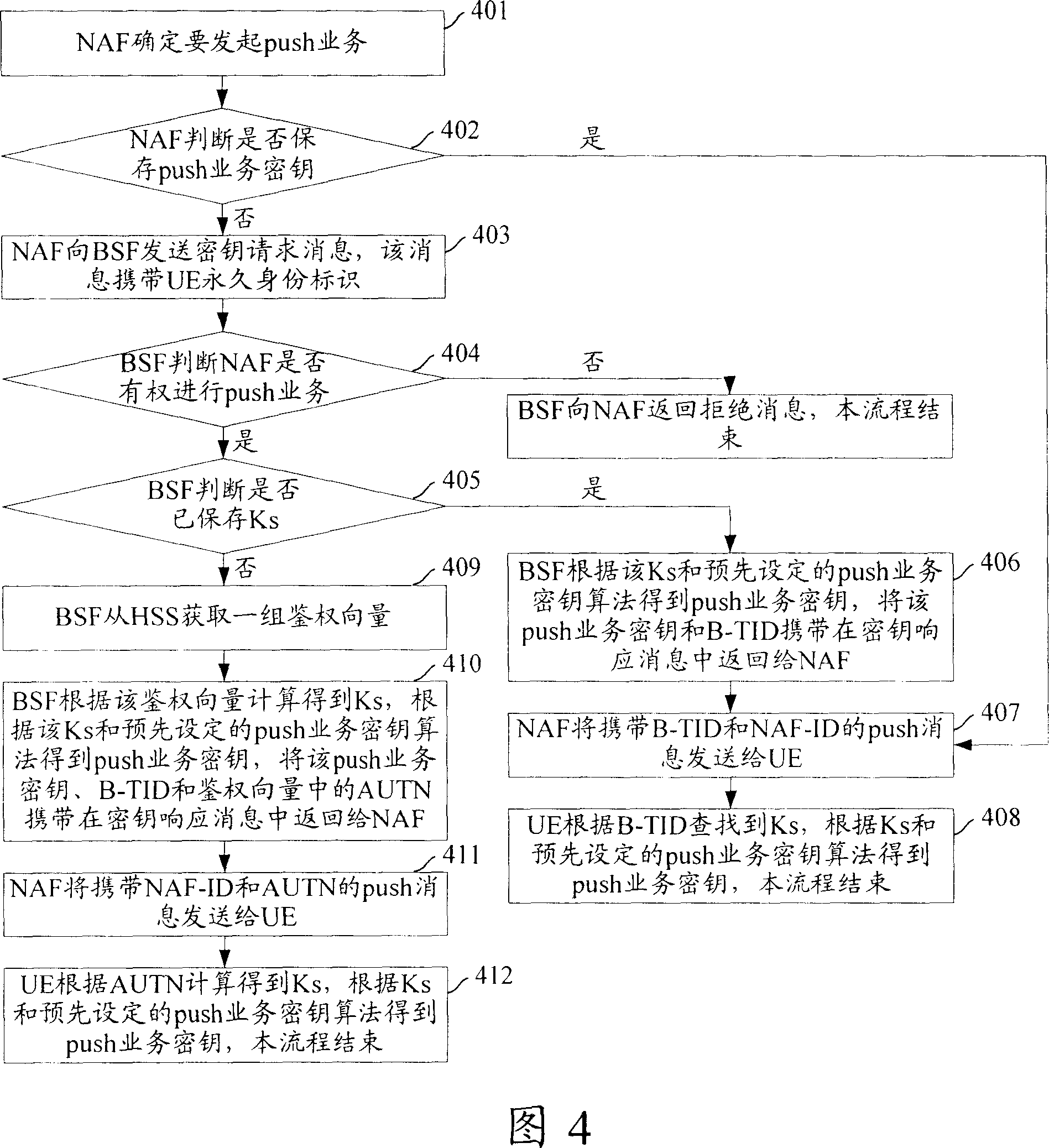
[0057] The present invention will be further described in detail below in conjunction with the drawings and specific embodiments.
[0058] Fig. 4 is a flowchart of obtaining the service key of the push service initiated by NAF under GAA according to the first embodiment of the present invention. As shown in Fig. 4, the specific steps are as follows:
[0059] Step 401: NAF determines to initiate a push service to a certain UE.
[0060] Step 402: NAF judges whether it saves the push service key corresponding to the UE, if yes, execute step 407; otherwise, execute step 403.
[0061] If the NAF stores the push service key, the NAF associates the push service key with the UE's B-TID, and at the same time stores the corresponding relationship between the B-TID and the UE's permanent identity.
[0062] If the NAF has initiated a Push message to the UE, the NAF may save the push service key corresponding to the UE.
[0063] Step 403: NAF sends a key request message to BSF, which carries U...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com