Access control method for prepaid users in cluster communication system
A trunking communication and prepaid technology, applied in access restriction, prepaid telephone system, telephone communication, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
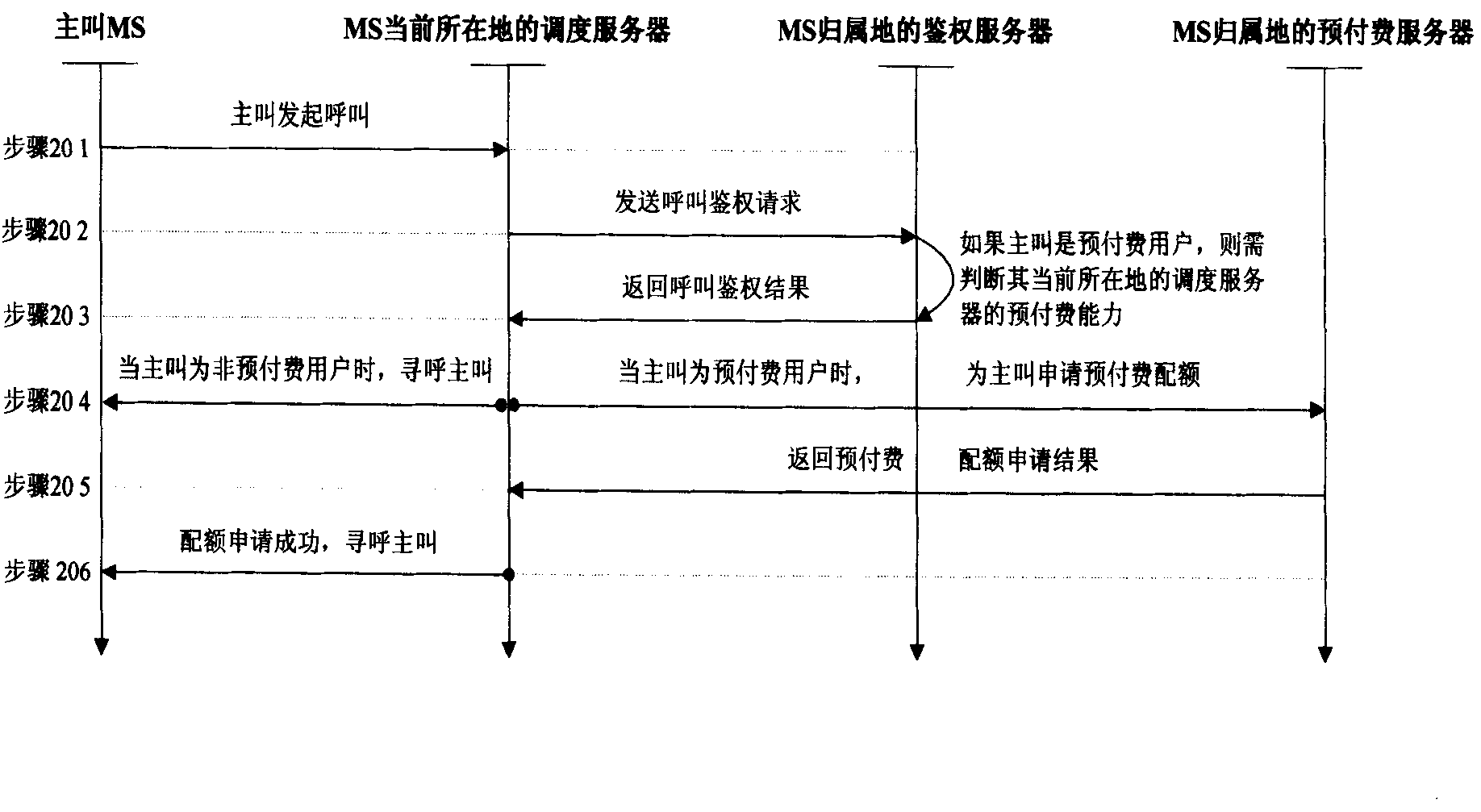
[0066] Embodiment 1: The access control process when a prepaid user acts as a calling party, such as figure 2 As shown, it mainly includes the following steps:
[0067] Step 201: The calling party initiates a call.
[0068] Step 202: The dispatching server at the caller's current location sends a call authentication request to the authentication server at the caller's home location, and the request includes the authentication information of the caller; The message exchange between the dispatching server of the caller and the authentication server at the caller's home location needs to be forwarded through the authentication server at the current location of the caller, and even needs to be forwarded through other authentication servers in the middle.
[0069] Step 203: The authentication server in the caller's place of origin authenticates the caller. After the caller has passed the basic call authentication process, the authentication server also checks whether the caller i...
Embodiment 2
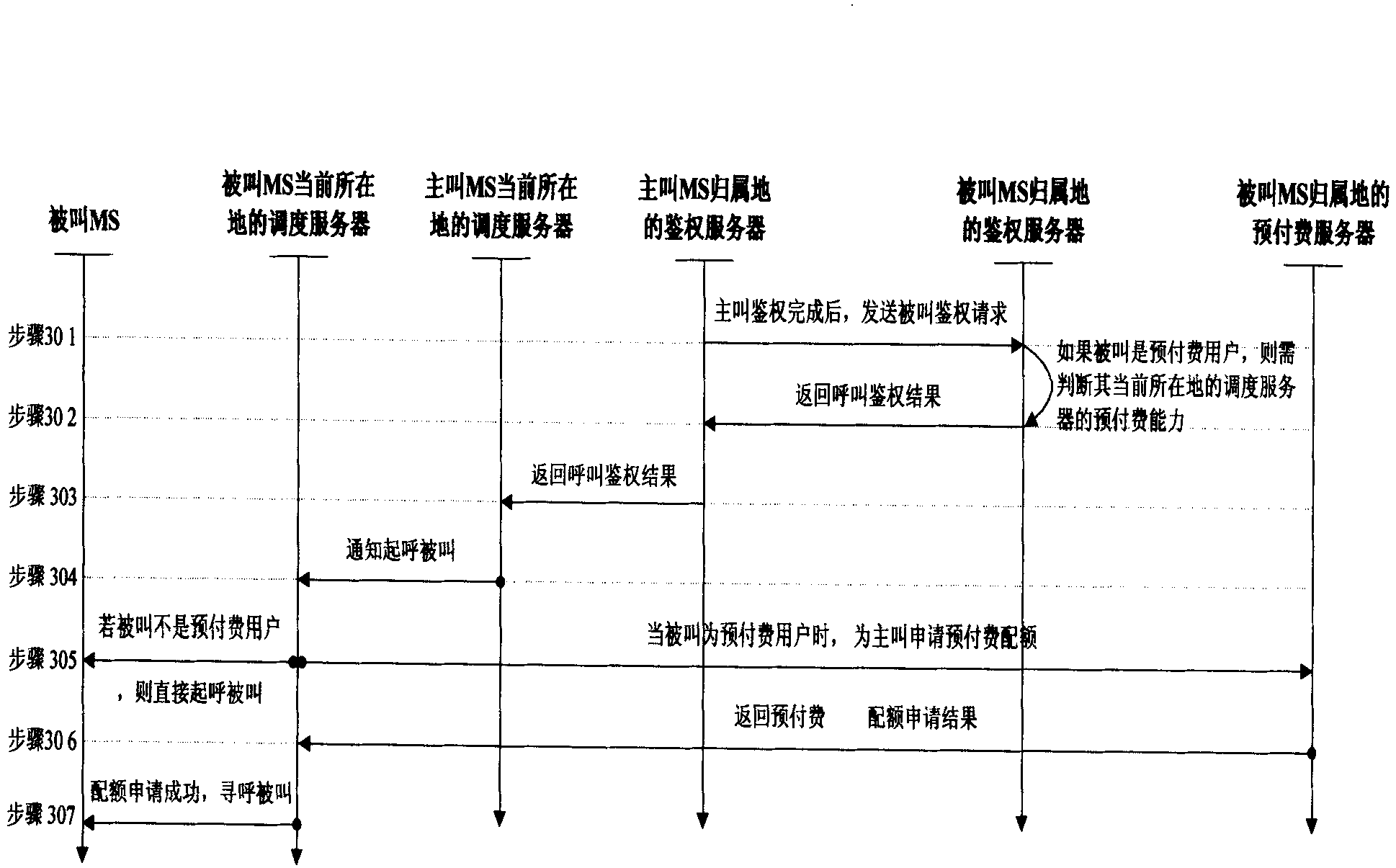
[0074] Embodiment 2: Called access control under single call (one call one) situation, such as image 3 As shown, it mainly includes the following steps:
[0075] Step 301: If the origin of the calling party and the called party are the same, the authentication server in the originating area of the calling party will authenticate the called party when completing the authentication of the calling party; The authentication server at the origin of the calling party needs to notify the authentication server at the origin of the called party to authenticate the called party.
[0076] Step 302: The authentication server in the called home region authenticates the called party. After the called party passes through the basic call authentication process, the authentication server will judge whether the called party is a prepaid subscriber. If not, the called party will authenticate the called party. If yes, the authentication server will further judge whether the dispatch server at...
Embodiment 3
[0082] Embodiment 3: Called access control under the situation of group call (one call with multiple), such as Figure 4 As shown, it mainly includes the following steps:
[0083] Step 401: If the origin of the calling group and the called group are the same, the authentication server in the calling place will authenticate the called group when completing the calling authentication. If the calling and called groups If the attributions are inconsistent, the authentication server at the calling location needs to notify the authentication server at the called location to authenticate the called group.
[0084] Step 402: The authentication server at the place where the called group belongs authenticates the group and group members. After the group and group members have passed the basic authentication process, the authentication server needs to determine the Whether it is a prepaid user, if not, the corresponding group member has passed the authentication, if yes, it is necessary...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com