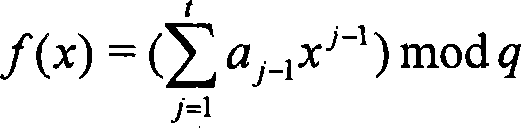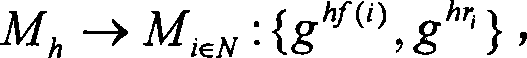Authenticating Ad Hoc group cipher key negotiation protocol
A technology of group keys and protocols, applied in the public key and key distribution of secure communication, can solve problems such as inability to guarantee security services
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0063] specific implementation
[0064] A preferred embodiment of the present invention is described in detail as follows in conjunction with accompanying drawing: the Ad Hoc group key agreement protocol that can be authenticated is:
[0065] 1. Negotiation initialization phase (IKA Initial key Agreement)
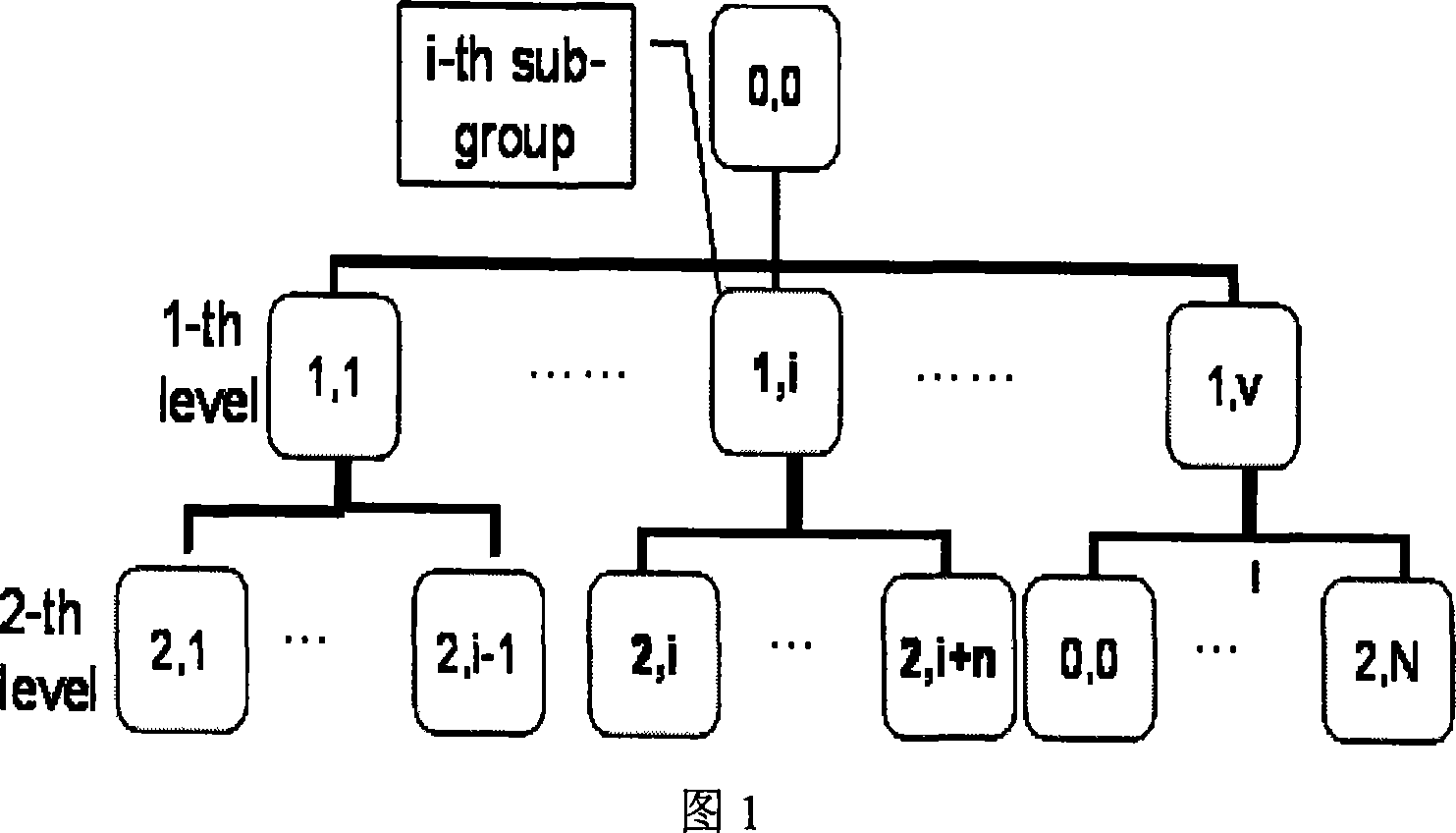
[0066] It can be seen from FIG. 1 that the height of the key tree proposed by the present invention is two layers, the root node has more than two children, and the first leaf node has more than two children. Before each key agreement, each Ad Hoc group must elect a group control node responsible for organizing the order of key agreement. The key agreement process is as follows:
[0067] First, each member chooses a random number r i , b i ∈[1,q-1] and a key x i ; Then, publish the public key y i and parameter c i , τ i : c i = H ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com