Method and device for detecting scanning attack
A technology for detecting scans and devices, which is applied to detect scan attacks, detect scan attack devices, detect scan attack devices based on monitoring the number of attacks within a certain period of time, and detect scan attack fields based on monitoring the number of attacks within a certain period of time. It can solve problems such as high complexity and high time precision requirements, and achieve the effect of low implementation cost, simple implementation method and reduced difficulty.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0032] Referring to Fig. 4, before describing each embodiment of the present invention in detail, it is necessary to briefly explain the format of the ICMP address unreachable message: generally, each message shown in Fig. 4 is included in an ICMP address unreachable message content:
[0033] IP packet header, including: source IP address (SIP) and destination IP address (DIP);
[0034] ICMP message header, for the unreachable message, its type (Type) value is 3; when the code (Code) value is 2, 3, it indicates that the protocol is unreachable and the port is unreachable respectively;
[0035] Original IP packet header, including: original source IP address (0_SIP), original destination IP address (0_DIP) and original protocol (0_Protocol);
[0036] Original IP UDP message header, including: source port (0_SPORT) and destination port (0_DPORT) of the original IP message.
[0037] Embodiments of the first aspect:
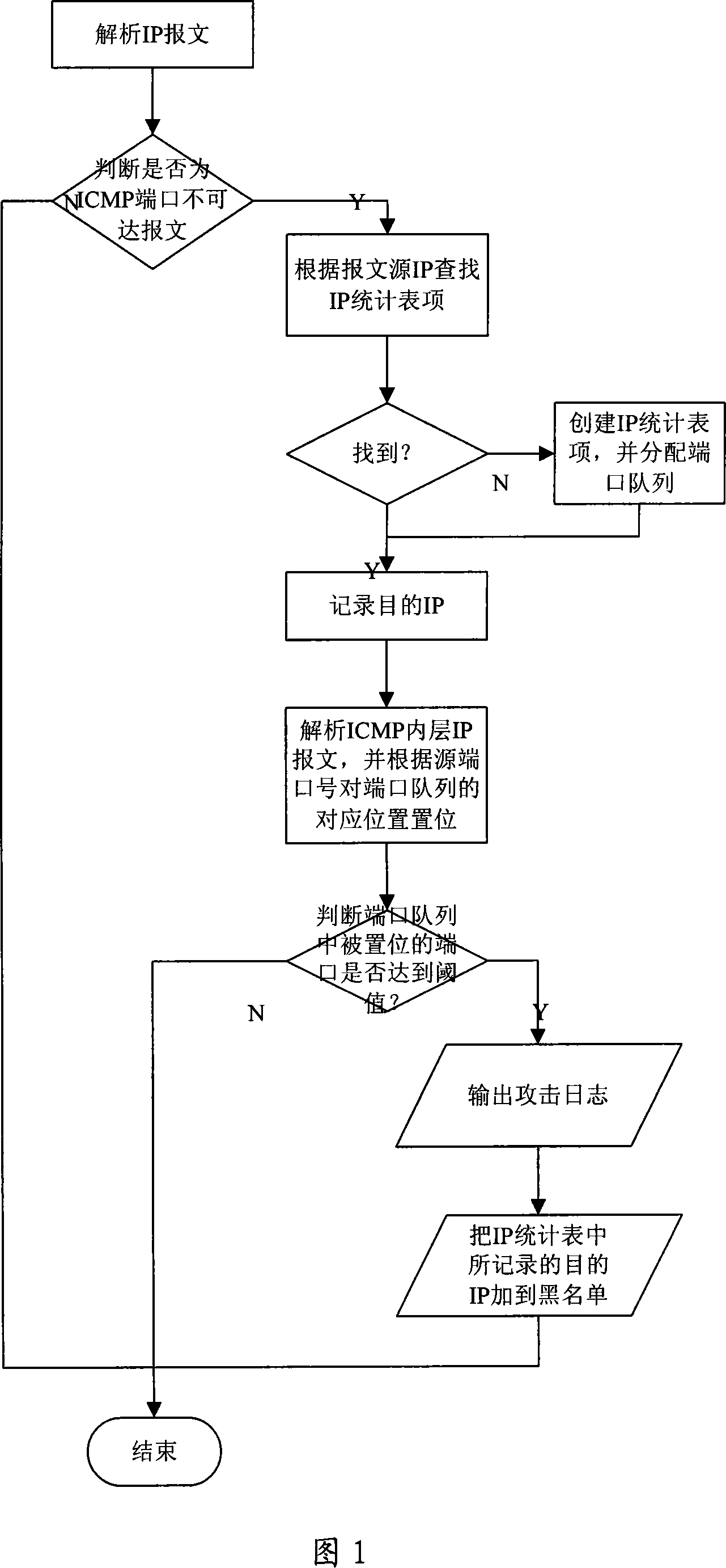
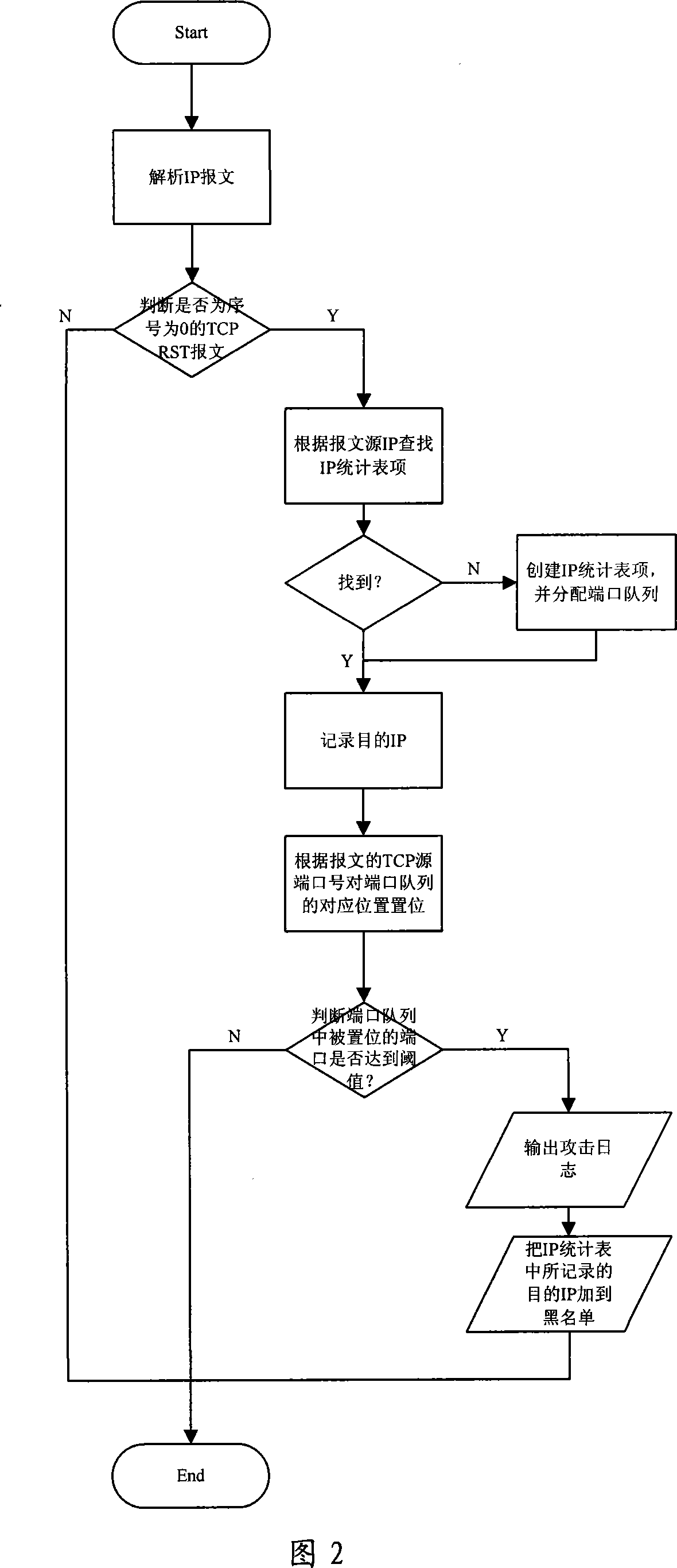
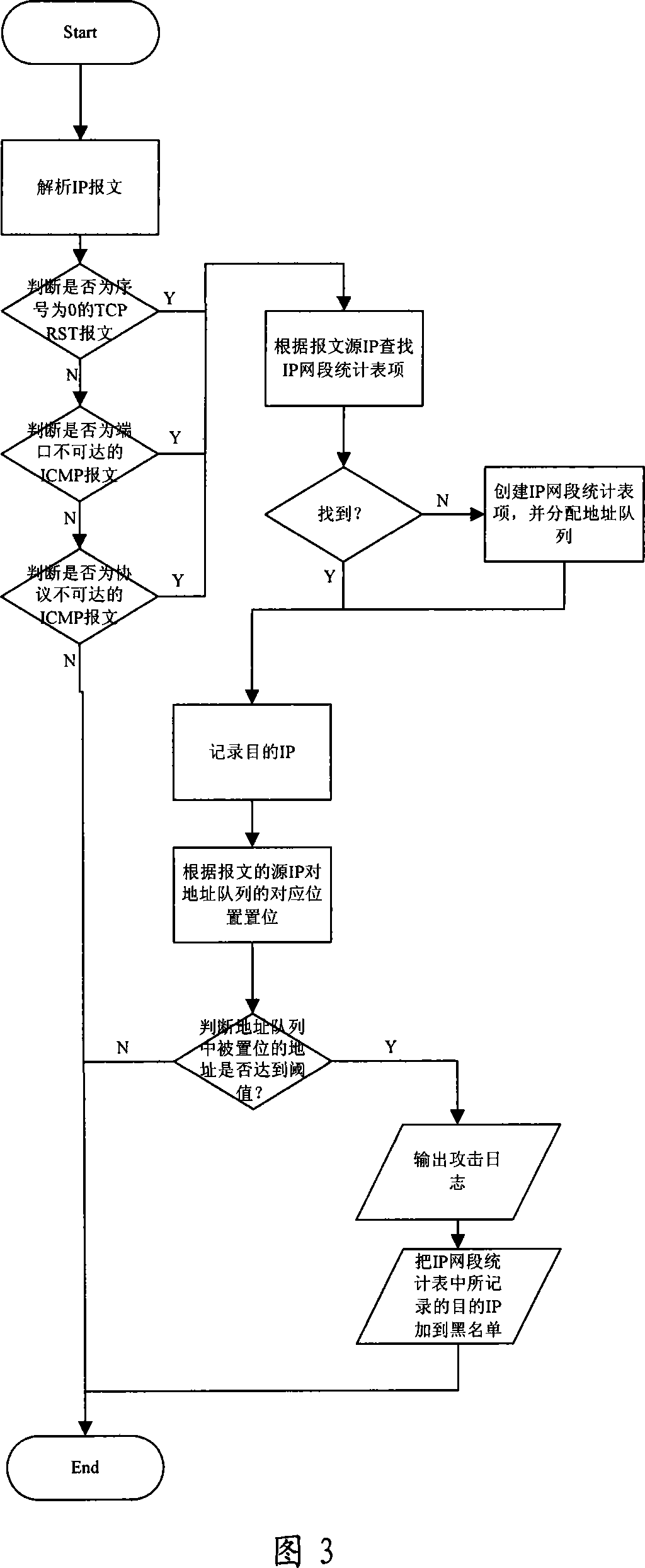
[0038] Referring to FIG. 1 , it is an example of a detection...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com