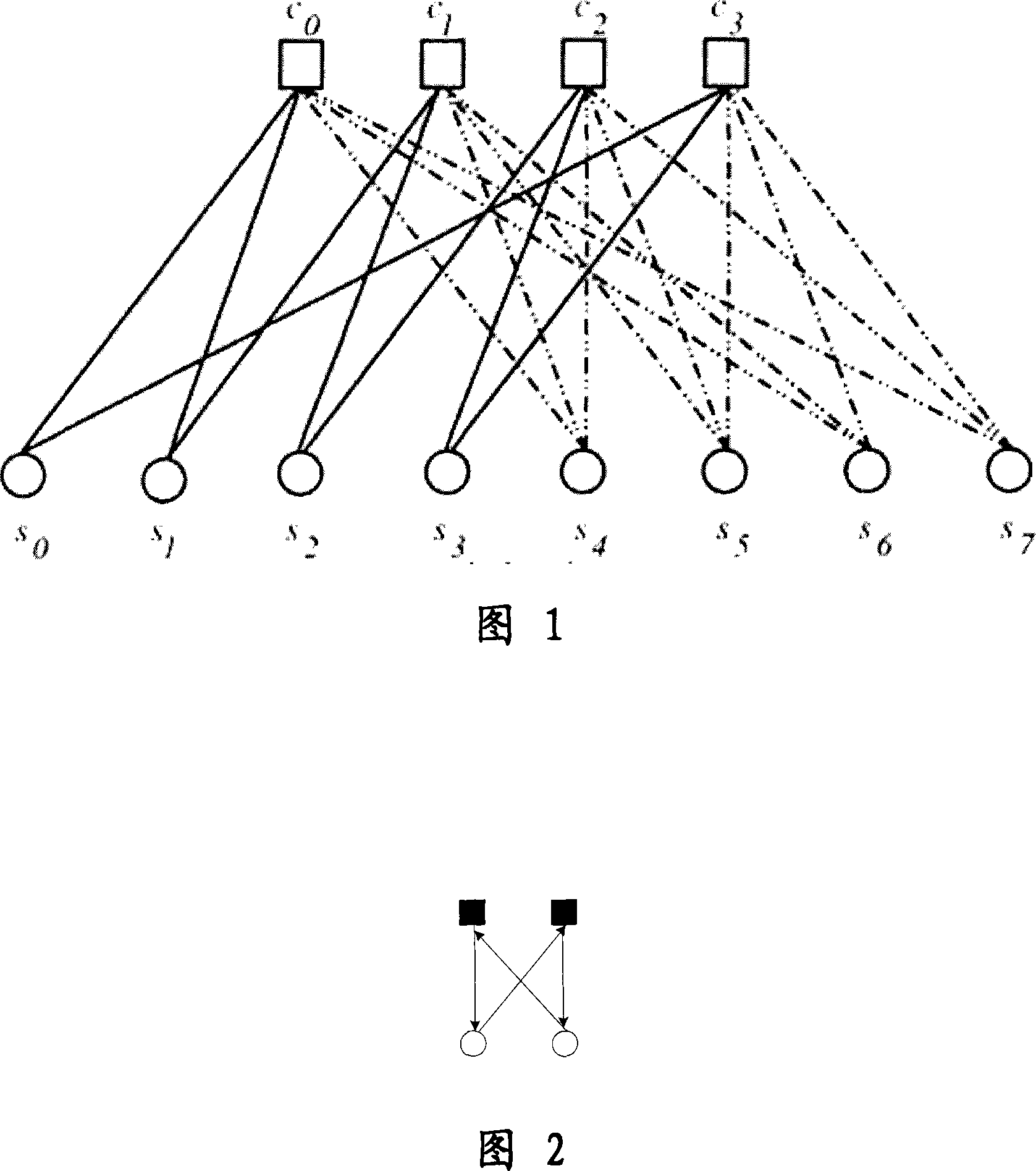
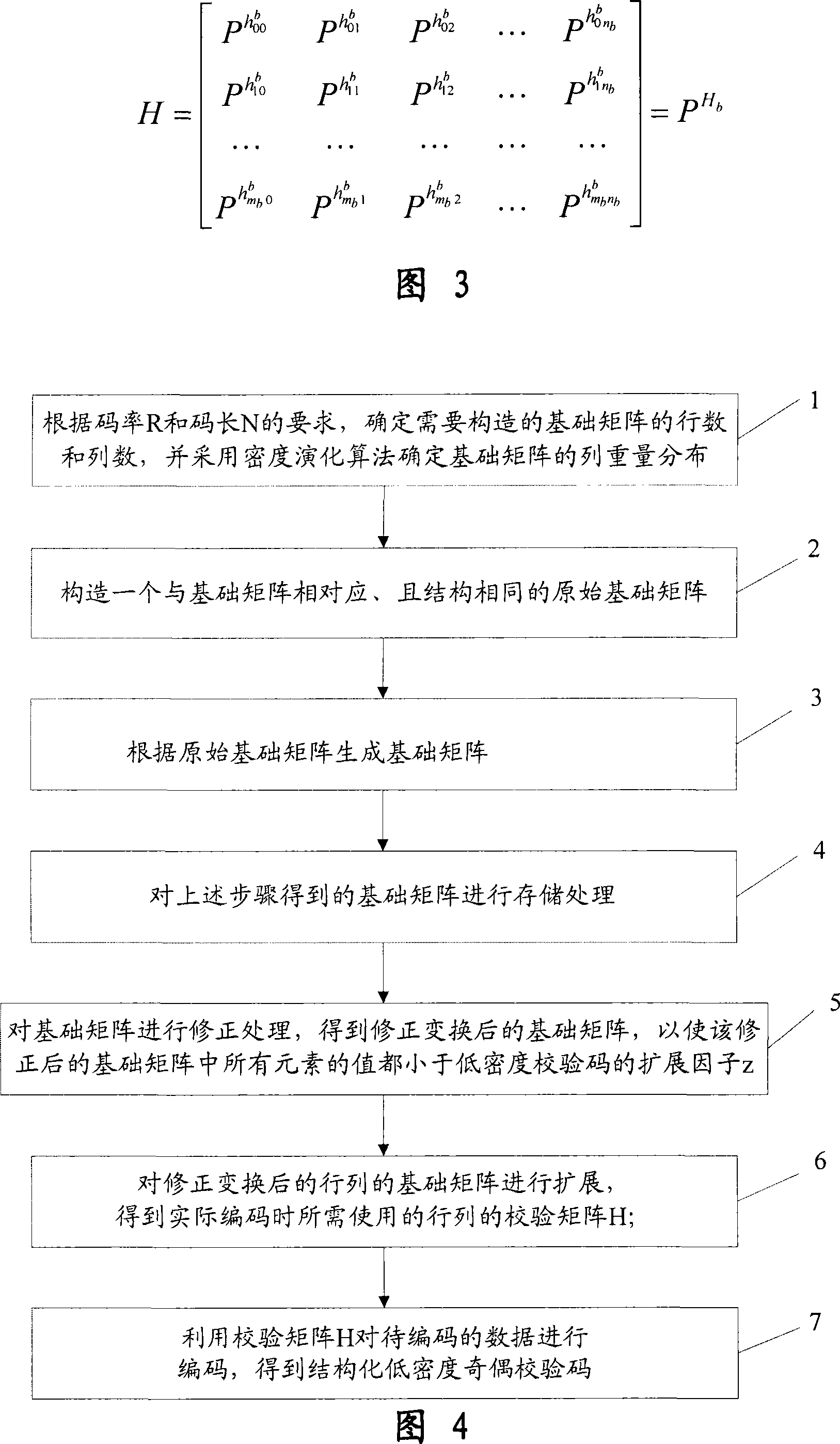
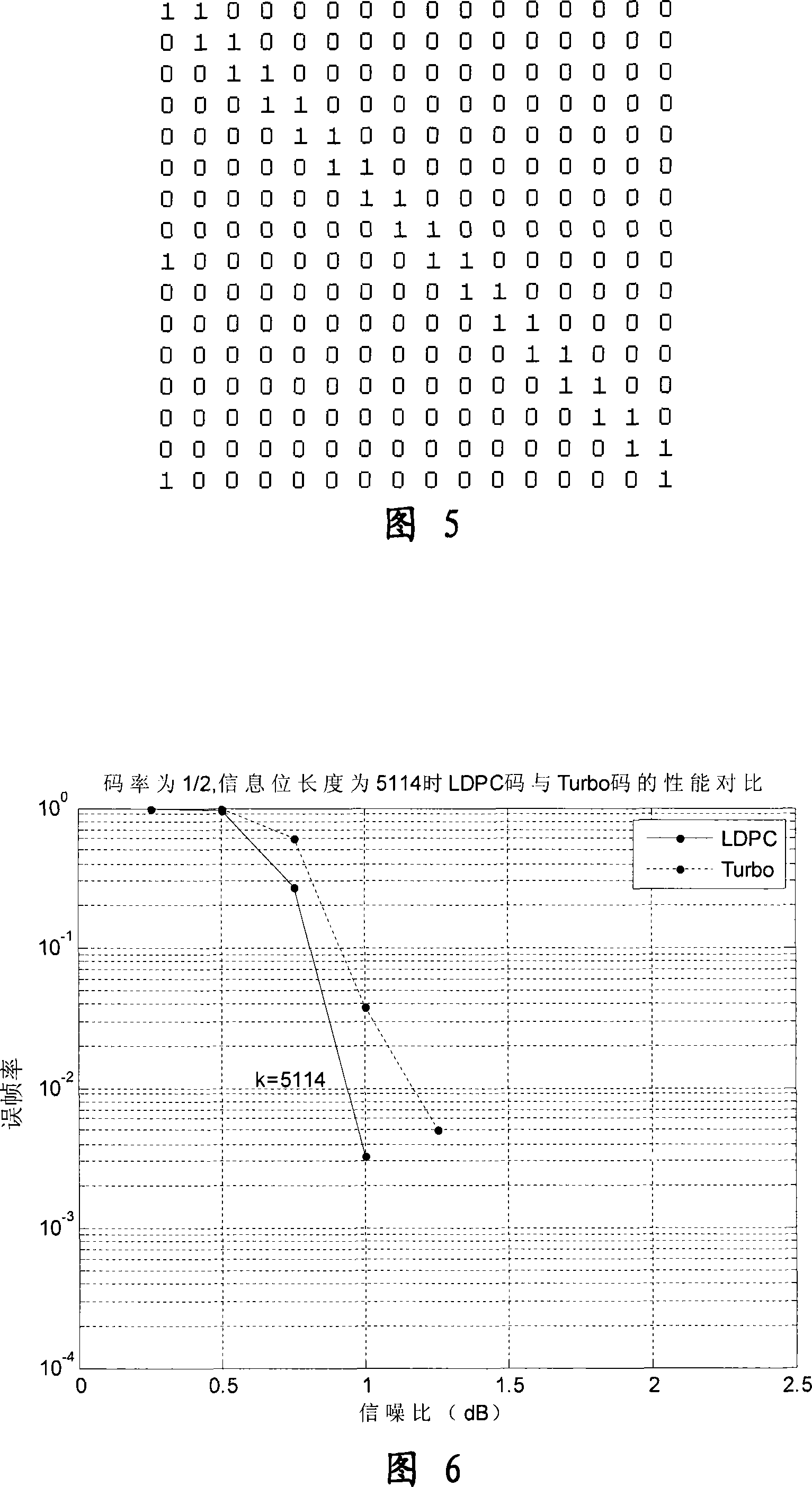
Method of encoding structured low density check code
A coding method and check code technology, which are applied in error detection coding using multi-bit parity bits, error correction/detection using block codes, digital transmission systems, etc., and can solve the problem that the shortest loop period is not well solved problem, to achieve good general applicability, good frame error rate performance, and the effect of reducing storage space
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0043] In order to make the purpose, technical solution and advantages of the present invention clearer, the specific steps, features and performance of the method of the present invention will be further described in detail below in conjunction with the accompanying drawings and embodiments.
[0044] Referring to Fig. 3, the encoding method of structured low-density check code of the present invention is introduced, and the method comprises the following steps:
[0045] Step 1, according to the requirements of code rate R and code length N, determine the fundamental matrix H that needs to be constructed b the number of rows m b and number of columns n b , and use the density evolution algorithm to determine the fundamental matrix H b column weight distribution; wherein, the calculation formula of the code rate R is: R=K / N, the length of the check bit M is: M=N-K, in the formula, the length K of the information bit, the code length N and the length of the check bit The leng...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com