Method based on access control list category
An access control list and algorithm technology, applied in digital transmission systems, data exchange networks, electrical components, etc., can solve the problems of reduced search efficiency, impacted efficiency, low search efficiency, etc., to save search time and save storage resources Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
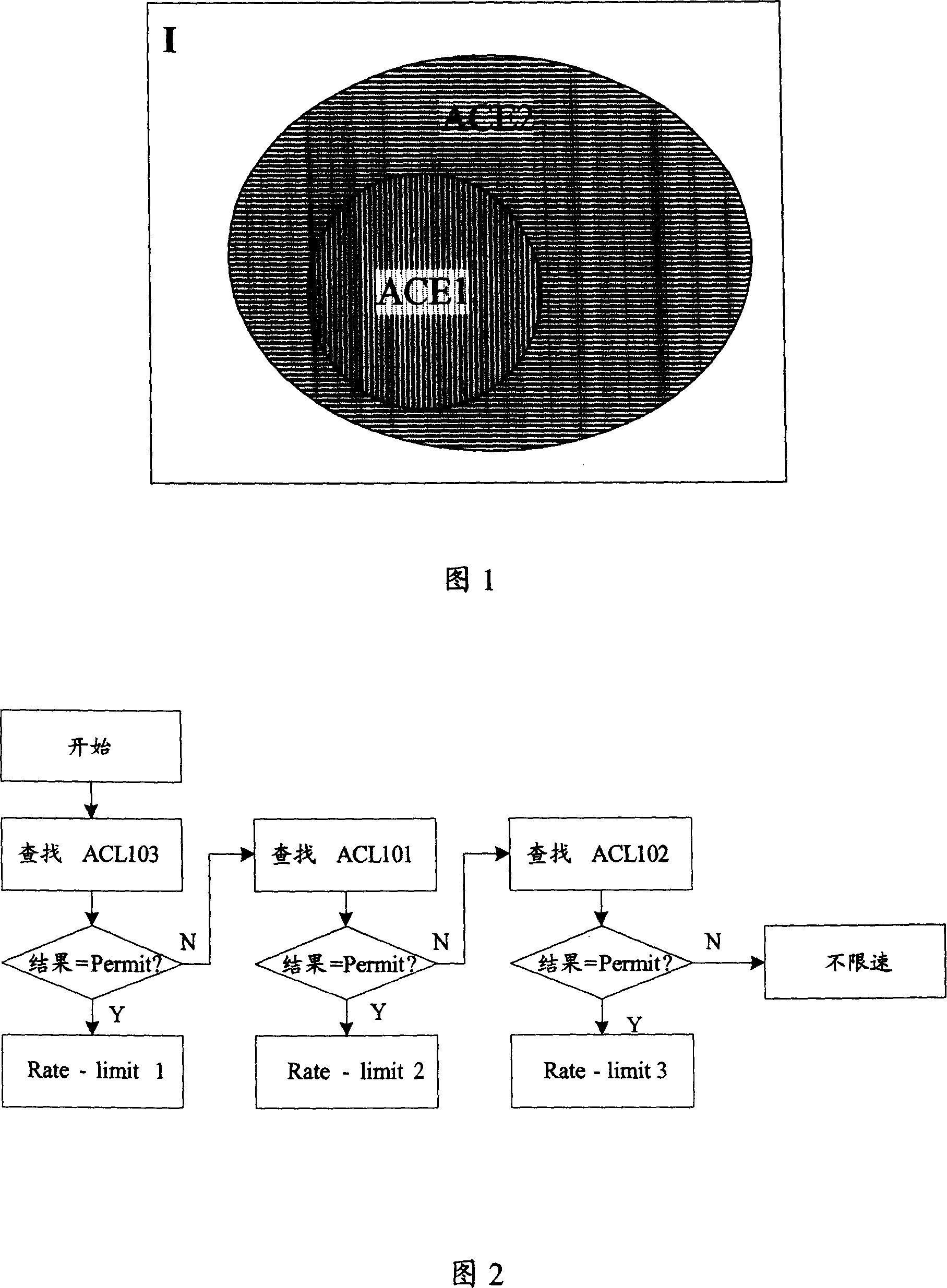
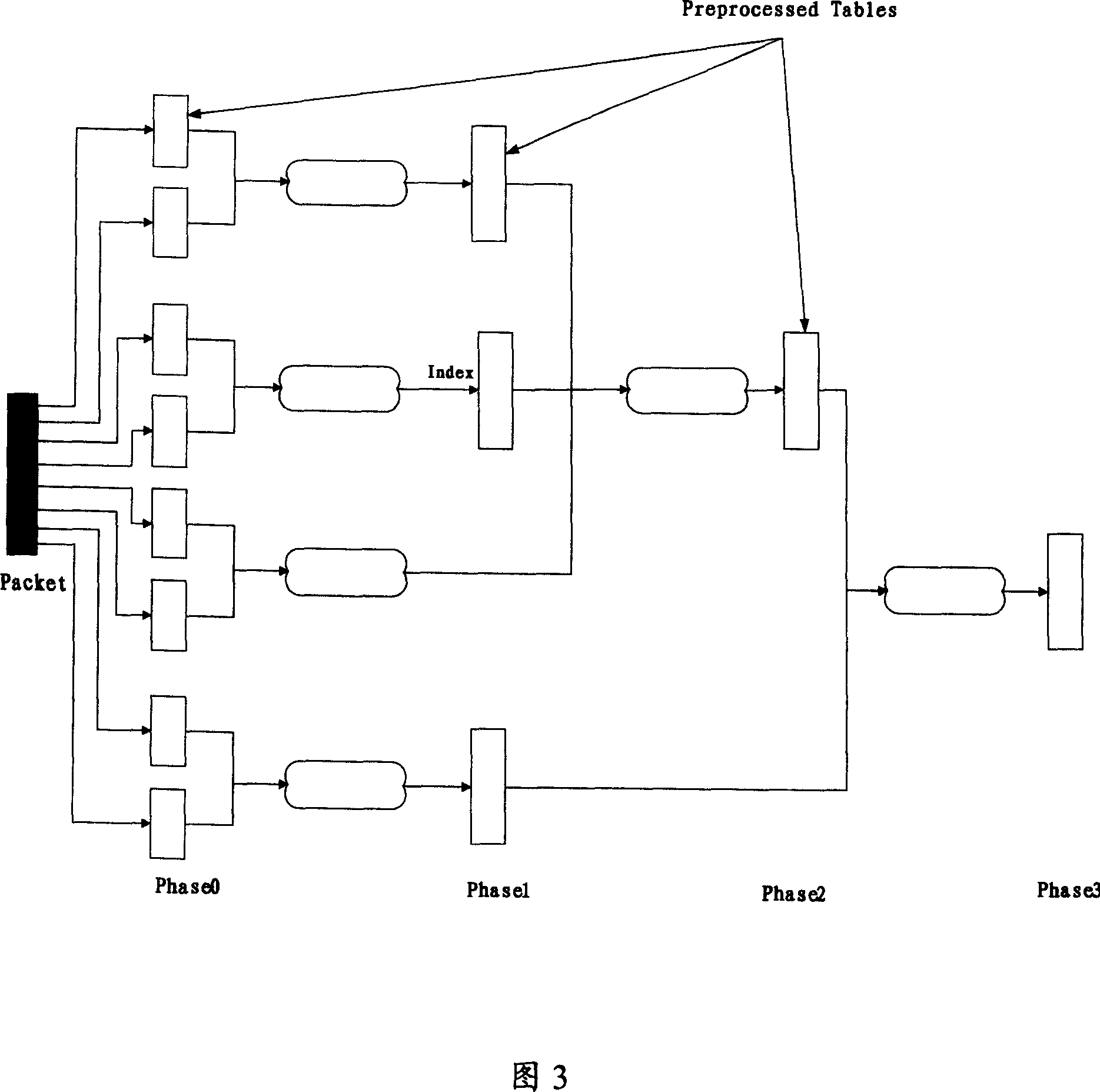
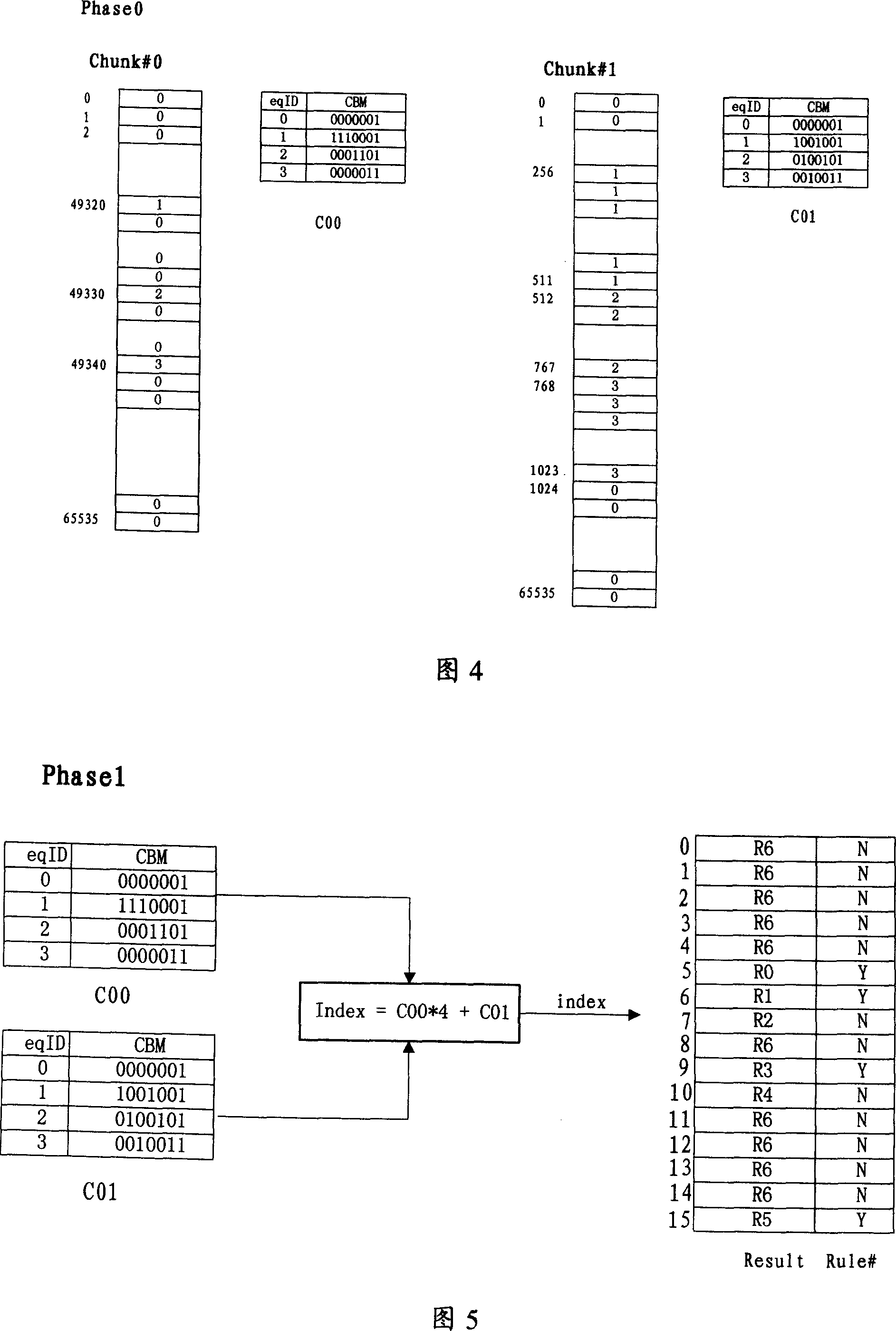
[0070] According to the analysis, after a specific packet enters a network element, the result is always unique after each classification. That is to say, when two identical packets enter a network element, their processing should be exactly the same. Set of class behaviors. If there is a method that can obtain all the behaviors to be done after a classification search, that is, the behavior set, then this method must be the most efficient, and the time complexity is O(n).
[0071] The difference between the present invention and the existing RFC algorithm is that all ACLs form an RFC table, and the final query result of the table is an action set, and the action set can include: whether the message is allowed to pass through, what kind of restriction is adopted Speed policy and what kind of NAT conversion and so on. In this way, when a packet enters a network element, only one search is required to obtain the set of behaviors that the packet should adopt.
[0072] The pre...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com