Network resource integration access method based on registration and authentication
An access method and network resource technology, applied in the field of network resource access, can solve problems such as difficult control of UDDI, uncontrollable service, non-support of registration and query of other users and personalized application resources, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0028] The invention relates to publishing, searching and positioning of network resources, especially in a large-scale network environment, the publishing, searching and positioning of network resources including users and services across regions, departments and trust domains.
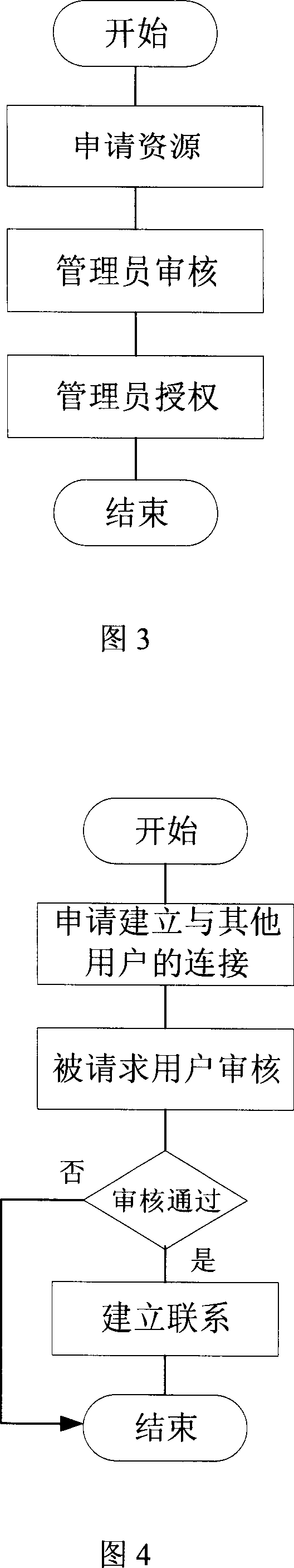
[0029] The invention introduces a method for publishing, discovering, locating and accessing network resources including contacts, business applications and common services.
[0030] The invention adopts a method of unified registration, unified authentication and unified management to provide credible release, discovery, positioning and service functions for resources and services in the private networks of e-government affairs, e-commerce and other industries.
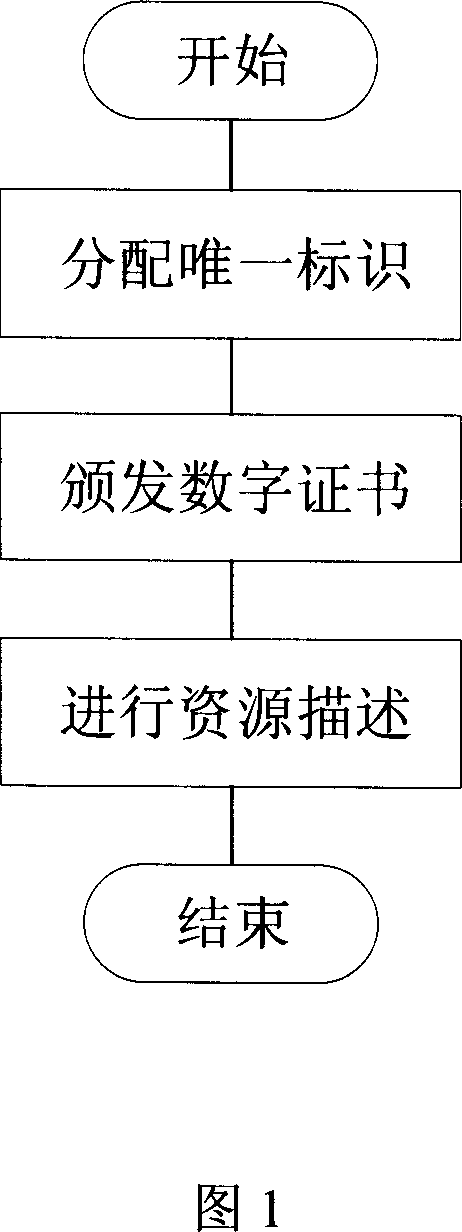
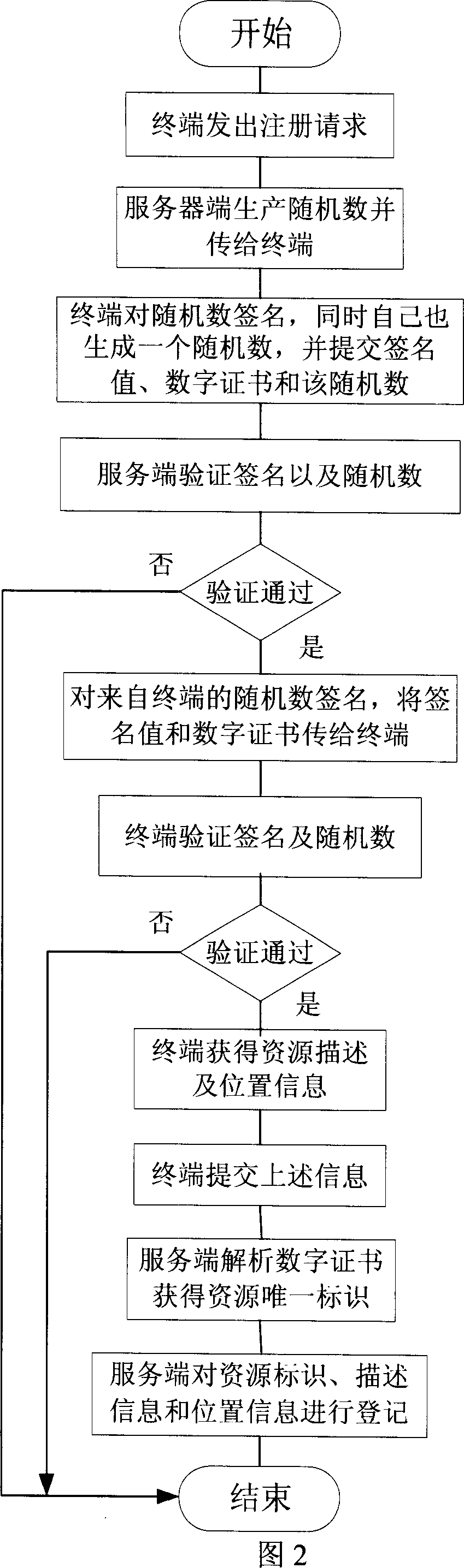
[0031] This method uniformly marks all kinds of network resources and services, releases them through trusted registration, for users to query and apply for resources, and can provide users with active push of resources and resource status a...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com