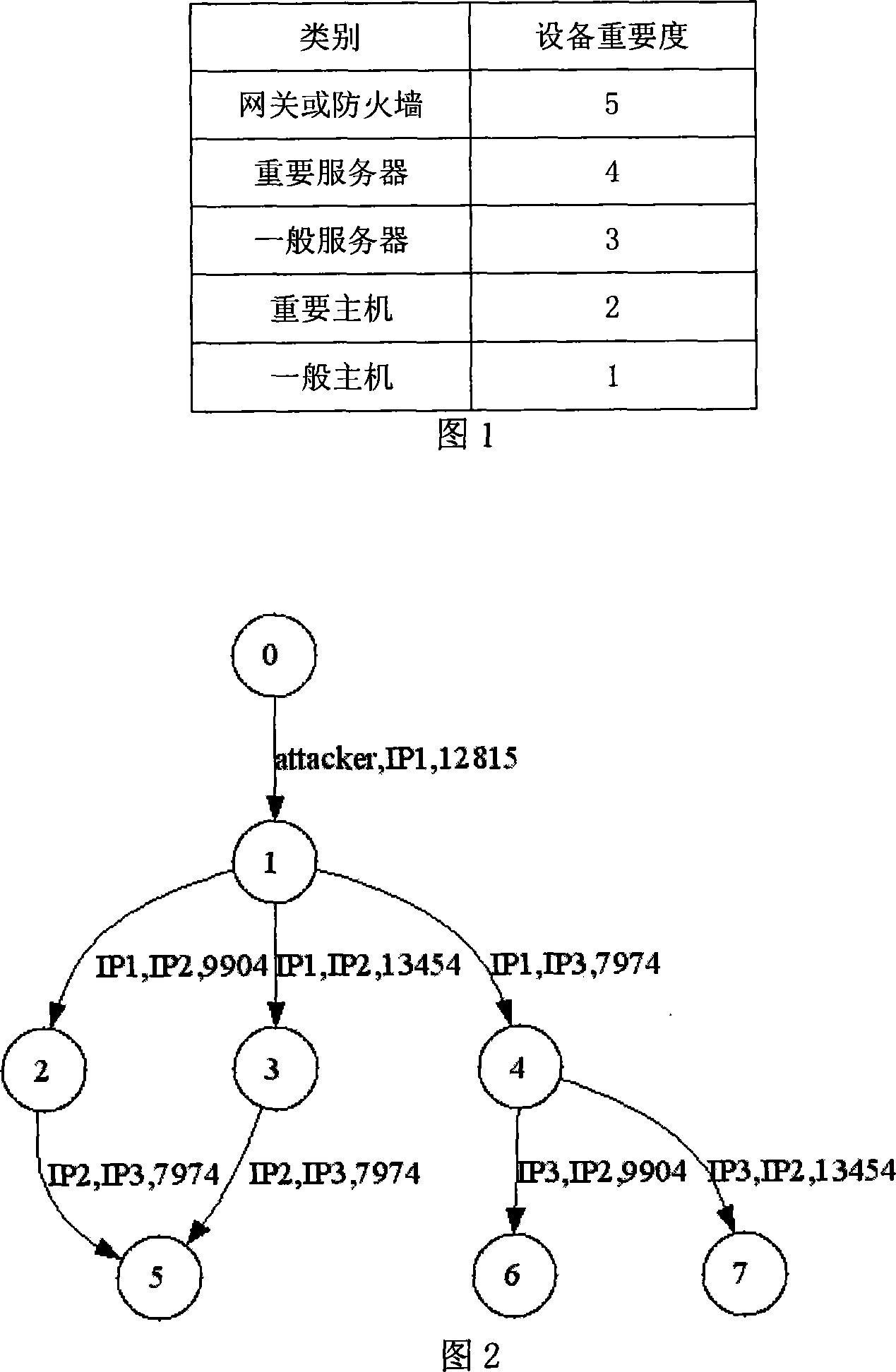
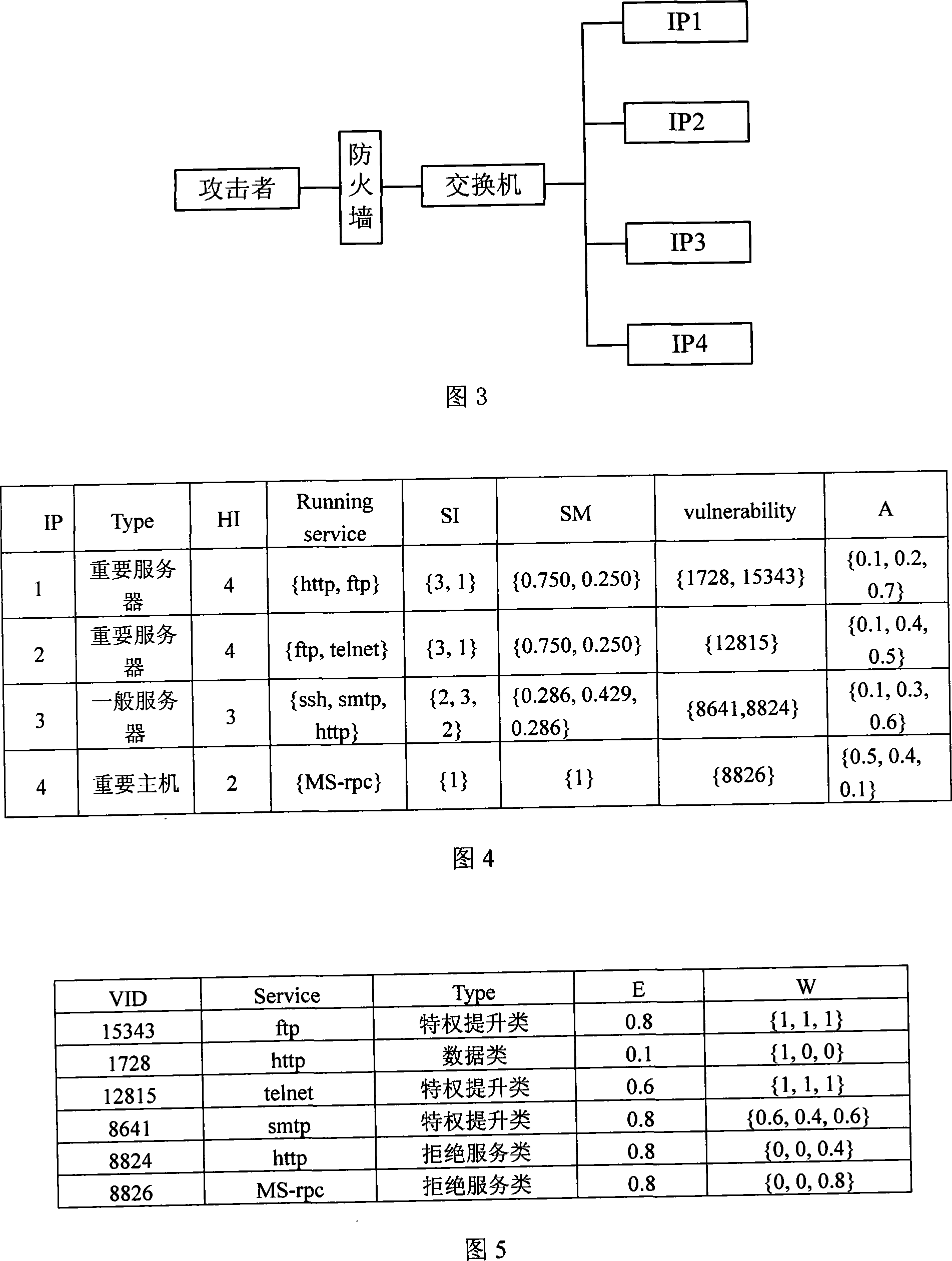
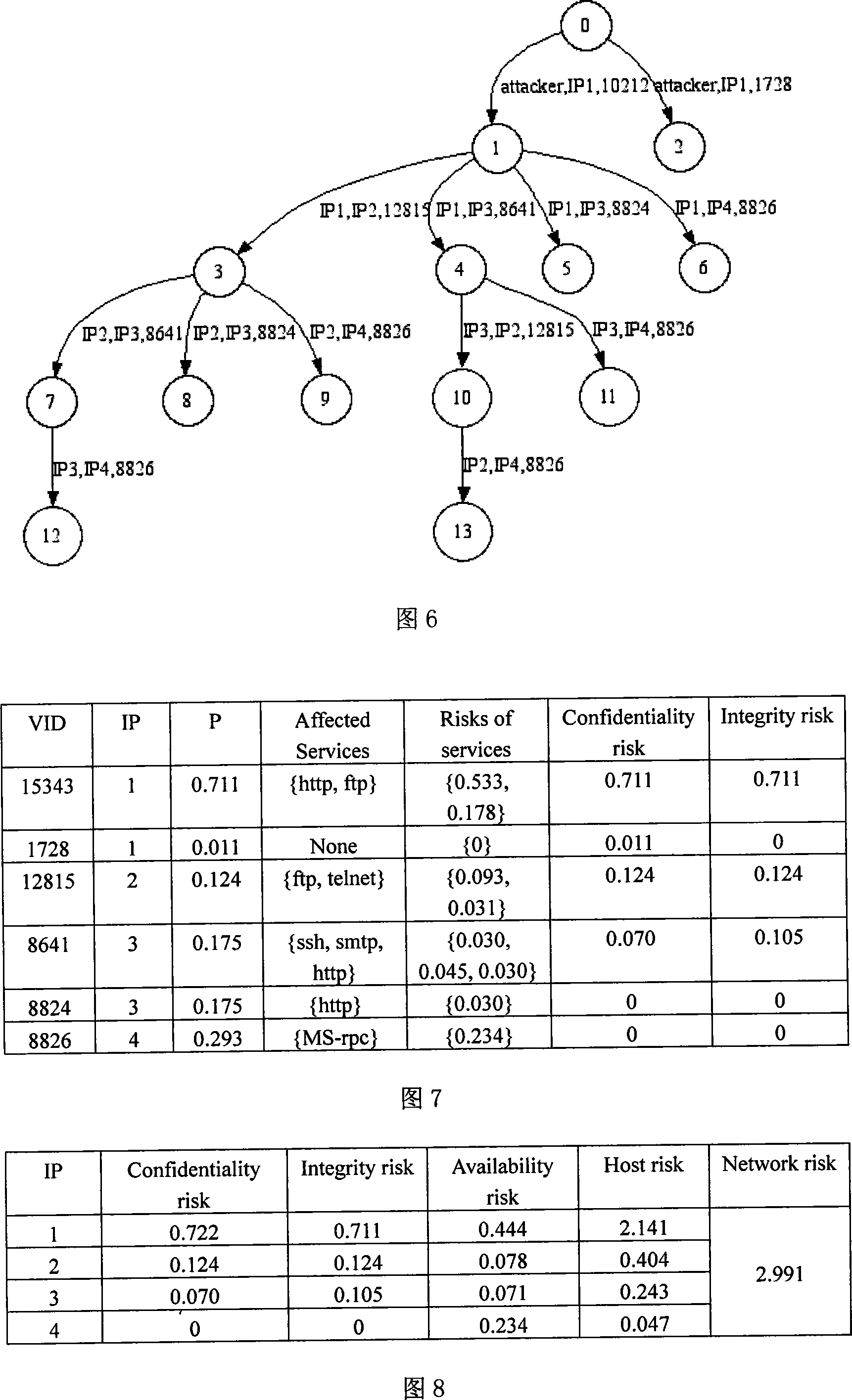
Network risk analysis method
A risk analysis and network technology, applied in the field of quantitative assessment technology for network risks, can solve the problems of being attacked, not considering security requirements, inaccurate assessment results, etc., to achieve the real effect of assessment results
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0032] The present invention is described in more detail below in conjunction with accompanying drawing example:
[0033] In order to realize the purpose of the present invention, the present invention provides a series of definitions at first:
[0034] Definition 1 (Attack Complexity). Attack complexity is a measure of how easy it is for an attacker to successfully exploit a weakness.
[0035] Definition 2 (Vulnerabilities). Vulnerabilities are represented by the following quintuples (IP, VID, W, E, P). Among them, IP is the name of the host where the vulnerability is located; VID is the number of the vulnerability in the Bugtraq vulnerability database; the degree of impact of the vulnerability on the security of the host is a triplet W=(W C , W I , W A ), W C , W I and W A are respectively the impact coefficients of the vulnerability on the confidentiality, integrity and service availability of the host; E is the attack complexity of the vulnerability; P is used to sto...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com