Mobile ad hoc authentication method and system
A technology of mobile self-organization and authentication method, applied in the field of communication
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
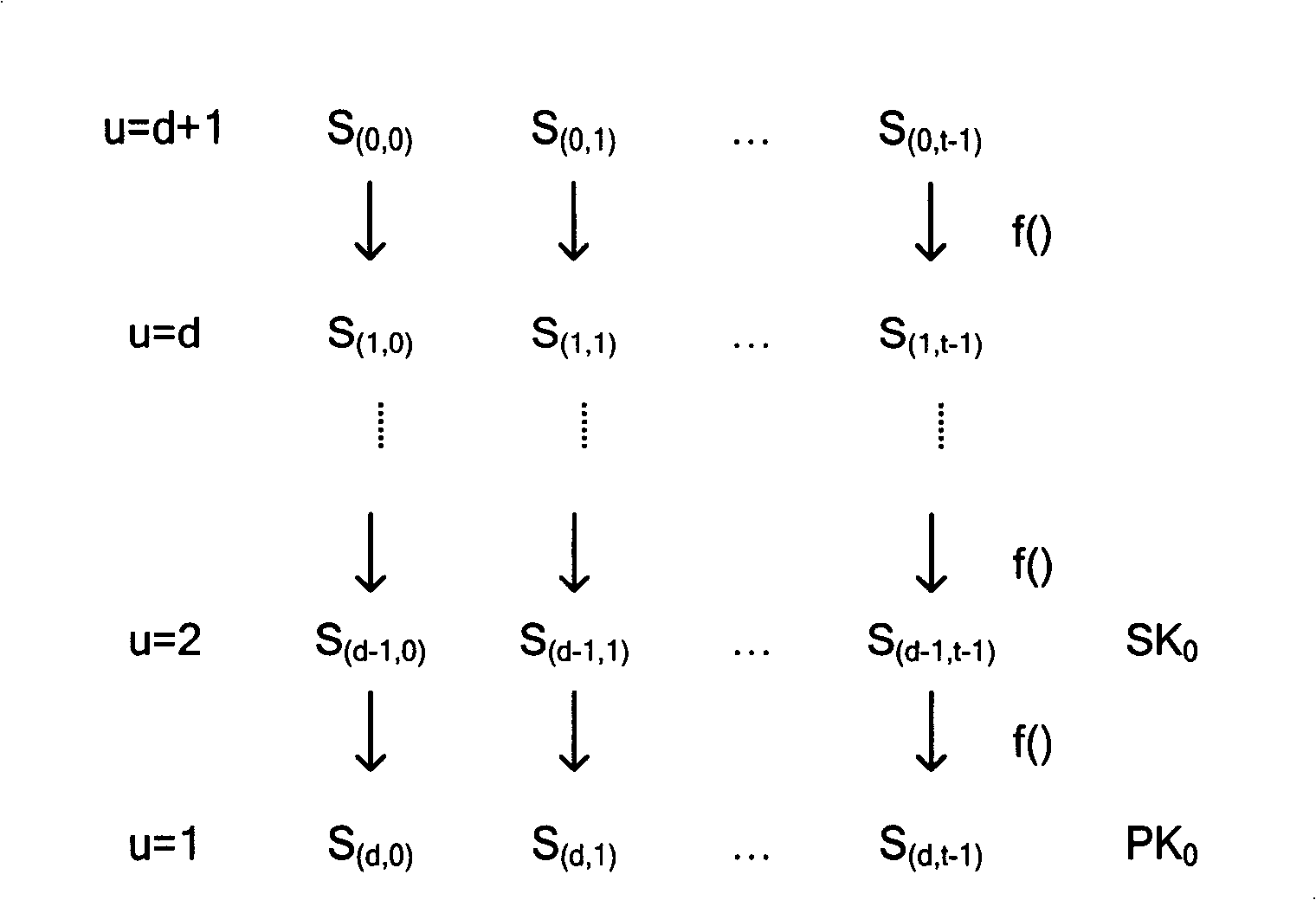
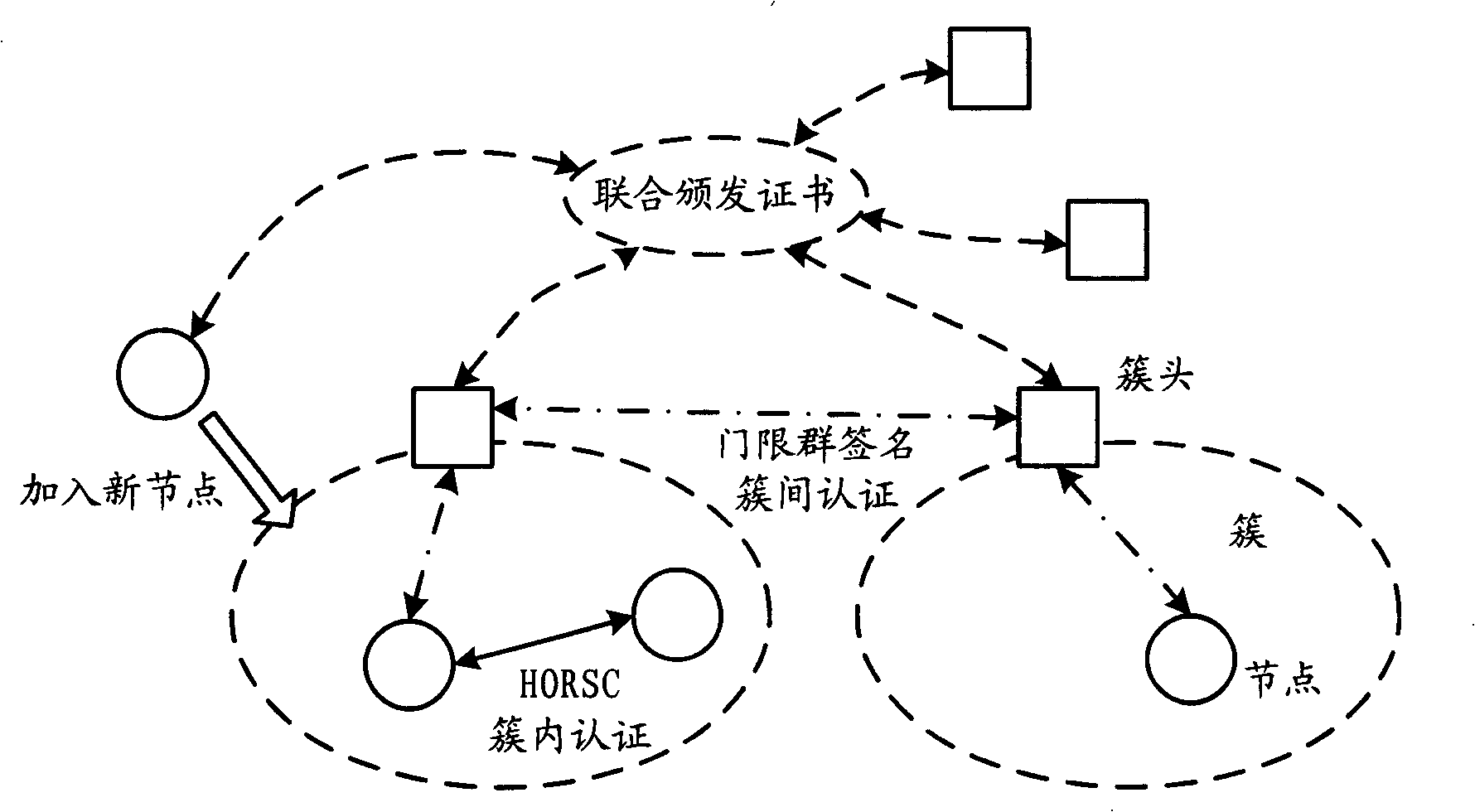
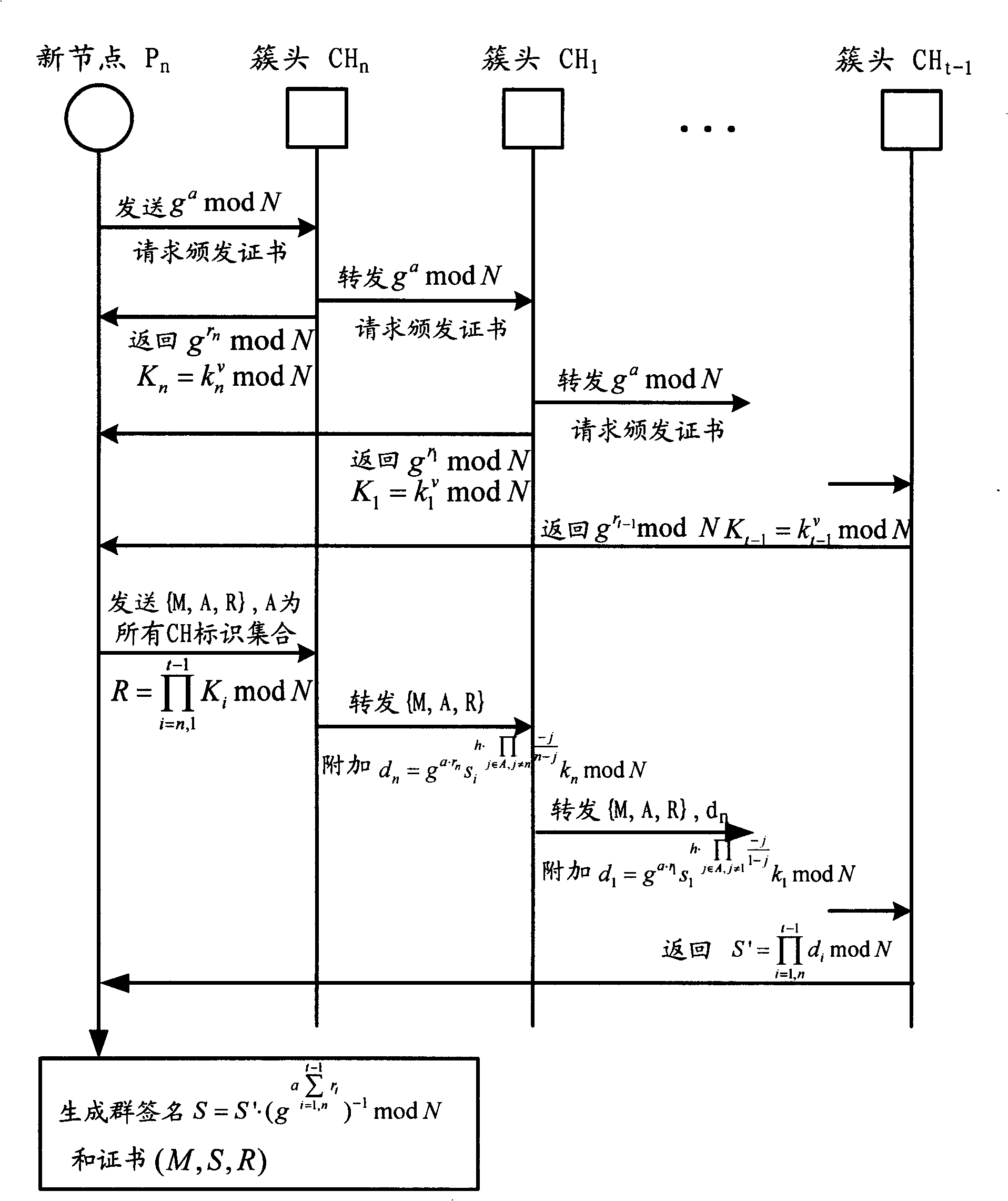
[0073] When a new node joins, a specified number of cluster head nodes jointly issue a certificate to the new node according to their subkeys and according to the new threshold group signature protocol. cluster heads, and then interact with the new node according to the protocol, and obtain the certificate of the new node through distributed computing and communication, which can be authenticated in the same way according to the protocol;
[0074] Nodes perform identity authentication and inter-cluster communication through the new threshold group signature protocol based on certificates, and identity authentication can be implemented between nodes with certificates. The authentication method is consistent with the traditional threshold group signature;
[0075] In the cluster, the nodes only need to use the Hash Obtained Random Subset (HORSC) protocol for identity authentication and intra-cluster communication. This protocol can efficiently implement flat authentication, fully...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com