Method, device and network system for secure algorithm negotiation
A security algorithm and algorithm technology, applied in the field of communication, can solve the problem of inability to negotiate a security algorithm
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0030] Embodiments of the present invention will be described in detail below with reference to the accompanying drawings.
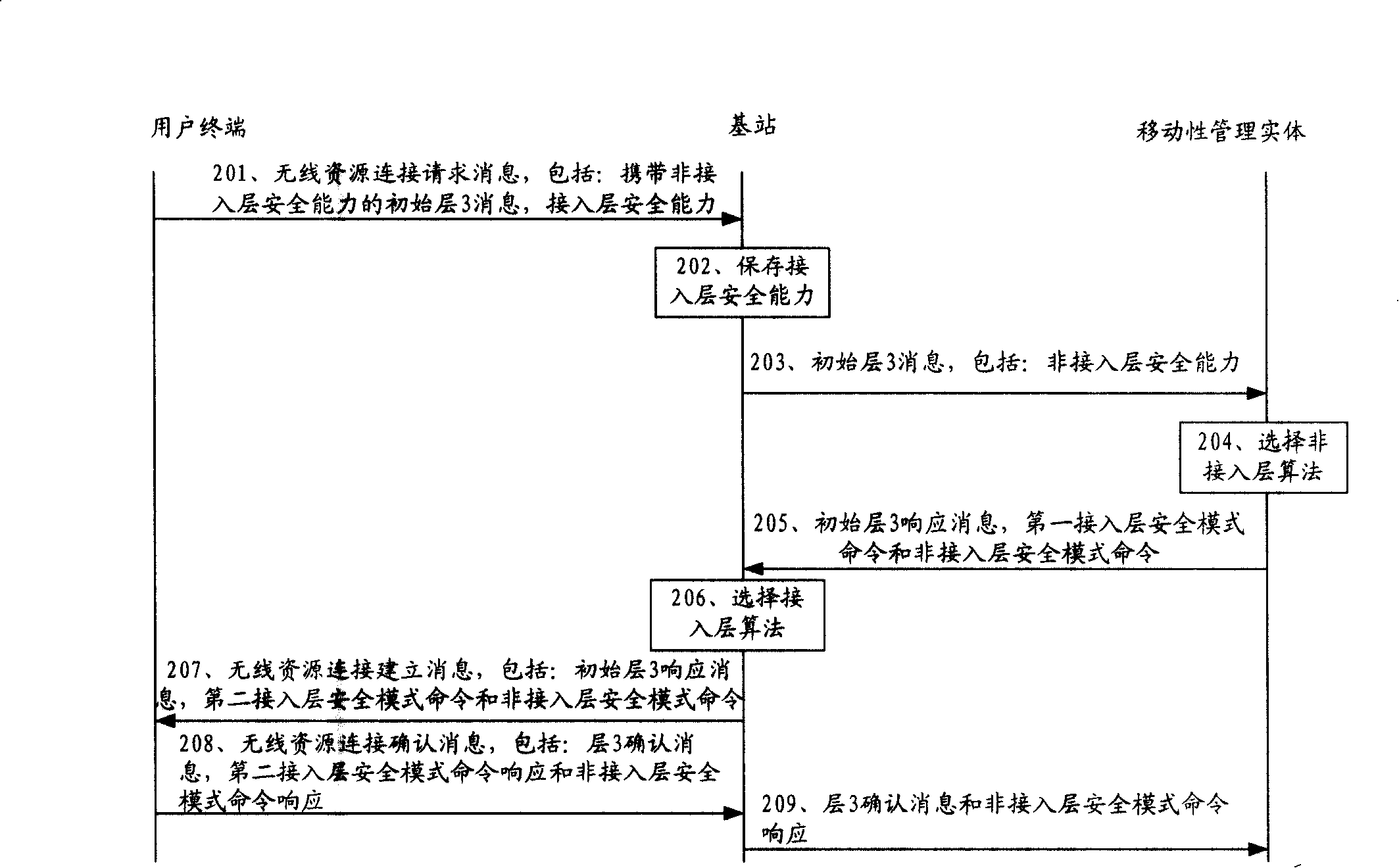
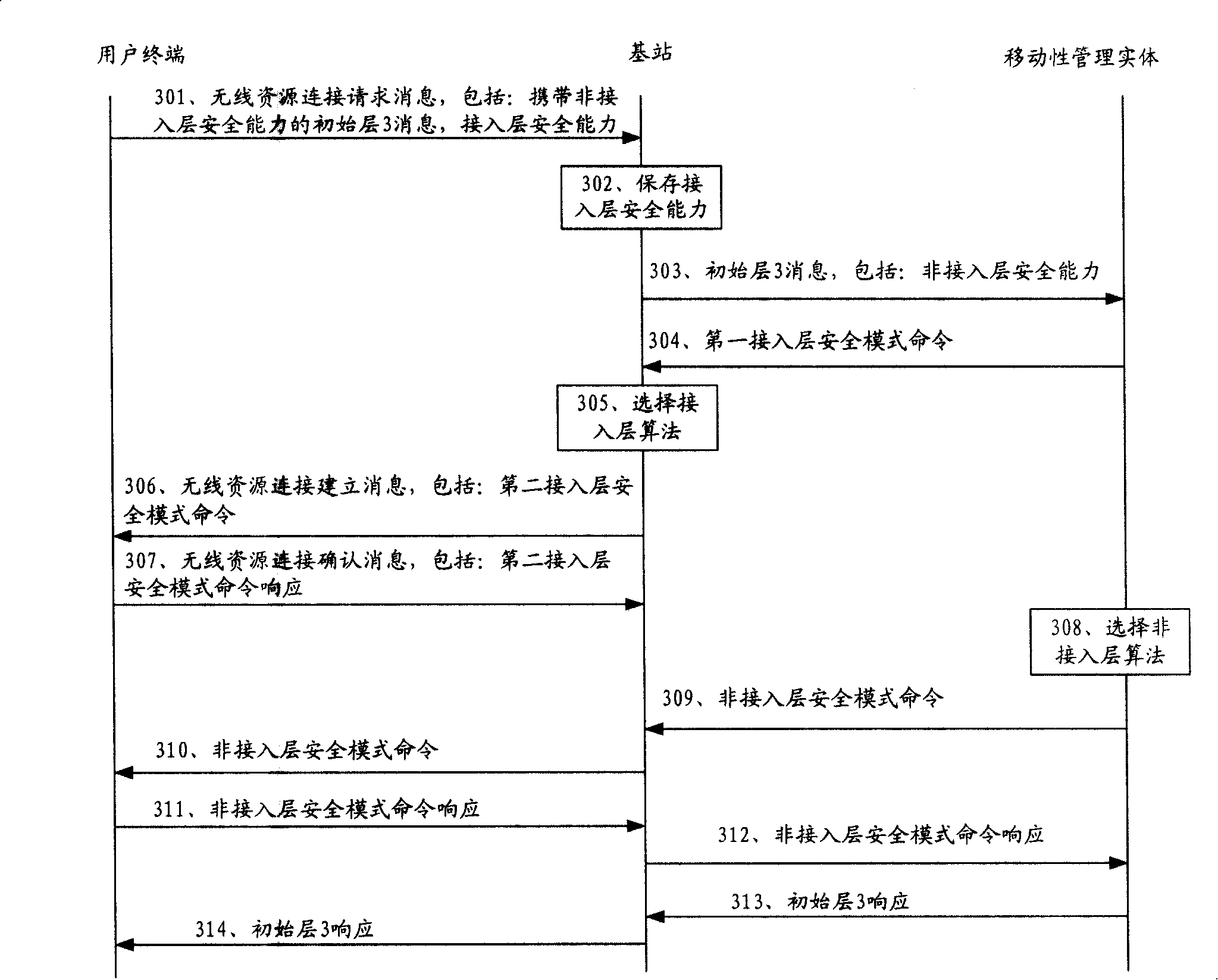
[0031] refer to figure 2 , the security algorithm negotiation method provided by Embodiment 1 of the present invention includes:
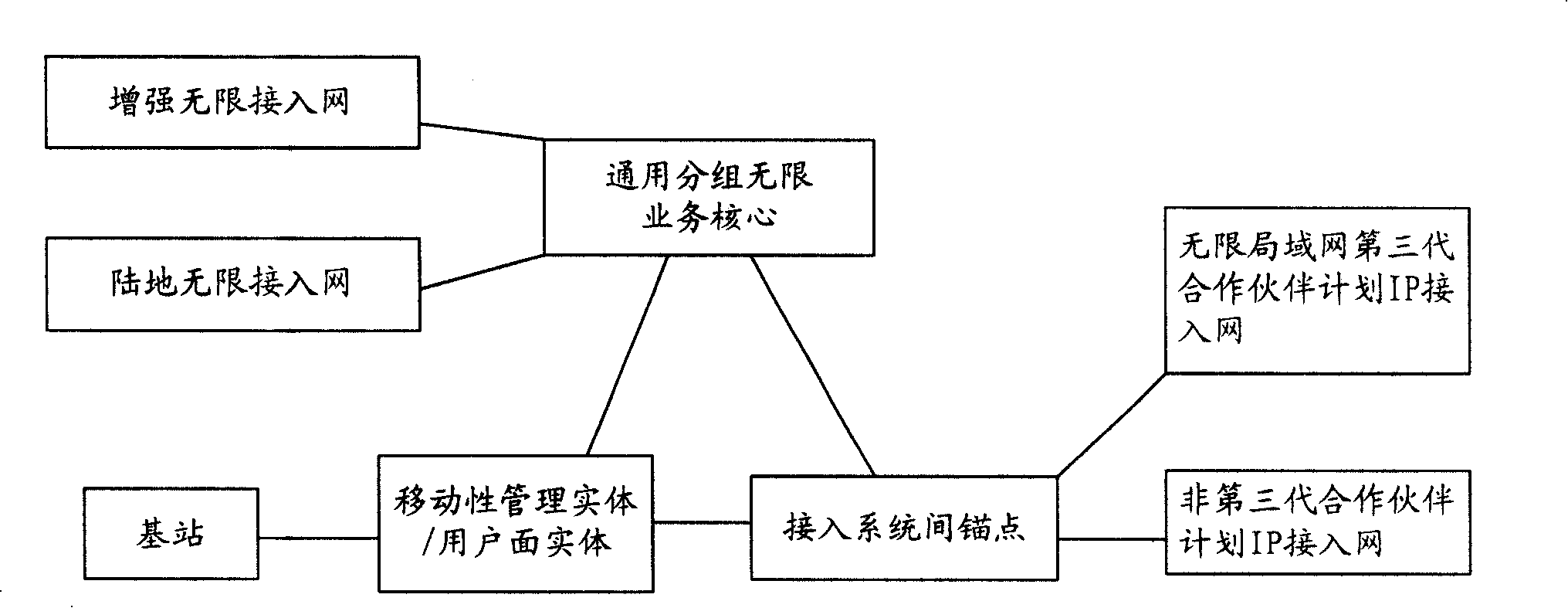
[0032] Implement a middle layer 3 message. Taking the initial layer 3 message as an example, the initial layer 3 message is carried in the radio resource connection (Radio Resource Connection, RRC) request message, and the initial layer 3 response information is carried in the RRC setup message, and the MME selects the NAS Security algorithm, the eNodeB selects the AS security algorithm;
[0033] Step 201, the UE sends a radio resource connection RRC request message to the eNodeB, the request message includes: AS security capability and initial layer 3 message, the initial layer 3 message carries NAS security capability; wherein, the AS security capability is the AS that the UE can support Security algorithm information, t...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com