Virus precaution method and device
A virus and configuration file technology, applied in the network field, can solve problems such as the inability to quickly and effectively remove viruses, achieve the effect of improving efficiency and accuracy, and eliminating tedious operations
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
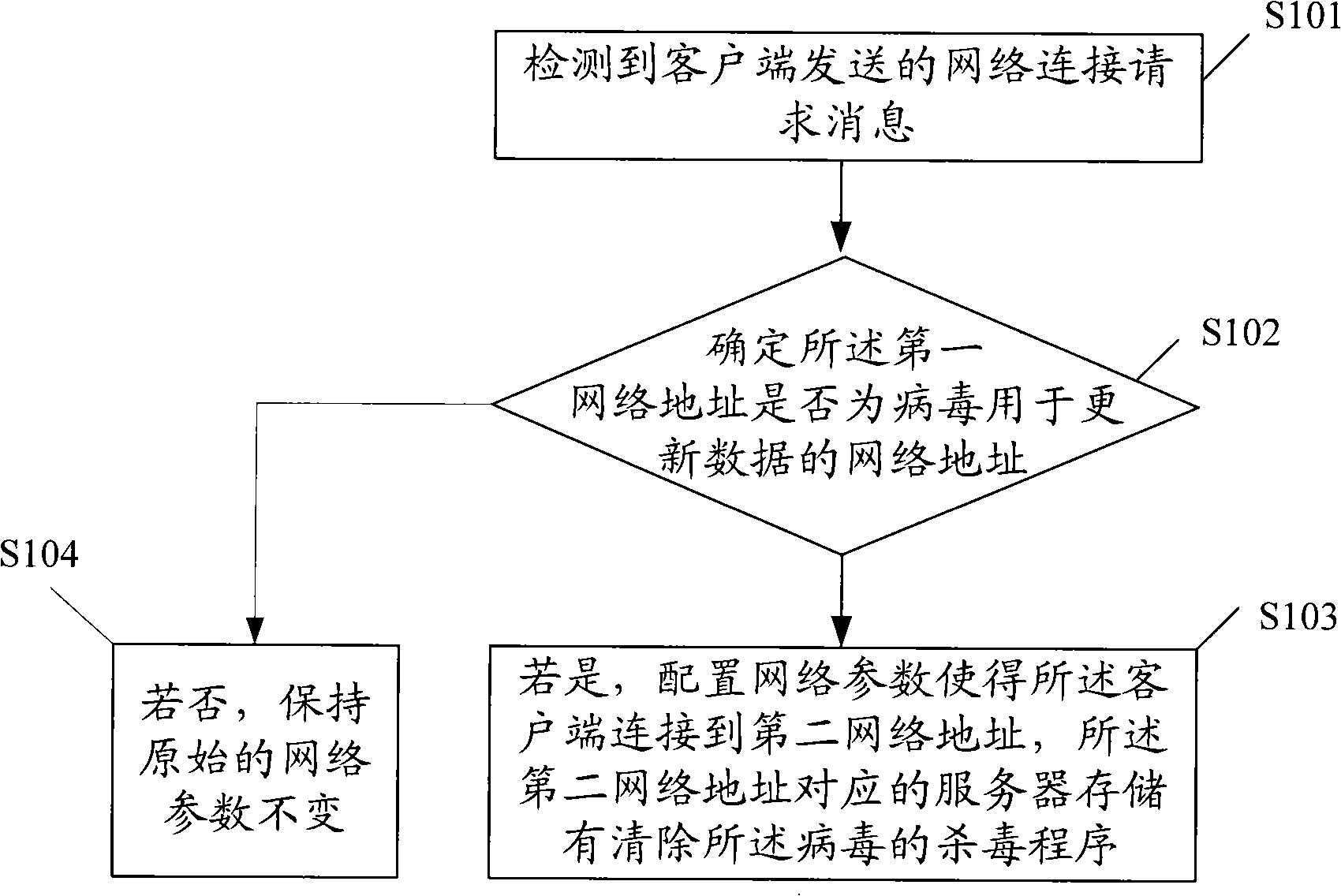
[0027] figure 1 A schematic flow chart of Embodiment 1 of the virus prevention method provided by the present invention, the method includes:
[0028] S101. Detecting a network connection request message sent by the client, where the request message includes a first network address for which the client requests to connect;
[0029] For a virus program with an automatic update download mechanism, when the virus is running, it will trigger the client to automatically connect to the network resource preset by the virus program with a certain strategy (such as regular automatic detection of updates) to download the updated version or new variant of the virus . The client will try to connect to the default network address. According to the provisions of the network protocol, a network connection request must be sent, and the request includes the first network address.
[0030] S102. Determine whether the first network address is a network address used by viruses to update data; ...
Embodiment 2
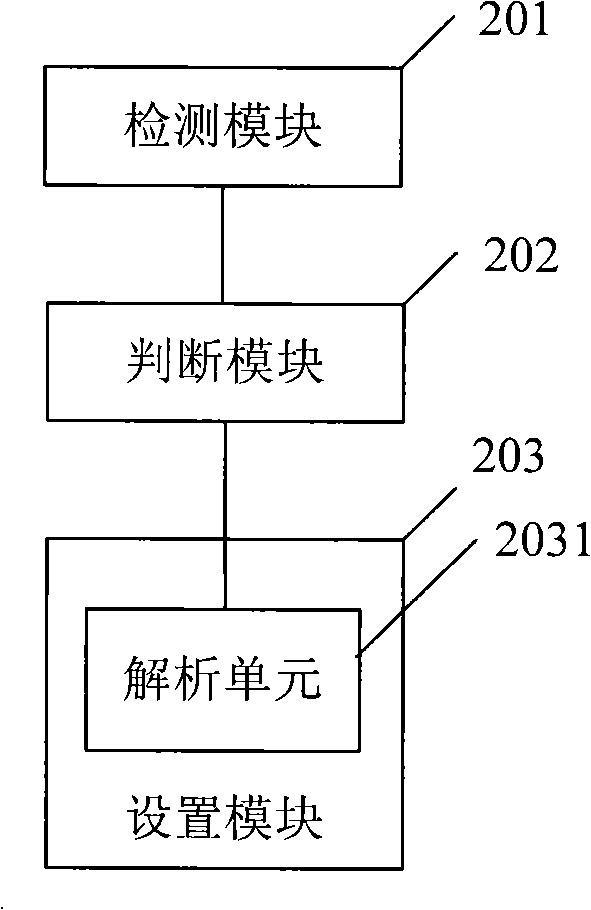
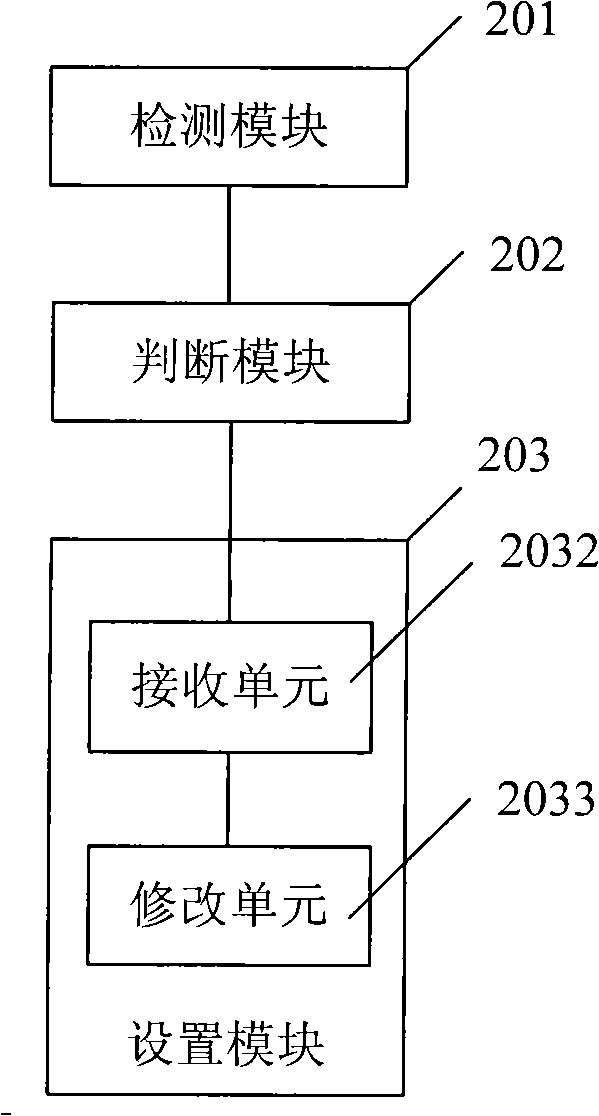
[0037] This embodiment mainly introduces the specific application embodiment of step S103. Steps S101 and S102 can be implemented by conventional means in the field, and will not be repeated here. The following takes a virus Trojan-Downloader.Win32.QQHelper.ws as an example to introduce how to automatically clear the virus by configuring network parameters. According to the name, this virus is a Trojan horse downloader. After analysis, the behavioral characteristics of the virus include the content between the dotted lines as shown below:
[0038] -------------------------------------------------- ----------------------
[0039] (The number 70204 below may vary with different hosts)
[0040] Attempts to download the following four files in random order
[0041] http: / / install1.ring520.org / kkkk / mminstall.exe? queryid=70204
[0042] http: / / install2.ring520.org / kkkk / mminstall.exe? queryid=70204
[0043] http: / / install3.ring520.org / kkkk / mminstall.exe? queryid=70204
[004...
Embodiment 3
[0059] Taking the virus Trojan-Downloader.Win32.QQHelper.vn as an example, it introduces how to automatically clear the virus by configuring network parameters.
[0060] Behavioral characteristics of the virus include:
[0061] (1) First download the following configuration file:
[0062] http: / / up.bizmd.cn / software / update.txt
[0063] (2) Determine the next download content according to the content in the file subsequently, and the author of the virus can completely control the downloading behavior of the downloader by controlling and updating the content of this file. For example, at a certain stage, the content of the file looks like this between the dotted lines:
[0064] -------------------------------------------------- ----------------------
[0065] [PlugList]
[0066] Url=http: / / up.bizmd.cn / software / pluglist.xml
[0067] [Download]
[0068] Ver=42
[0069] Key=2
[0070] ic=1
[0071] URL=http: / / up.bizmd.cn / software / netdde32.exe, 0, 2, W, NULL
[0072] Ocx=...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com