Cipher processor supporting thread-level encryption and decryption and its cipher operation method
An encryption and decryption, processor technology, applied in the direction of electrical digital data processing, instruments, calculations, etc., can solve the problems of not being able to provide cryptographic algorithms, not being able to complete multi-key random cross-encryption and decryption, and not being able to support cross-encryption and decryption. The effect of sewing arbitrary switching
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
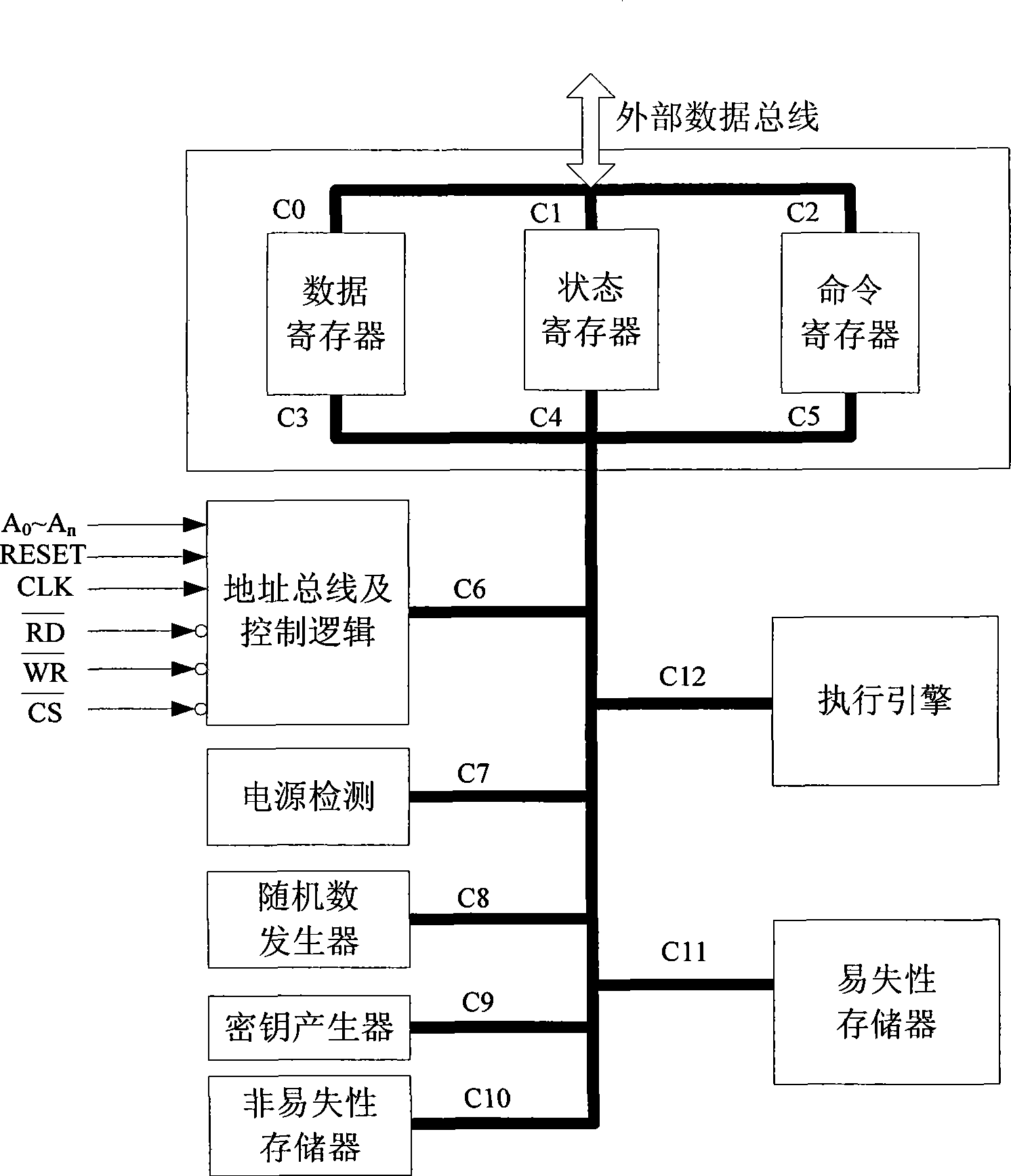
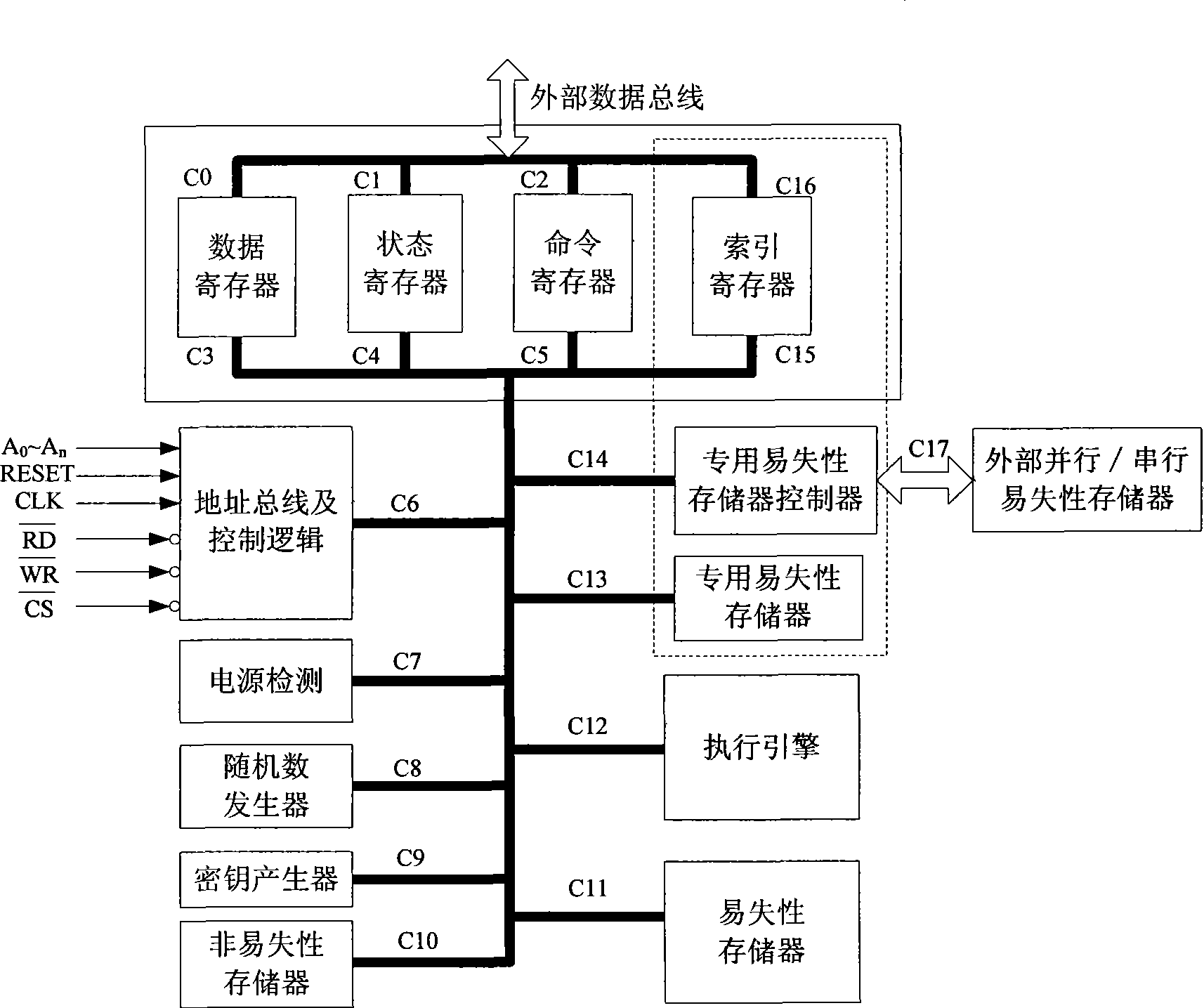
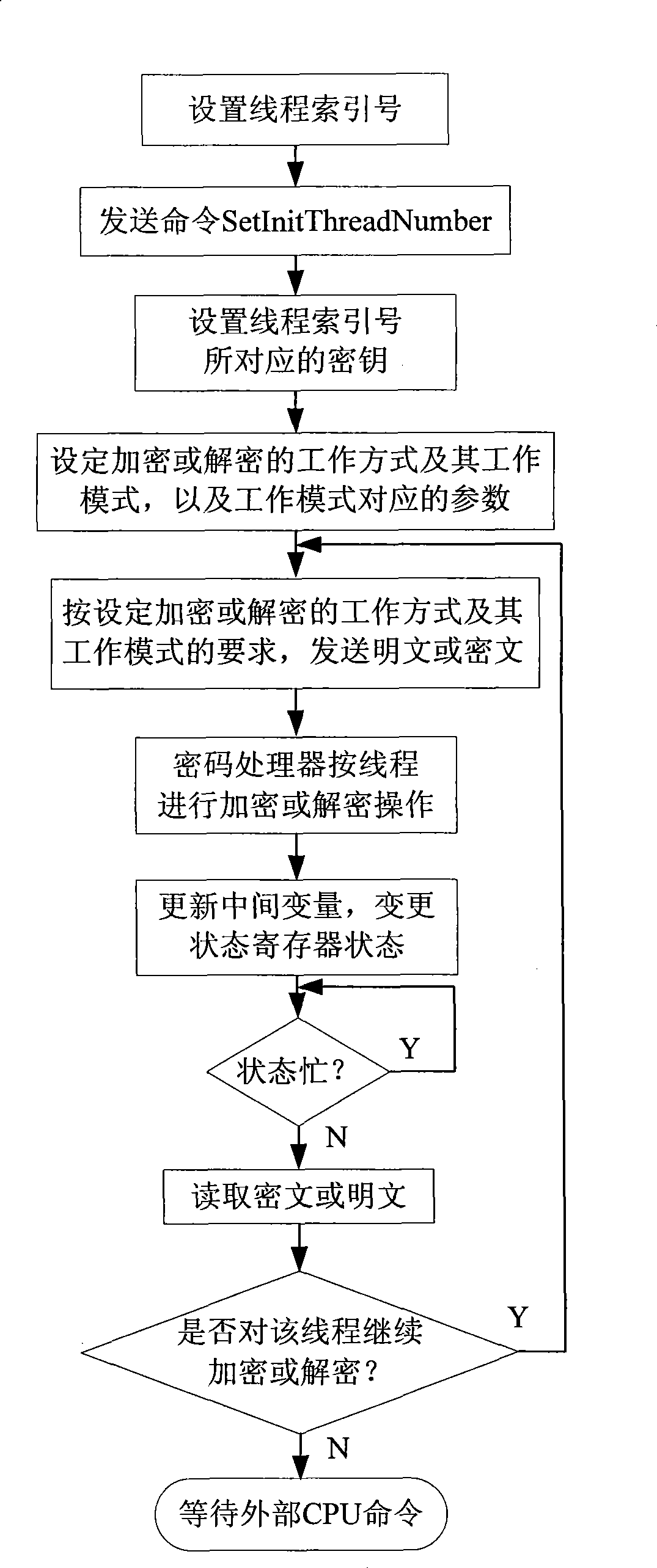
[0042] refer to figure 2 , the present invention consists of data register, status register, command register, address bus and control logic, power supply detection, random number generator, key generator, nonvolatile memory, volatile memory, execution engine, special volatile memory, a dedicated volatile memory controller, and index registers. Among them, the dedicated volatile memory, the dedicated volatile memory controller and the index register are used to interact with the execution engine internally to complete thread-level encryption and decryption. The index register is connected to the external data bus through the sixteenth channel C16, and is connected to other modules through the fifteenth channel C15. The current thread index number is stored in the index register, and the execution engine and the control logic generate pairs according to the value of the index register. Base address for addressing dedicated volatile memory and external parallel / serial volatile...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com