Graded-and-grouped secret image sharing method
A secret image and image technology, applied in the direction of image communication, electrical components, etc., can solve the problems of not being able to adapt to the application
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0077] We choose Matlab7.0 as the software platform, and program to realize the design of the scheme of the present invention. The implementation process is to select the standard test image "Spoke.bmp" of 512×512 as the secret image , select 512×512 standard test images “lena.bmp”, “barbara.bmp”, “peppers.bmp” and “goldhill.bmp” as four masking images respectively (if attached Figure 5 shown). use threshold scheme, When embedding the sub-secret image, the distortion is minimal.
[0078] The specific operation steps are:
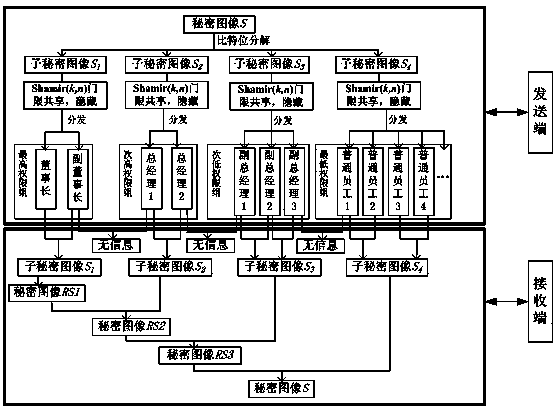
[0079] Ⅰ. Hierarchical decomposition, sharing, and hiding of secret images at the sending end, including the following steps:
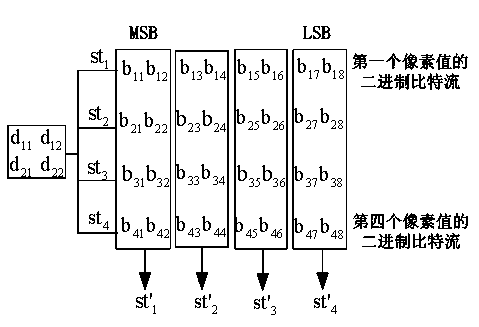
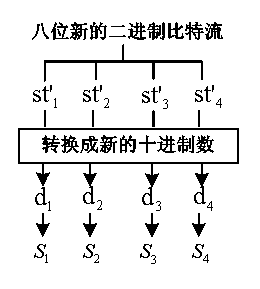
[0080] In the first step, the secret image is decomposed into bits to form multiple sub-secret images of different levels:
[0081] .read a secret image of , which are divided into non-overlapping, Image blocks of size, perform the following steps (2) and (3) from the first image block;
[0082] .The value of...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com