Network authentication method, system and apparatus
A technology of network authentication and authenticator, applied in the field of authentication, can solve the problems of not supporting EAP-MD5 authentication, the whole network is paralyzed, and protecting the unfavorable investment of network operators, so as to avoid network problems and protect network investment
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0027] In order to make the object, technical solution and advantages of the present invention clearer, the present invention will be further described in detail below with reference to the accompanying drawings and examples.
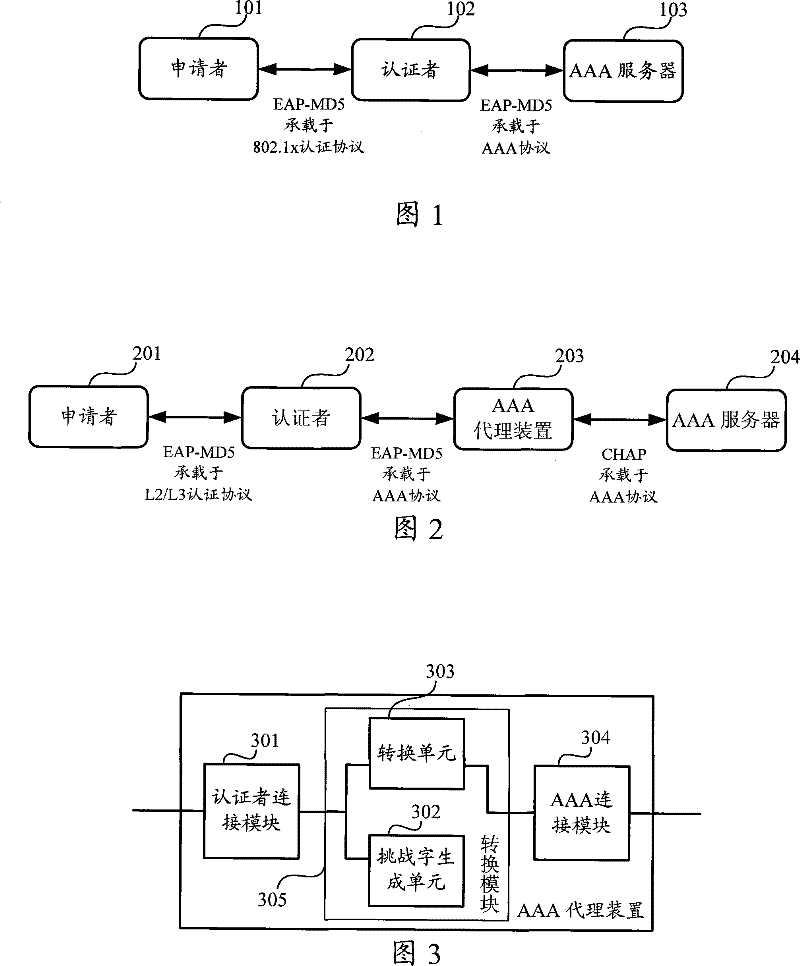
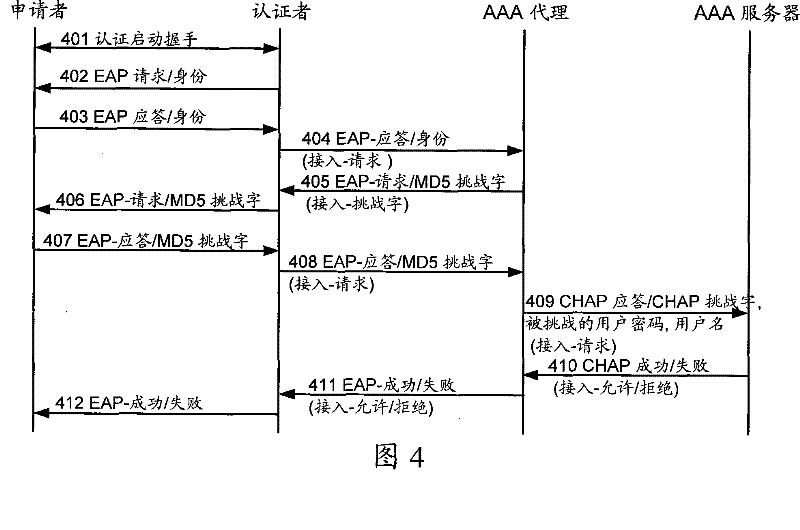
[0028] The embodiment of the present invention mainly introduces an AAA proxy device between the authenticator and the AAA server to realize the conversion between EAP-MD5 authentication and CHAP authentication carried by the AAA protocol, so that the AAA server of the original network does not need to be changed, and the Support new network terminals that support EAP-MD5 authentication.
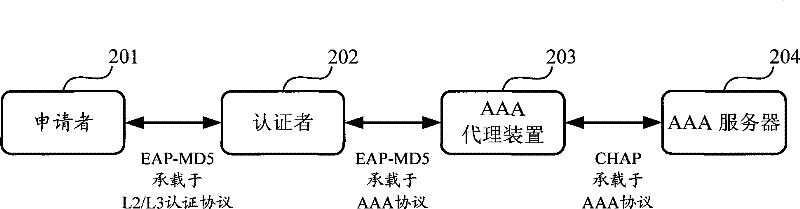
[0029] figure 2 It is a structural diagram of the EAP-MD5 authentication system of the embodiment of the present invention;
[0030] As shown in the figure, the authentication system includes: AAA proxy device 203 and AAA server 204;
[0031] Wherein, the applicant 201 supports EAP-MD5 authentication; the authenticator 202 supports EAP-MD5 authentication; the AAA s...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com