Method, network node and system for preventing aggression in P2P network
A P2P network and node technology, applied in the P2P field, can solve the problem of malicious nodes not being processed, and achieve the effect of avoiding influence
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
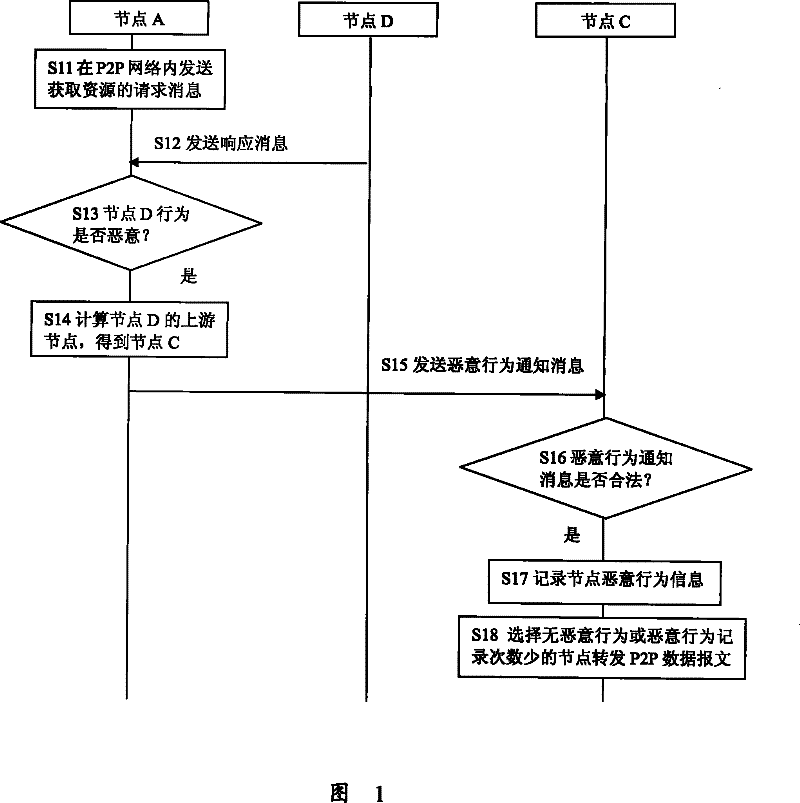
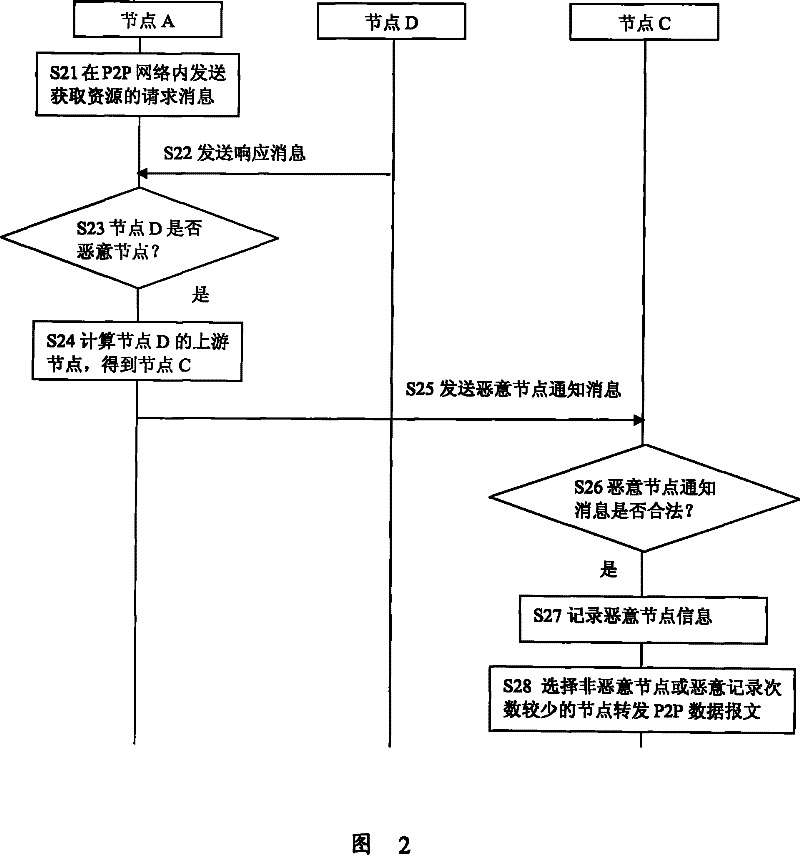
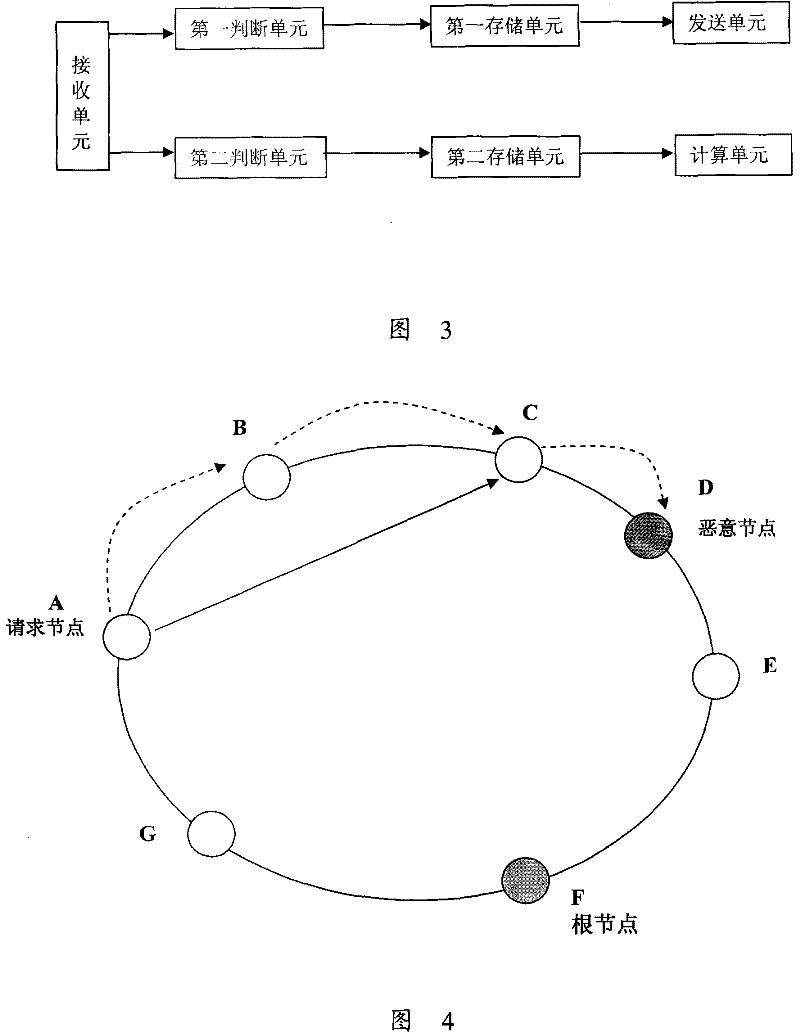
[0034] Embodiments of the present invention provide a method for preventing attacks in a P2P network, and a P2P network and network nodes for preventing attacks. When a node detects that other nodes in the P2P network have made malicious behaviors, the evidence proving that the node has made malicious behaviors is sent to the upstream node of the node that made the malicious behavior, and the upstream node records the node that made the malicious behavior. Information and the number of times the node has been notified to perform malicious behaviors, and when it is necessary to forward data packets, select nodes with no malicious behavior records or nodes with fewer malicious behavior records to forward data packets, so as to reduce or avoid The purpose of the influence of malicious behavior nodes on the entire P2P network.
[0035]The present invention will be described in detail below in conjunction with the accompanying drawings and embodiments.
[0036] like Figure 4 Sho...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com