A method, detection device and monitoring equipment for preventing server from being attacked
A detection device and monitoring equipment technology, applied in the field of communication, can solve the problems of blocking agent access, unable to defend against attacks, etc., and achieve the effect of defending against attacks
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
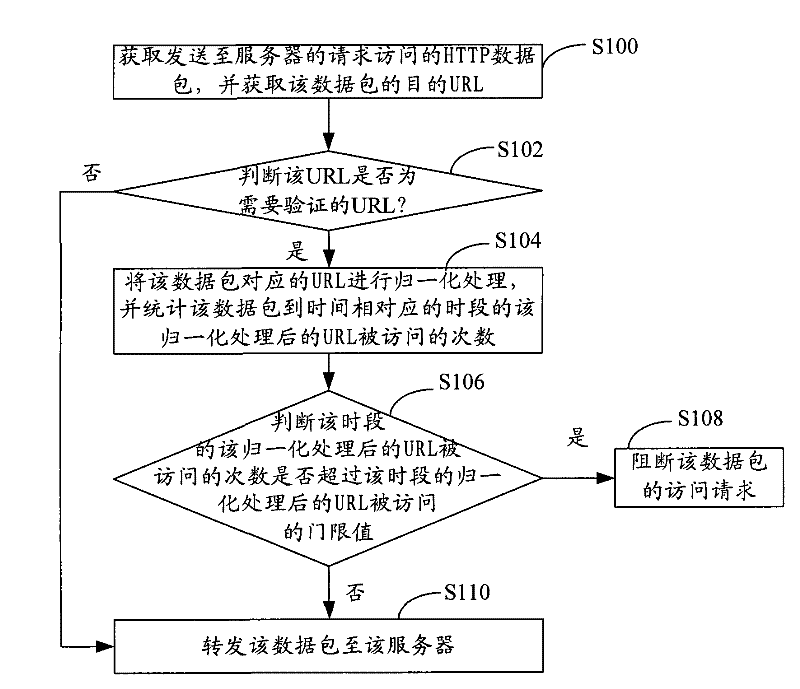
[0037] Step S100, get HTTP packets sent to the server request, and obtain the uniform resource positioning of the data packet (URL).
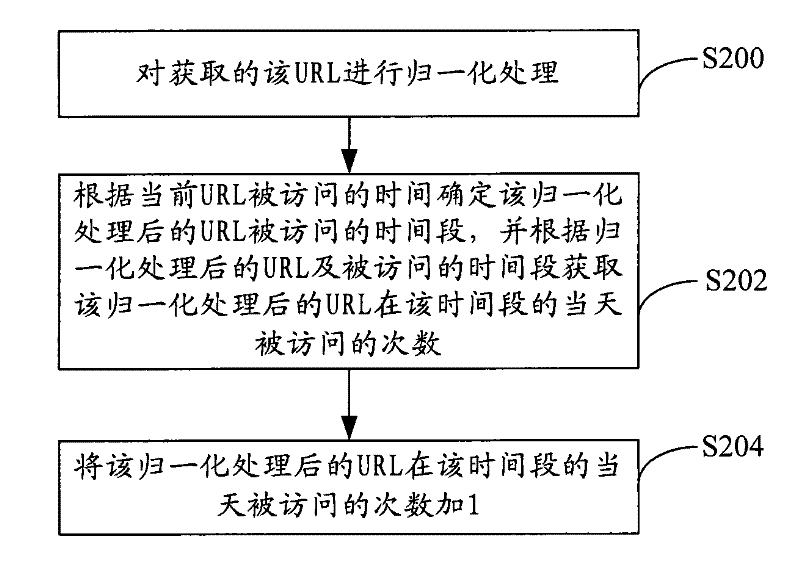
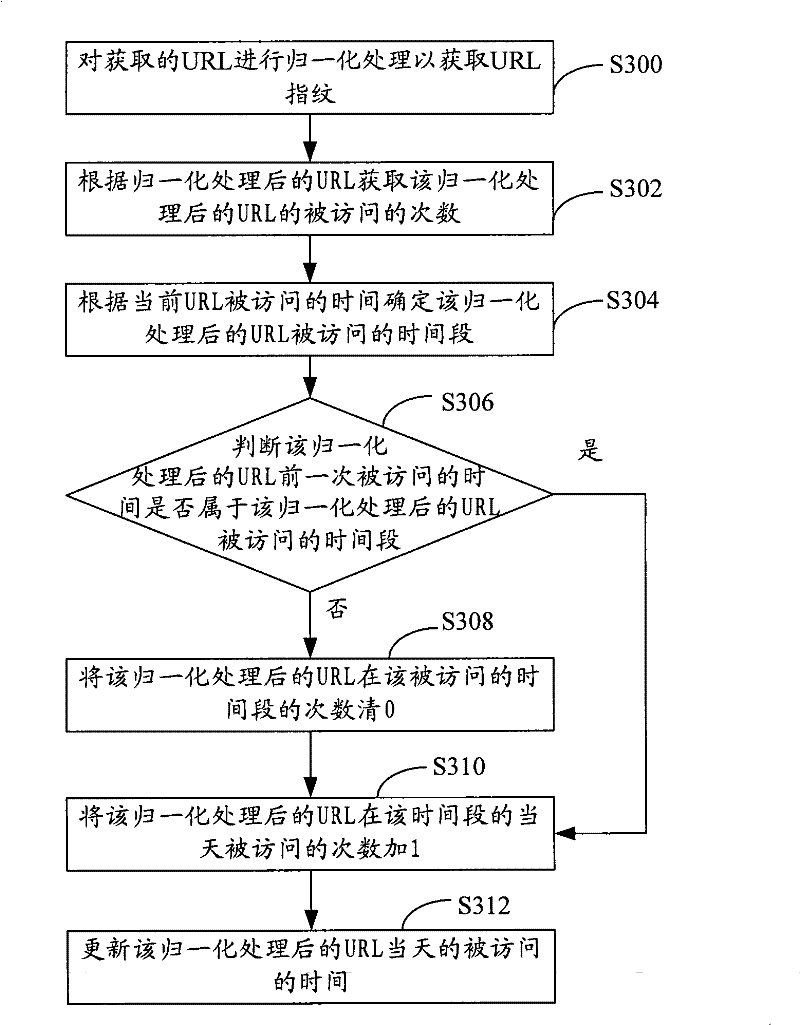
[0038] Step S102, determine whether the URL is a URL that needs to be verified.In this embodiment, the URL that needs to be verified by default or according to the load of the URL.In this embodiment, the load of the URL is determined by the short interval between the request and the response of the URL.In this embodiment, if the time interval between the request and the response of the URL and the response is greater than that of a certain door limit, the time interval between the request and the response of the URL is consideredThe time interval between the response is not greater than the limit value, then the time interval between the request and the response of the URL and the response is determined that the URL is not overloaded. Among themset up.When the URL is an overload, the URL needs to be verified, and the URL does not need to be verifie...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com