Authentication computer and program
A computer and client computer technology, applied in the field of authentication systems, can solve the problem of bank untrustworthiness compensation, damage and other problems, and achieve the effect of improving security and convenience
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
no. 1 Embodiment approach
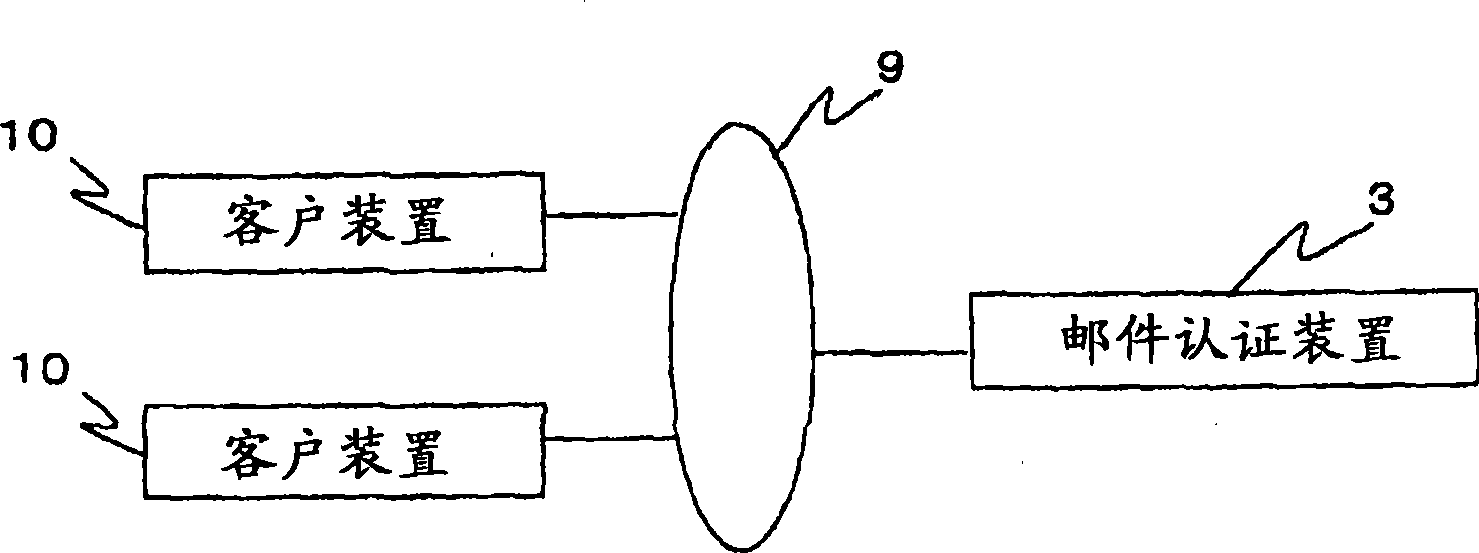
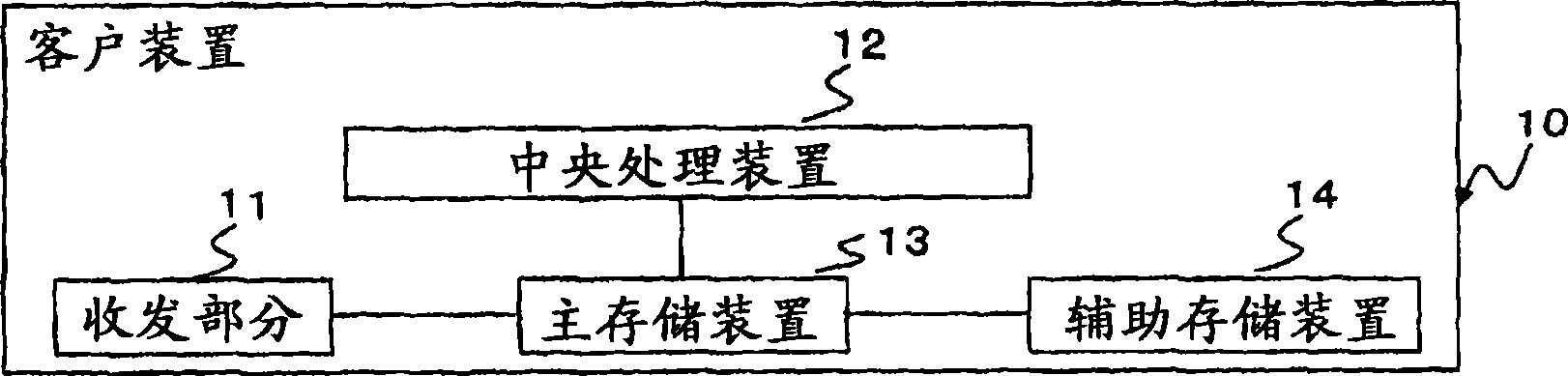
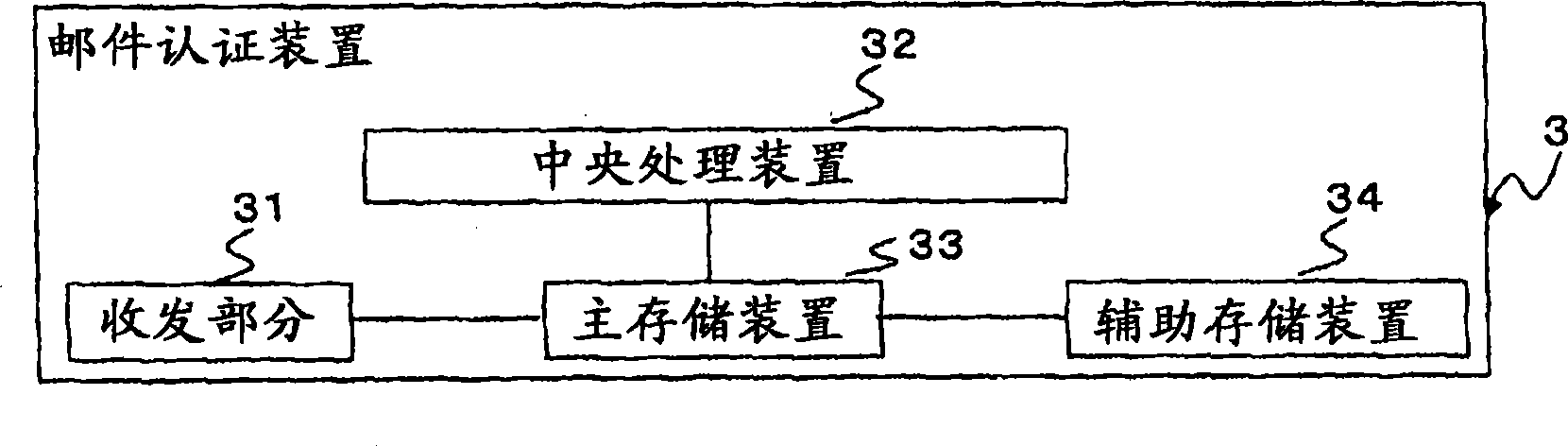
[0076] figure 1 It is a schematic configuration diagram of the personal authentication system of the first embodiment. figure 1 The personal authentication system shown in has a plurality of client devices 10 and mail authentication devices 3 . The client device 10 is a computer operated by a user who intends to be authenticated. And the client device 10 is connected to the network 9 . Regarding the client device 10, the figure 2 in detail. In addition, the network 9 is a data communication network such as a dedicated line network, a public switched telephone network, or a LAN. Meanwhile, the network 9 may be an internal network or the Internet. The mail authentication device 3 is connected to a client device 10 via a network 9 . Specifically, the mail authentication device 3 is connected to the client device 10 via an internal network or the Internet. In addition, the mail authentication device 3 may be provided with an interface for the Internet and an internal netwo...
no. 2 Embodiment approach
[0122] Hereinafter, the personal authentication system of the second embodiment will be described, but descriptions will be omitted by using the same symbols for points that overlap with the personal authentication system of the first embodiment.
[0123] The configuration of the personal system of the second embodiment is the same as that of the personal authentication system of the first embodiment ( figure 1 ) are the same, so the explanation is omitted here. However, in the second embodiment, the network 9 is the Internet. In addition, the client device 10 transmits an authentication request and an authentication result request to the mail authentication device 3 via HTTP. Then, the client device 10 receives the authentication mail address and the authentication result from the mail authentication device 3 via HTTP. Therefore, when the client device 10 is a mobile phone, it is equipped with a WEB browser function and an e-mail sending function. In addition, the mail aut...
no. 3 Embodiment approach
[0130] Next, the personal authentication system of the third embodiment will be described, but the description will be omitted by using the same reference numerals for points that overlap with the personal authentication systems of the first and second embodiments.
[0131] The mail authentication device 3 included in the personal authentication system of the second embodiment has an authentication function and a function of sending a web page including unique information of the user. In this case, in order to change the conventional WEB server to have the function of the mail authentication device 3, it is necessary to change the program of the WEB server. In contrast, in the third embodiment, an embodiment in which the personal authentication method of the present invention can be easily introduced into a conventional WEB server will be described. The conventional WEB server included in the personal authentication system of the third embodiment is used as the import WEB serv...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com