System and method for implementing call authentication gateway
An authentication and gateway technology, applied in telephone communication, supervision/control of auxiliary connections, electrical components, etc., can solve the problems of complex implementation and operation, high risk, and large investment.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
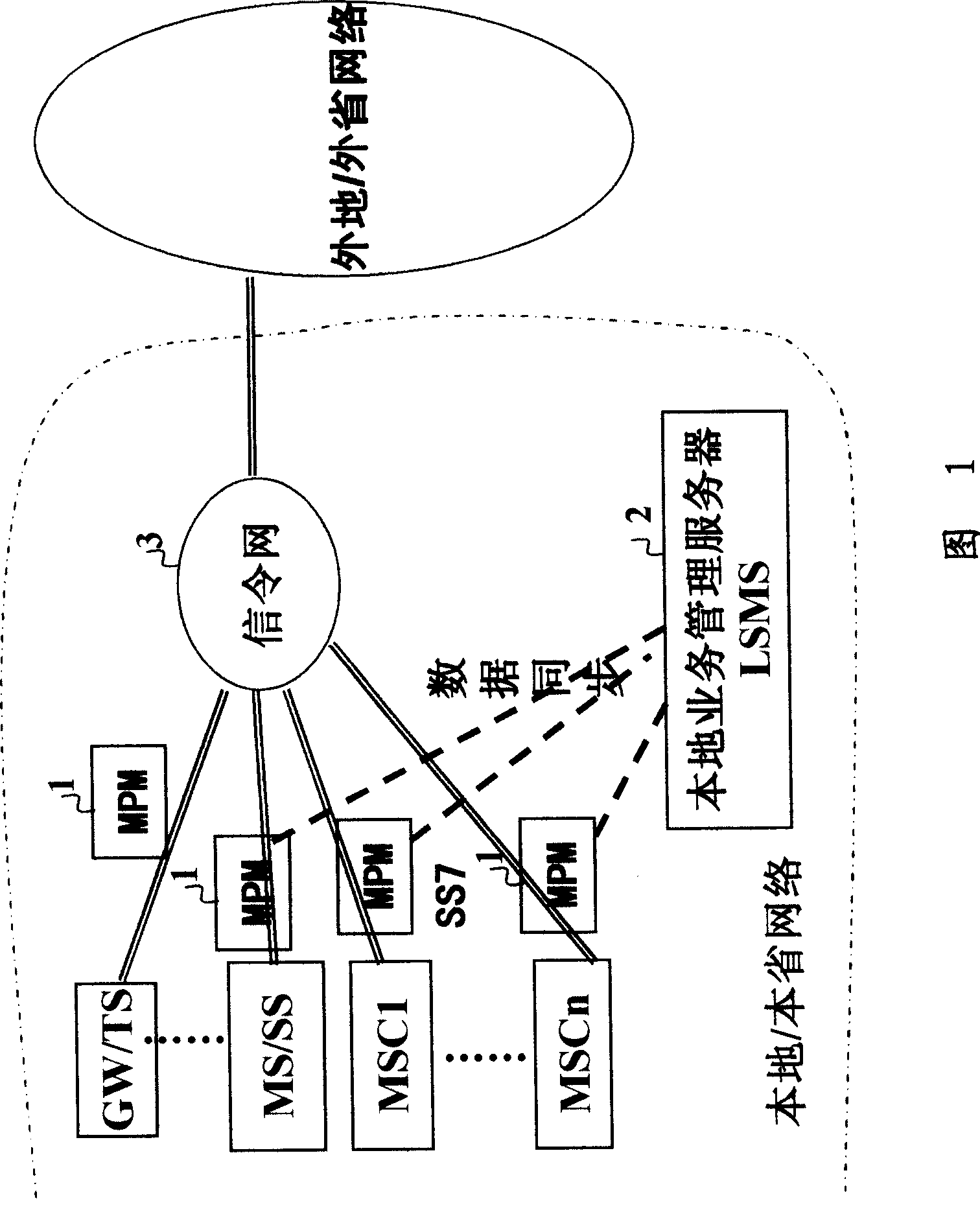
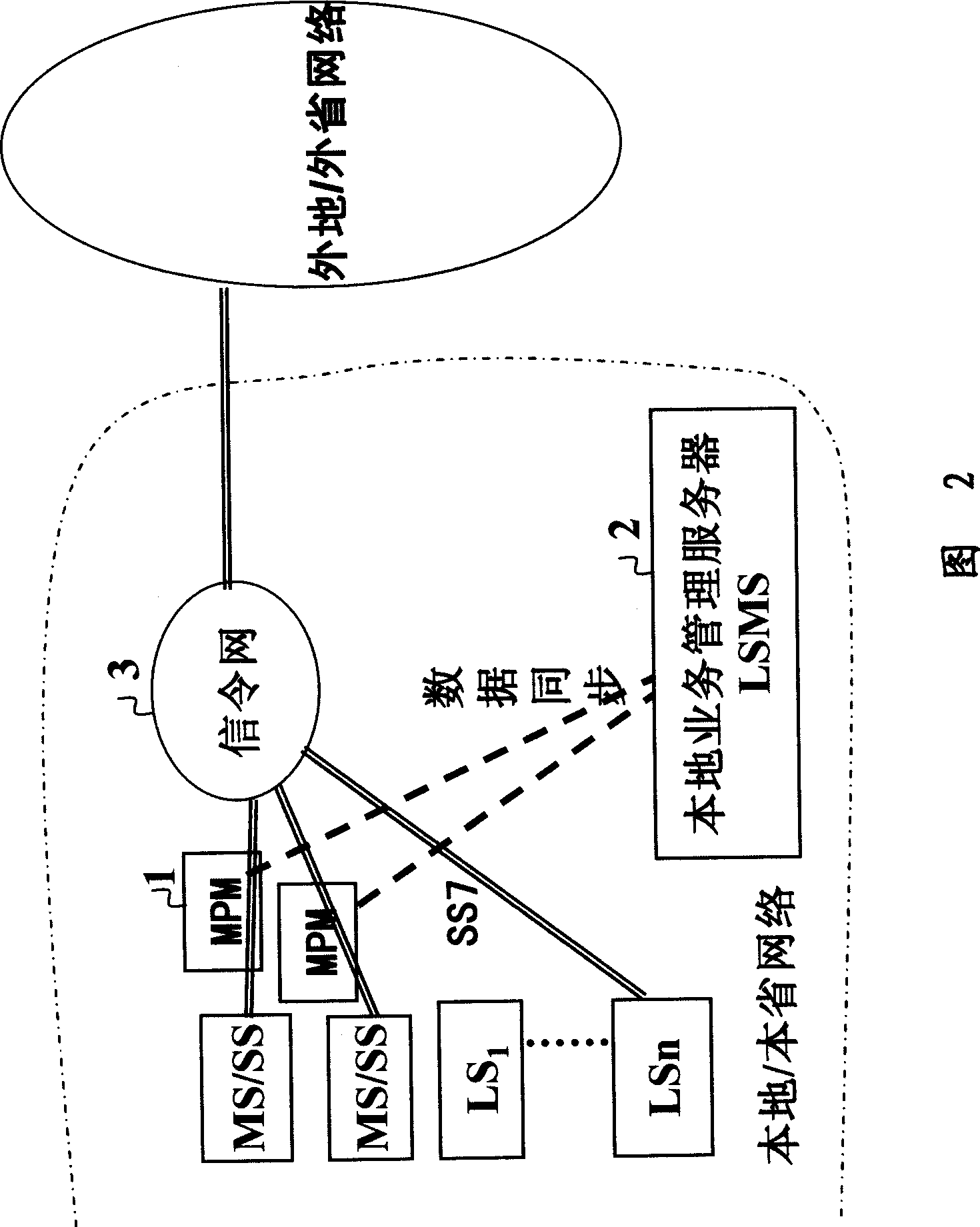
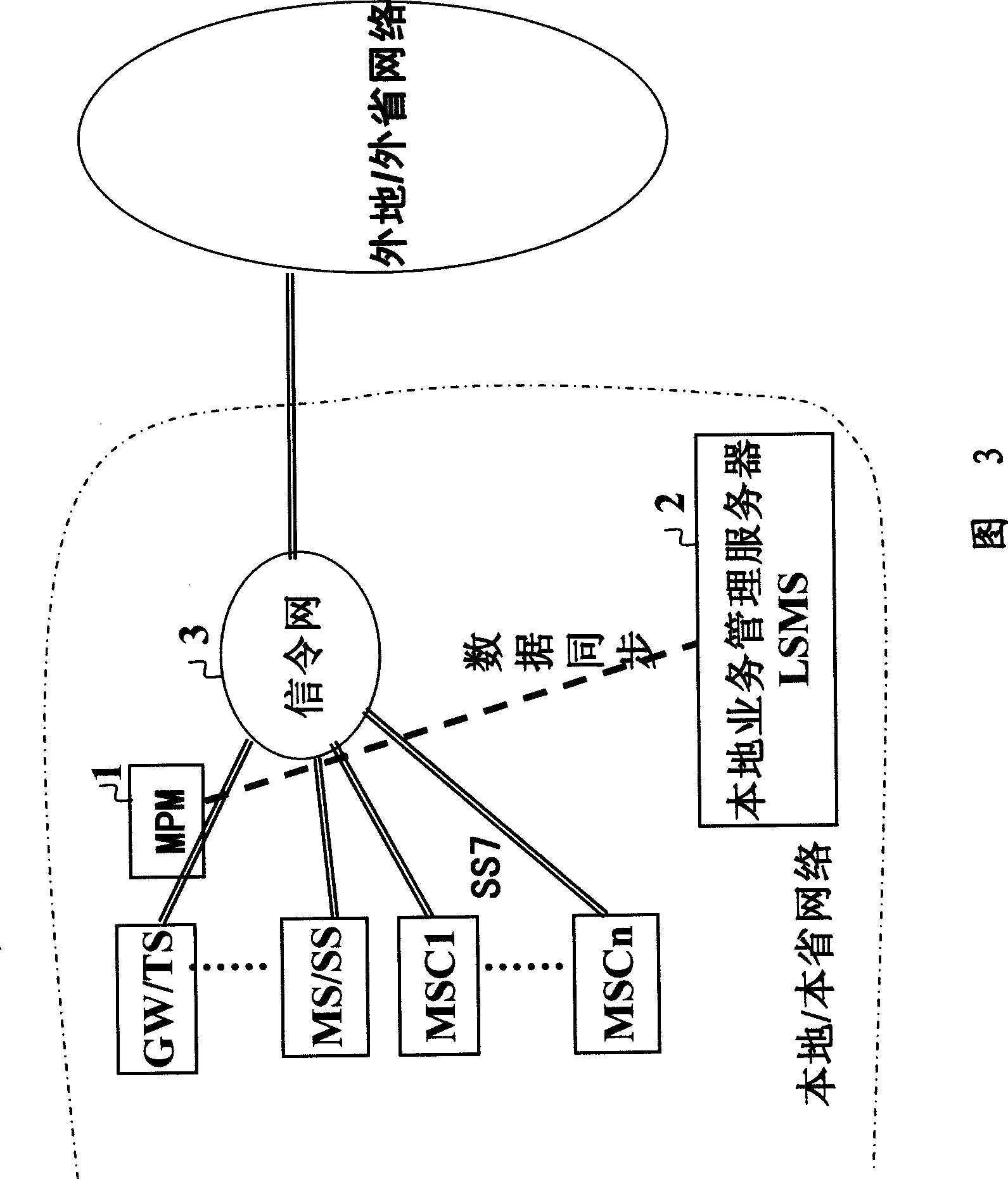
[0018] Fig. 1 is a schematic diagram of the system networking of the call authentication gateway, which consists of several mobile switching centers (MSCs), soft switches (SSs), tandem offices (MSs), and gateway offices (GWs) connected on the No. 7 signaling network 3. ), a local office (LS) or a toll office (TS), etc., the system also includes a number of signaling message detection processing devices (MPM) 1—and a local service management server (LSMS) 2, wherein:
[0019] Each MPM is connected to the No. 7 signaling link between MSC / MS / SS / GW / TS and the signaling network, and is connected to the LSMS. The MPM is used to analyze the signaling message and detect and identify the call message that has been included in the black and white list. The call source is used to control calls to blacklisted and blacklisted numbers; it is used to execute synchronous modification commands of business rules and blacklisted and blacklisted numbers from LSMS, and report working status to LSMS...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com