Method and device for issuing identity certificate in trusted computing
A technology of identity proof and trusted computing, applied in user identity/authority verification, public key for secure communication, electrical components, etc., can solve problems such as heavy load, achieve the effect of reducing load and reducing the amount of certificate issuance
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0080] In order for those skilled in the art to further understand the features and technical contents of the present invention, please refer to the following detailed description and accompanying drawings of the present invention. The accompanying drawings are provided for reference and illustration only, and are not intended to limit the present invention.
[0081] The technical solutions of the present invention will be described below in conjunction with the drawings and embodiments.
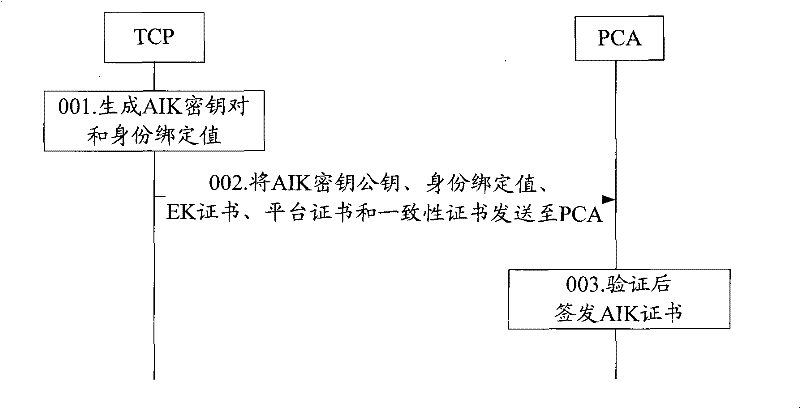
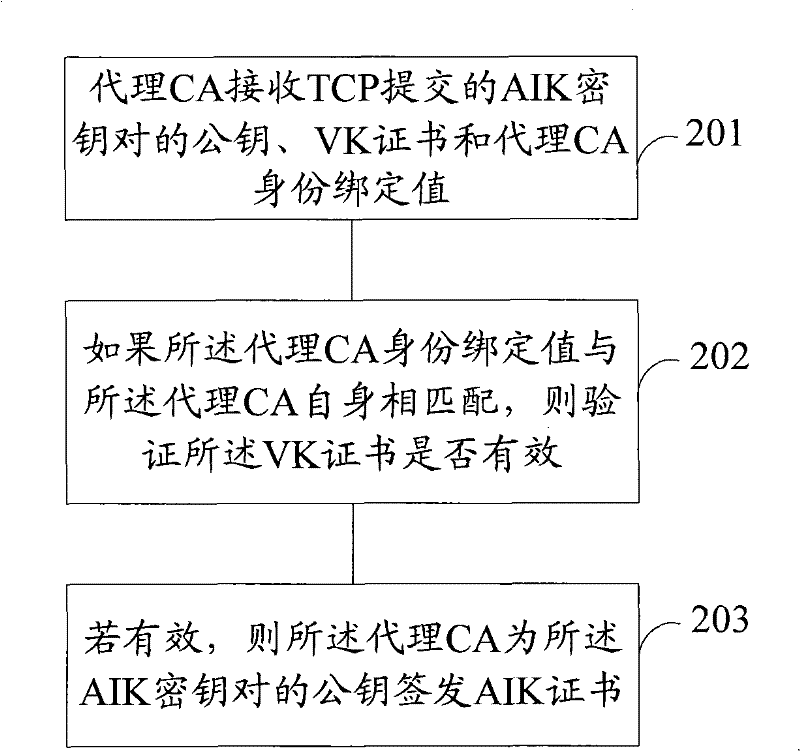
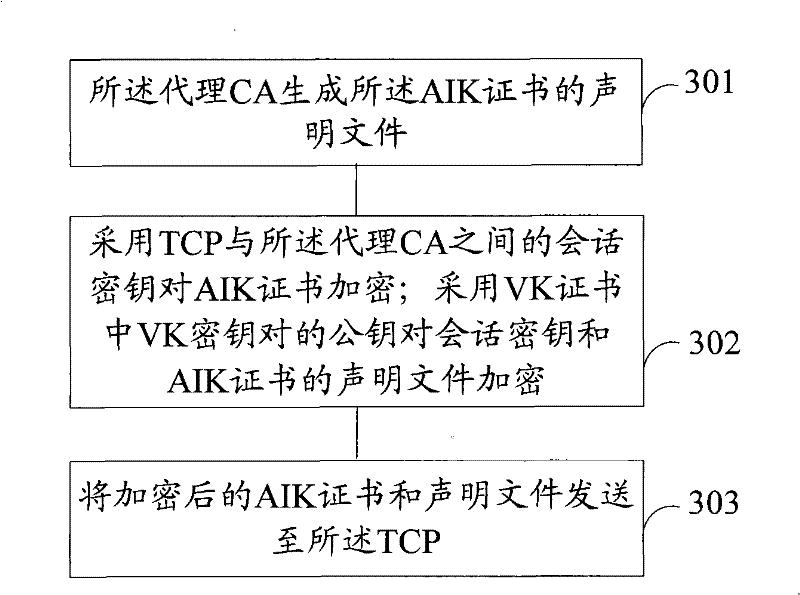
[0082] refer to figure 2 , is a flowchart of a method for issuing an AIK certificate in trusted computing according to an embodiment of the present invention. In the embodiment of the present invention, a method of issuing an AIK certificate for TCP is described with a proxy CA as the main body, wherein the proxy CA is a trusted third party authorized by a privacy CA and capable of issuing certificates. The method includes:
[0083] Step 201, the proxy CA receives the public key of the AIK...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com