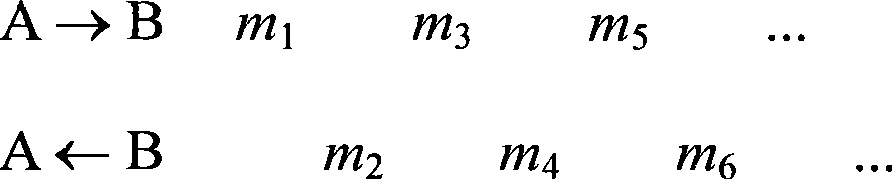Keyword extracting method for network unknown application
A technology for extracting methods and keywords, which is applied in the field of network security and can solve problems such as confusion
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0022] The present invention will be further described below in conjunction with the accompanying drawings.
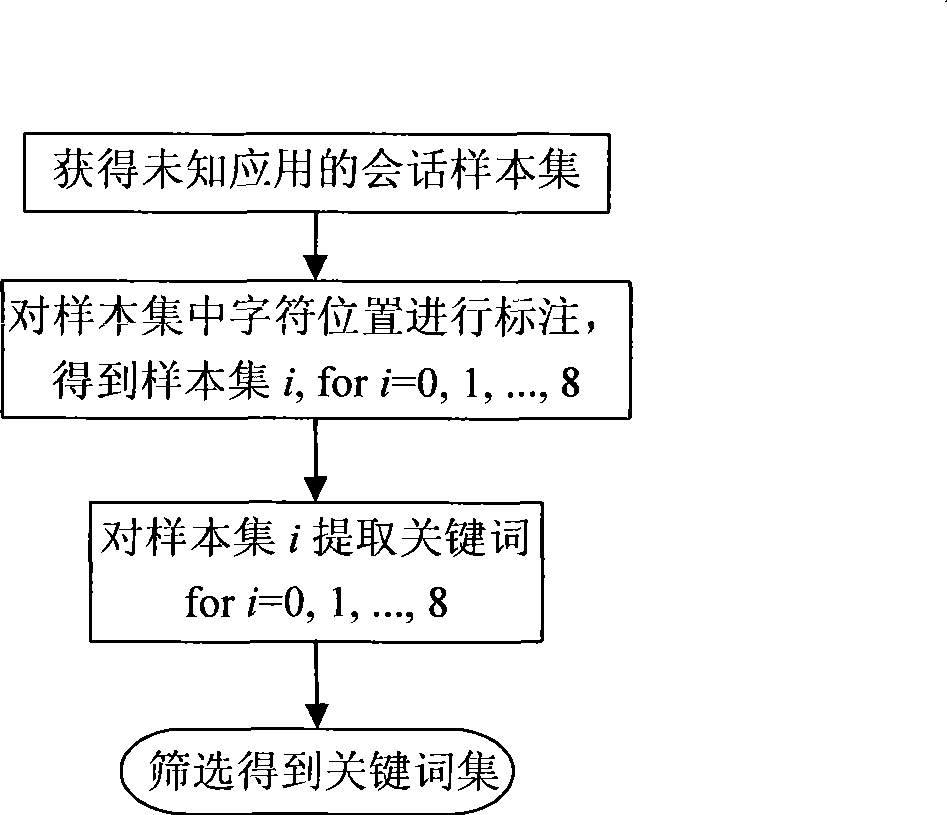
[0023] The invention adopts a data mining method to extract keywords from application layer data of unknown applications. A specific implementation method such as figure 1 As shown, it includes the following steps:
[0024] 1. Collection of samples
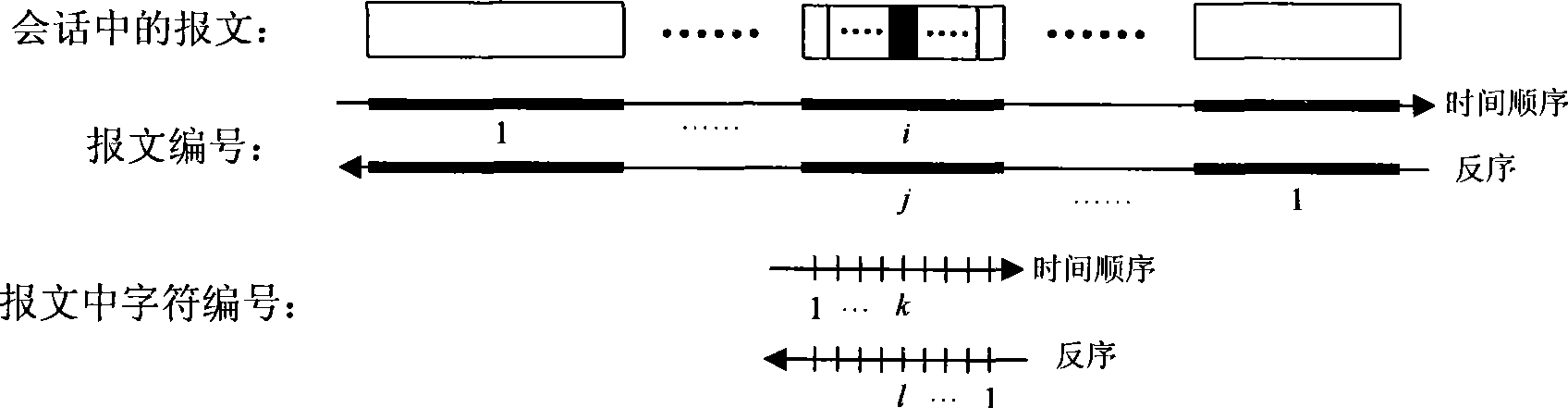
[0025] Samples are collected from the same unknown application to form a sample set, each of which is a session record of this application; these session samples are further divided into sample subsets, and the session samples contained in each sample subset should have something in common, for example, for client-server applications, all sessions in this sample subset have the same server IP address and port number; for P2P applications, all sessions in this sample subset occur at between a given set of IP addresses. Assume that there are N>1 sample subsets in the sample set, and M>N session samples. In order to make...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com