USB interface hardware storage apparatus with log off function when missed and implementing method
A USB interface and storage device technology, applied in computer security devices, preventing unauthorized use of memory, instruments, etc., can solve problems such as USBKey access and potential safety hazards
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
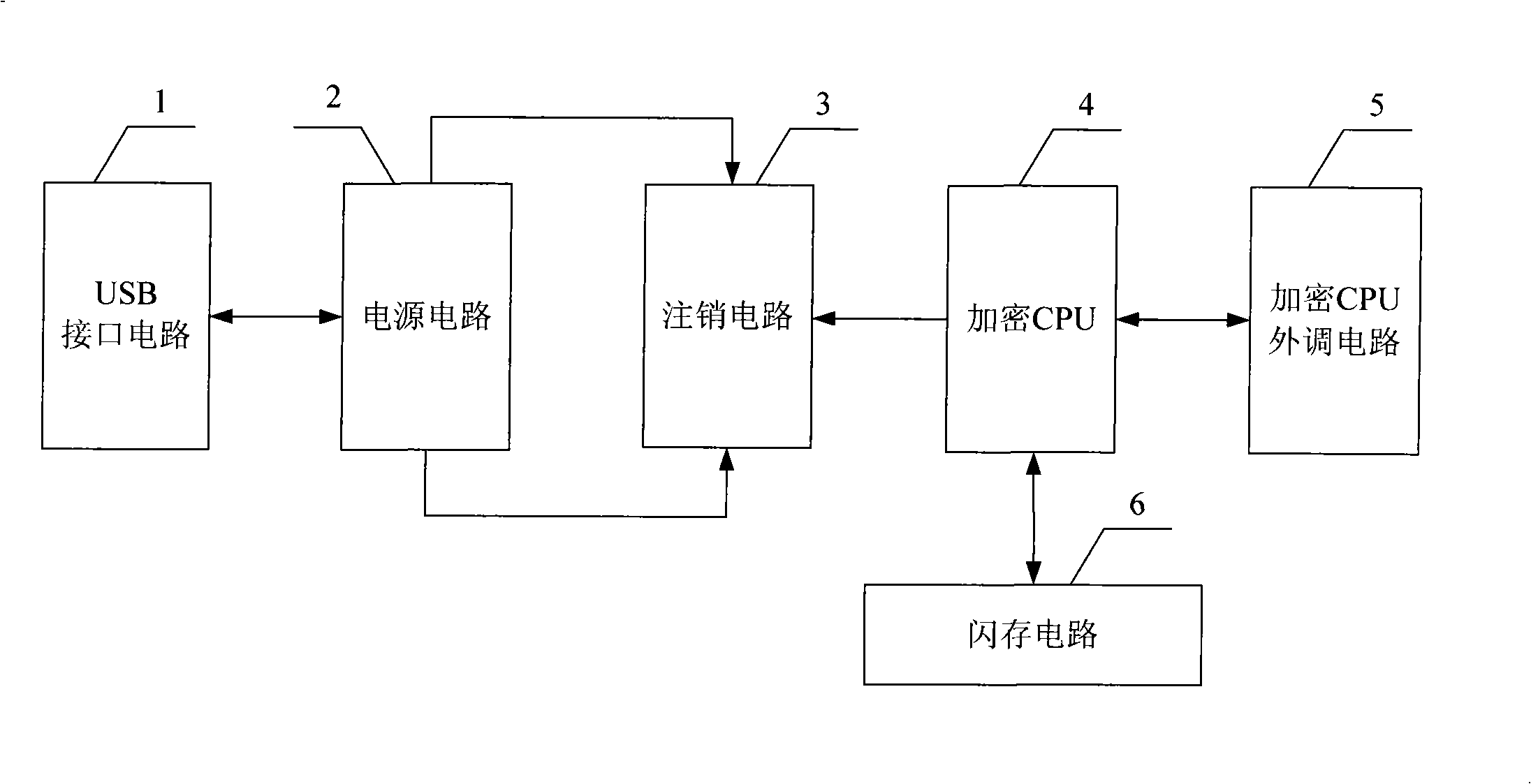
[0017] Embodiment 1, combining Figure 1 to Figure 6 This embodiment will be described.
[0018] A kind of USB interface hardware storage device with lost logout function, it comprises USB interface circuit 1, power supply circuit 2, logout circuit device 3, encryption CPU 4, encryption CPU peripheral circuit 5 and flash memory circuit 6, the input and output of USB interface circuit 1 end is connected with the output and input ends of power supply circuit 2, and two output ends of power supply circuit 2 are connected with two power supply input ends of cancellation circuit device 3 respectively, and the signal output terminal of encryption CPU4 is connected with the control input terminal of cancellation circuit device 3, The data input and output terminals of the encryption CPU 4 are connected with the data input and output terminals of the encryption CPU peripheral circuit 5, and the storage data input and output terminals of the encryption CPU 4 are connected with the data...
Embodiment 2
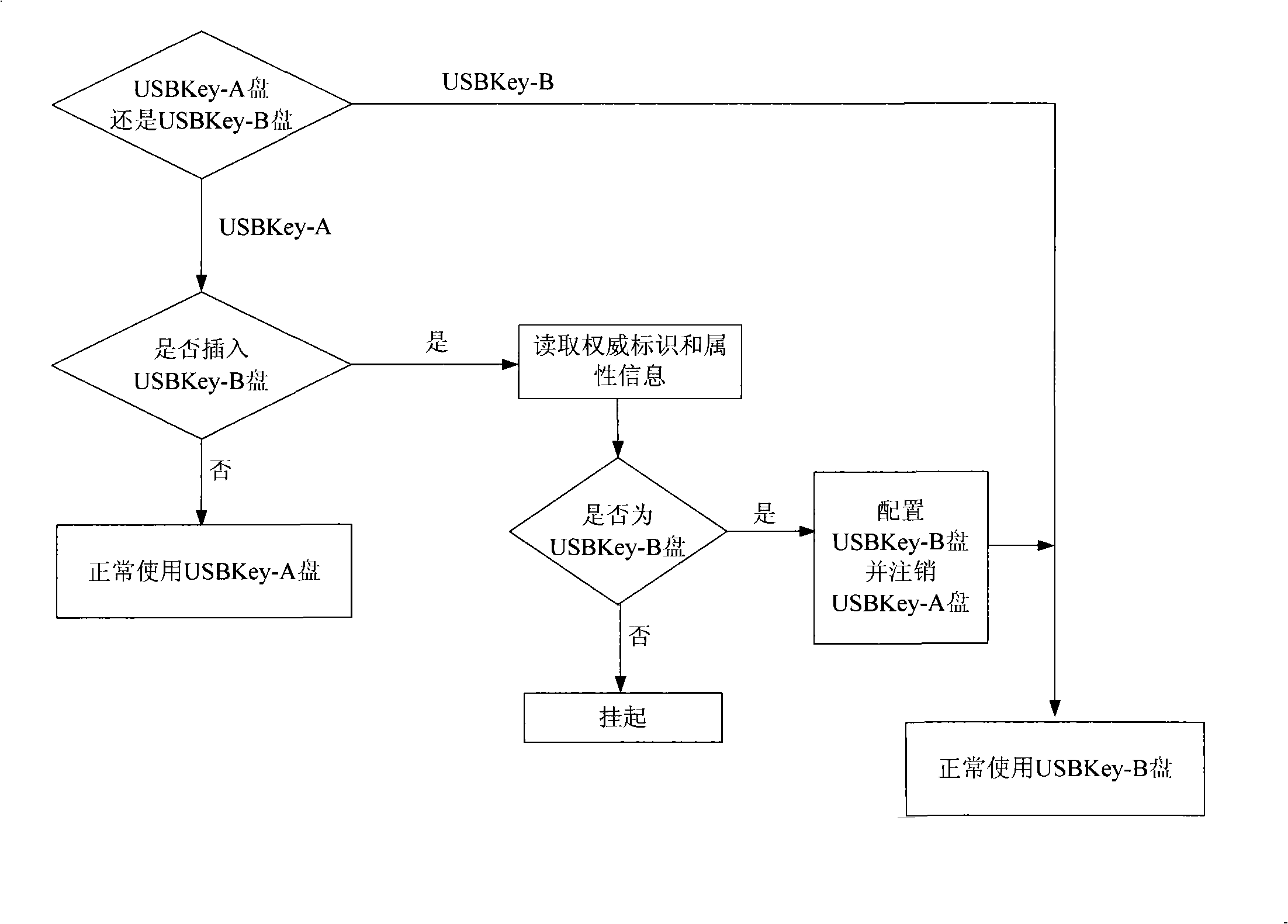
[0022] Embodiment 2, the steps of the described method for implementing lost logout are:
[0023] Step 11. Format the USBKey-A disk and USBKey-B disk with the same hardware through the client formatting tool software;
[0024] Step 12. Divide the initialized USBKey-A disk and USBKey-B disk into three areas: CD-ROM area, encrypted U disk area and hidden area, and set the authoritative USBKey logo on the USBKey-B disk to realize USBKey-B disk pairing Logout permission of USBKey-A drive;
[0025] Step 13, store the client software in the USBKey-A disk and the USBKey-B disk respectively, wherein the client software to be protected is stored in the CD-ROM area of the USBKey-A disk and the USBKey-B disk, and the administrator password, Common user password and Windows login password;
[0026] Step 14. Set the USBKey-A disk authentication to boot through the client software, enter the access password to access the host, and when the USBKey-A disk is lost or canceled, the USBKey-B...
Embodiment 3
[0027] Embodiment 3, this embodiment is different from embodiment 2 in that the optical disk area is a read-only attribute; the encrypted U disk area is accessed and used through identity authentication; the hidden area is divided into unauthorized access, read-only and read-write attributes , the administrator sets the user's access authority, and the hidden area is accessed after the user logs in according to the access authority set by the administrator, which is completed through the application program interface library.
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com