Method and system for recognizing end-to-end flux
A technology of network traffic and P2P traffic, which is applied in the field of communication, can solve the problems of unable to identify P2P traffic, unable to effectively control P2P traffic, and unable to identify
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
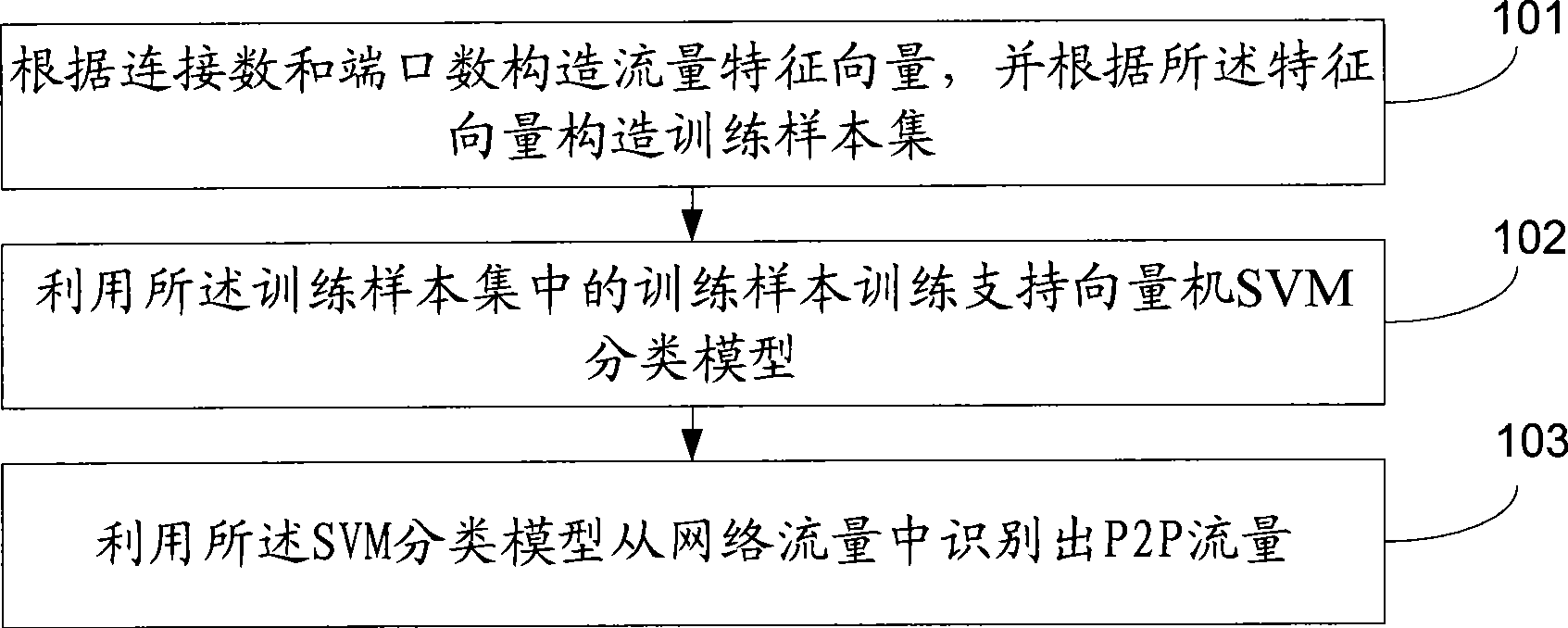
[0028] see figure 1 , the end-to-end traffic identification method provided by Embodiment 1 of the present invention includes the following steps:
[0029] Step 101: Construct a traffic feature vector according to the number of connections and ports, and construct a training sample set according to the feature vector.
[0030] Step 102: Using the training samples in the training sample set to train a support vector machine (SVM) classification model.
[0031] Step 103: Using the SVM classification model to identify P2P traffic from network traffic.
[0032] Through the method provided by the embodiment of the present invention, the traffic feature vector is constructed according to the number of connections and ports, and the constructed feature vector can reflect the P2P traffic characteristics of TCP and UDP, and then use the feature vector to construct a training sample set, and train the support vector machine classification model, and identify network traffic, because t...
Embodiment 2
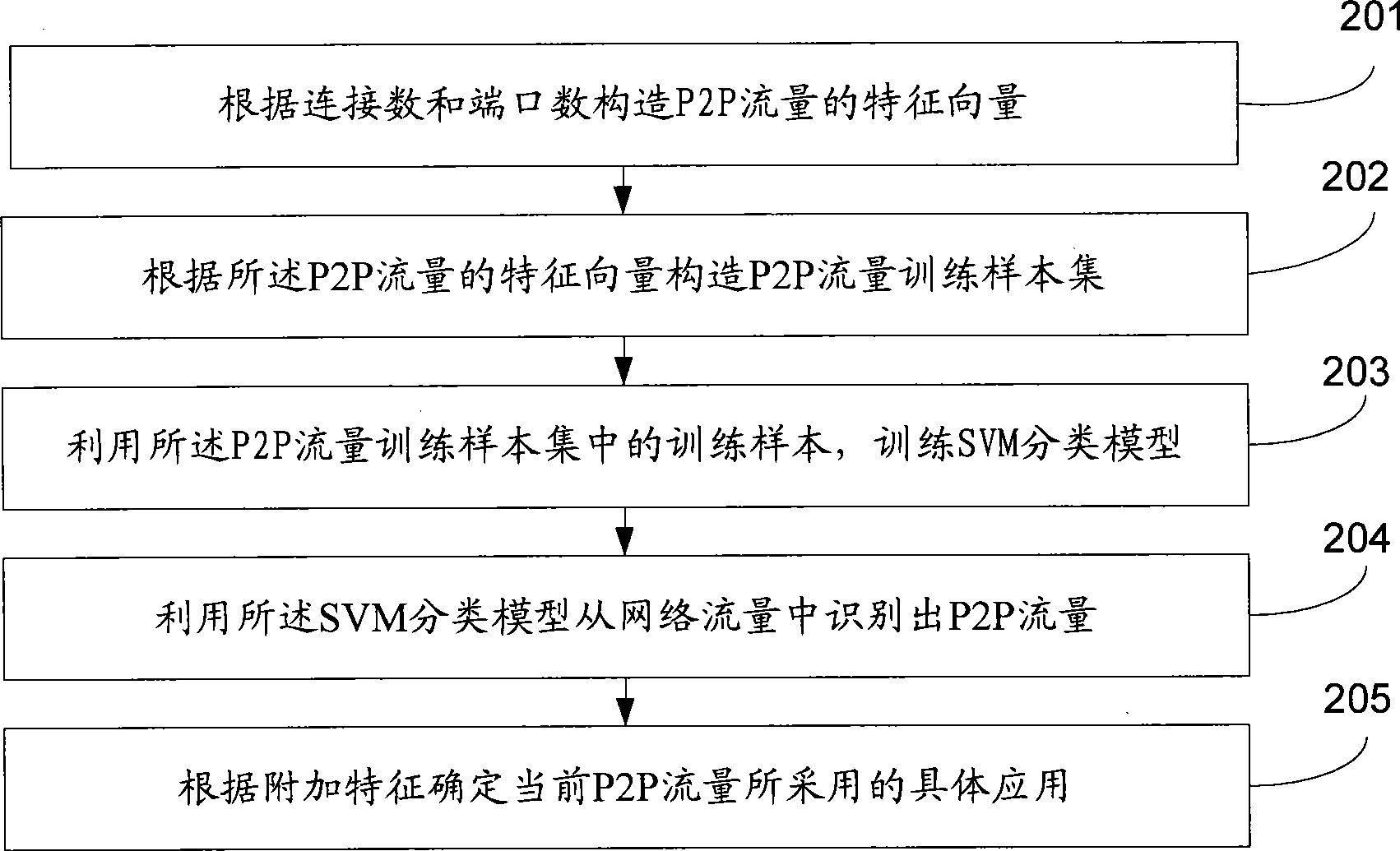
[0034] see figure 2 , the P2P traffic identification method provided by Embodiment 2 of the present invention includes the following steps:
[0035] Step 201: Construct a feature vector of P2P traffic according to the number of connections and ports.
[0036] By analyzing the difference between P2P traffic and non-P2P traffic, it can be seen that for P2P applications, a certain node is connected to multiple nodes or super nodes in the network, but the number of connections between two nodes is not many. To ensure the load balance of data transmission, the high load between two nodes can be avoided by limiting the number of connections between two nodes, and the communication pressure can be reduced; while for non-P2P applications, the performance between nodes in the network is that a certain node and A small number of nodes in the network are connected, but there are many connections between two nodes.
[0037] Constructing the feature vector of P2P traffic according to th...
Embodiment 3
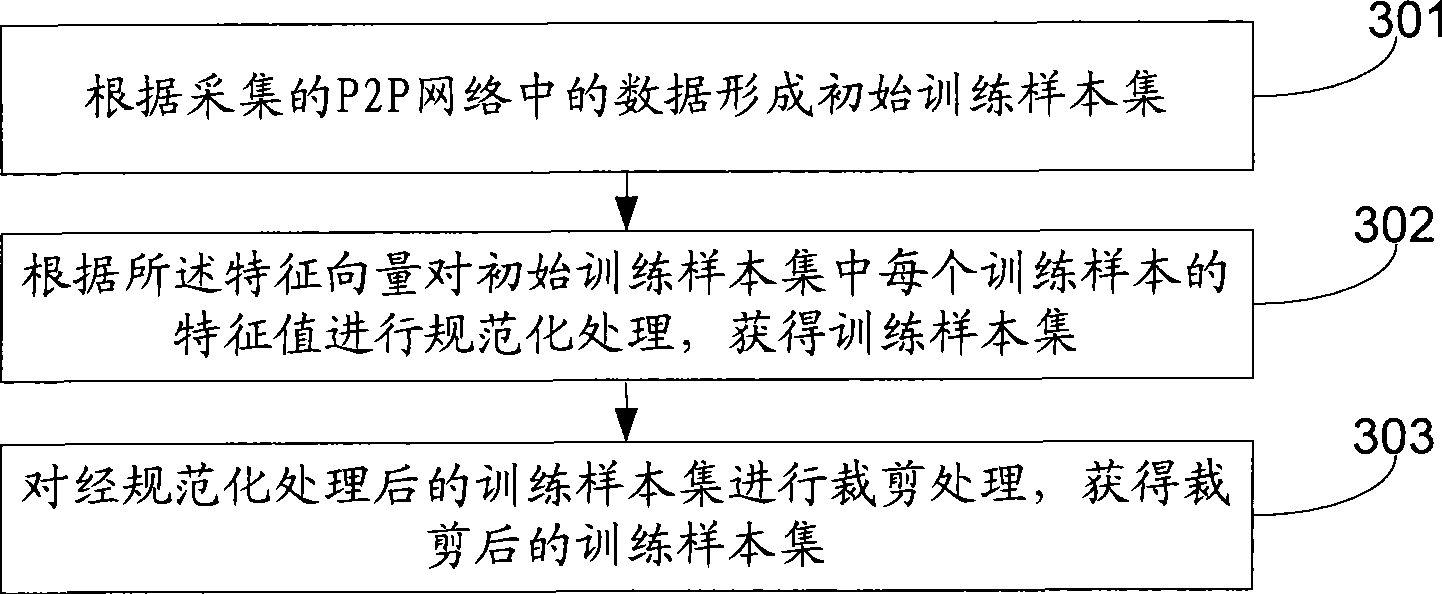
[0062] In order to establish the SVM classification model, it is necessary to collect a large amount of data on the network as training samples and test samples, but among these numerous samples, the support vectors are effective for establishing the classification model, and other training samples are not helpful to this, so you can Cut the training samples to reduce the size of the training sample set.
[0063] see Figure 4 , the present embodiment provides a clipping processing method, which can be used to clip the normalized training sample set to obtain the clipped training sample set. The clipping processing method includes:
[0064] Step 401: Select the first training sample set from the training sample set for training, and obtain the initial hyperplane of the initial classifier.
[0065] Assume that the training sample set is M, and randomly select a part of samples from M as the first training sample set N. According to the constructed feature vector, SVM training...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com