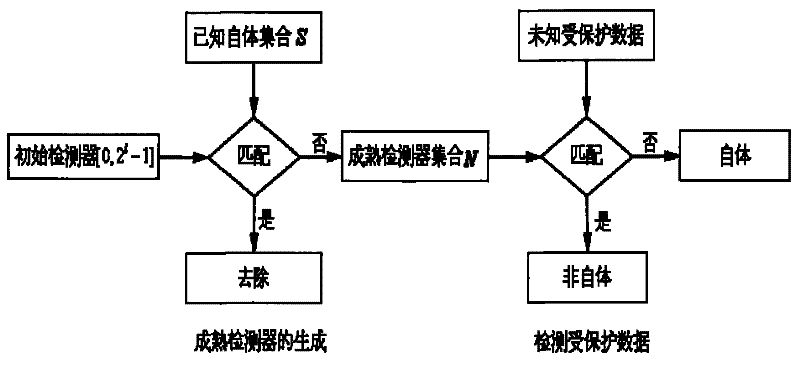
Generation of detectors and detecting method
A detector, a mature detector technology, applied in the fields of instruments, biological models, electrical digital data processing, etc., can solve the problems of low detector generation efficiency, difficult binary strings, redundant detectors, etc., to improve the generation efficiency and detection efficiency, improve comparison performance, and eliminate vulnerabilities.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0043] Further description will be given below in conjunction with the examples.
[0044]Known 32-bit binary self character string (assuming that the string contains all self bodies whose length is l): 00101000100100000100001010010011, divide it into subself character string sets S whose length is l=4,
[0045] S={0010, 0101, 1010, 0100, 1000, 0001, 0010, 0100, 1001, 0010, 0100, 1000, 0000, 0000, 0001, 0010, 0100, 1000, 0000, 0001,
[0046] 0010, 0101, 1010, 0100, 1001, 0010, 0100, 1001, 0011}.
[0047] Replacing the self-substring in the set S with a decimal number, the corresponding sub-self string set can be expressed as:
[0048] S={2, 5, 10, 4, 8, 1, 2, 4, 9, 2, 4, 8, 0, 0, 1, 2, 4, 8, 0, 1, 2, 5, 10, 4 ,9,2,4,9,3}
[0049] (1) Generation of detectors
[0050] Since the substring length l=4, the initial detector interval in binary form ranges from 0000 to 1111, ie [0, 15]. Figure 1 shows the initial detector R that conforms to the number field of the above example 1...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com