Method, device and system for securely transmitting and receiving pseudowire network data
A data security and receiving device technology, applied in the field of communication, can solve the problems of inability to realize security protection, non-IP/TCP messages cannot realize encrypted transmission, etc., and achieve the effect of wide application
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
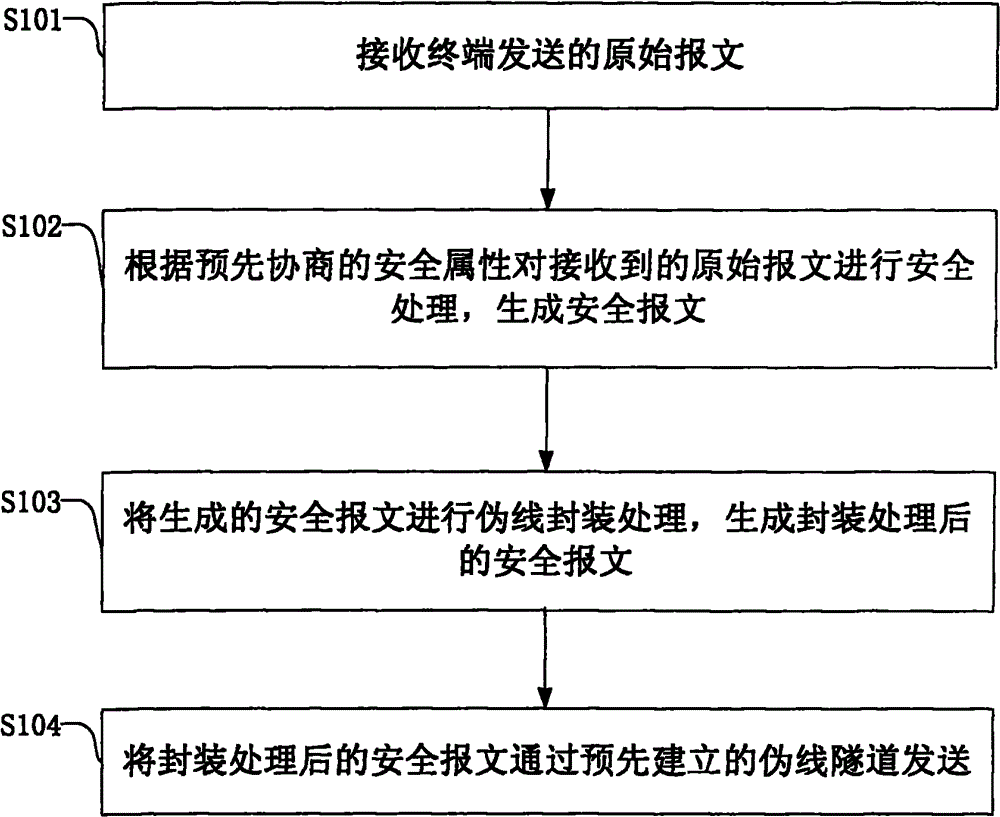
[0026] figure 1 It is a flow chart of a method for securely sending data in a pseudowire network provided by an embodiment of the present invention, as shown in figure 1 As shown, the methods described include:
[0027] S101. Receive an original packet sent by a terminal.
[0028] In the embodiment of the present invention, a typical PW network is used to illustrate how to establish a PW network with data security attributes when the PW is established. figure 2 It is a typical PW network structure diagram, such as figure 2 As shown, the terminal 201 establishes a PW connection with the terminal 204 through an attachment link 202 (AC, Attachment Circuit) and an attachment link 203 of another terminal 204 , wherein the AC 202 receives the original message sent by the terminal 201 .
[0029] S102. Perform security processing on the received original message according to the pre-negotiated security attribute to generate a security message. The secure processing of the receiv...
Embodiment 2
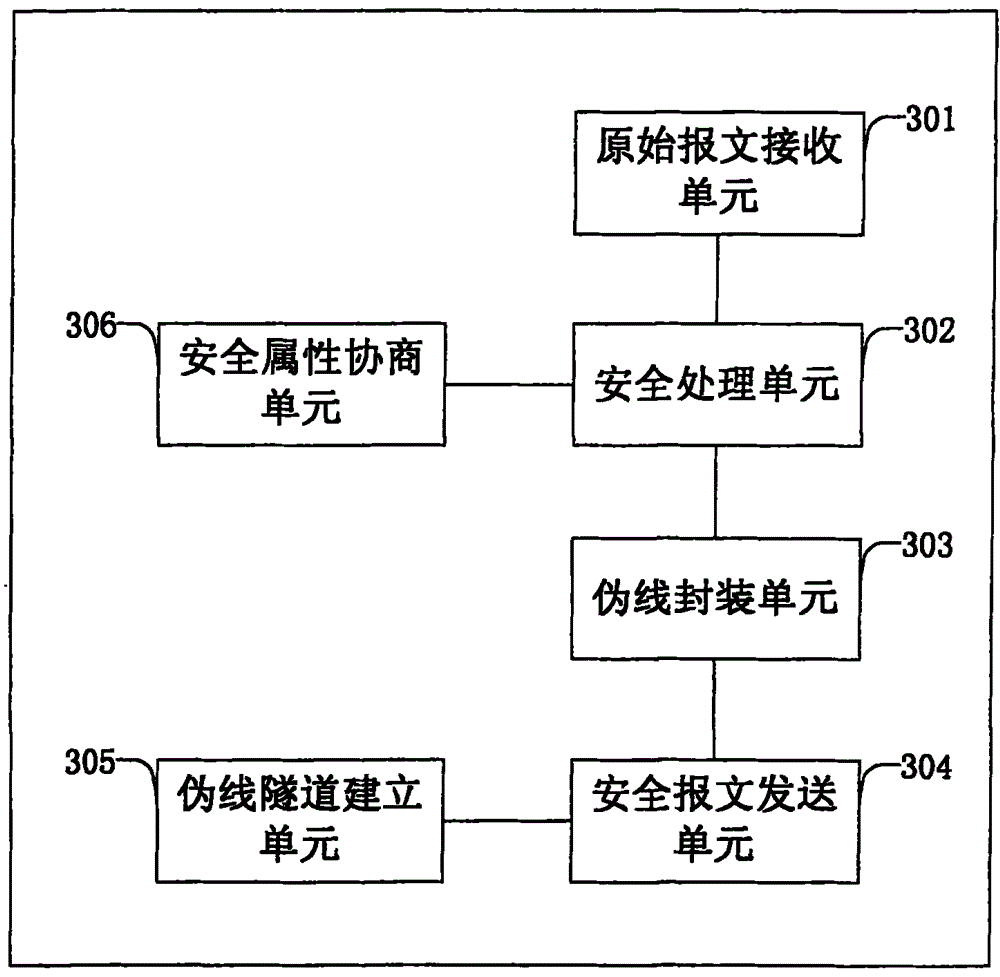
[0038] image 3 It is a block diagram of a data security sending device for a pseudowire network provided by an embodiment of the present invention, such as image 3 As shown, the described secure data sending device for a pseudowire network includes an original message receiving unit 301, a security processing unit 302, a pseudowire encapsulating unit 303, and a secure message sending unit 304, wherein:
[0039] The original message receiving unit 301 is configured to receive the original message sent by the terminal.
[0040] In the embodiment of the present invention, combined with figure 2 As shown, the device for securely sending data may be AC202, wherein the original message receiving unit 301 is configured to receive the original message sent by the terminal 201.
[0041] The security processing unit 302 is configured to perform security processing on the received original message according to the pre-negotiated security attributes, and generate a security message. ...
Embodiment 3
[0050] Figure 4 It is a flow chart of a data secure receiving method for a pseudowire network provided by an embodiment of the present invention, as shown in Figure 4 As shown, the methods described include:
[0051] S401. Receive the encapsulated security message through the pre-established pseudowire tunnel.
[0052] In the embodiment of the present invention, before step S401 receiving the encapsulated security message through the pre-established pseudo-wire tunnel, the method may include the step of establishing a pseudo-wire tunnel through negotiation. to combine figure 2 As shown, AC203 and AC202 establish a pseudowire tunnel through negotiation, and then AC203 receives an encapsulated security packet from AC202 through the established pseudowire tunnel.
[0053] S402. Perform pseudowire decapsulation processing on the received encapsulated security message to generate a decapsulated message.
[0054] In the embodiment of the present invention, AC203 performs pseu...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com