Secret key management method of IC card terminal
A technology of key management and terminal management system, which is applied in the direction of code identification card or credit card start-up, electrical components, transmission system, etc., which can solve the problems of unfavorable networking and high cost of update and maintenance, so as to improve versatility and reduce Maintenance update cost, effect of improving security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
specific Embodiment approach
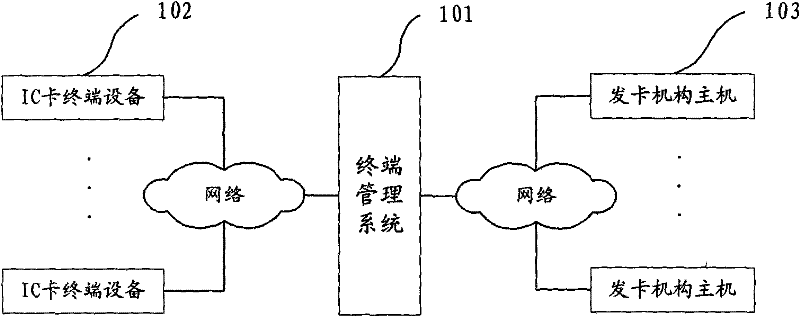
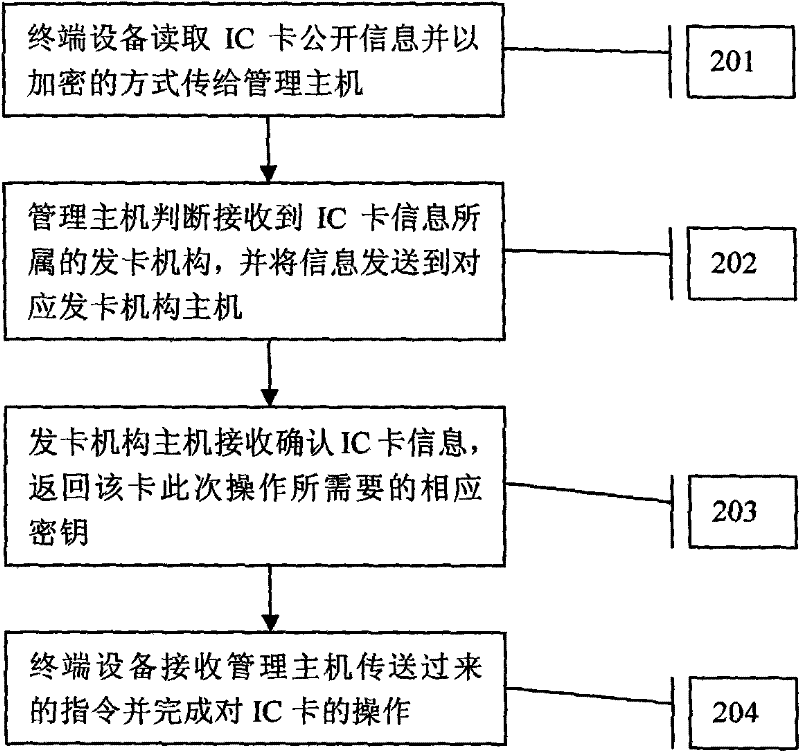
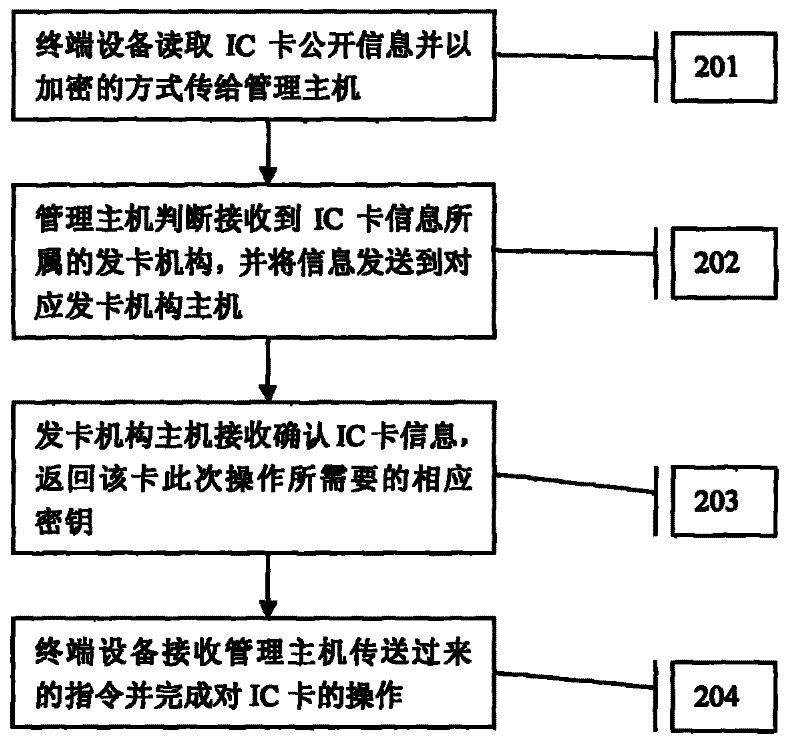
[0021] refer to figure 2 , is a flowchart of an embodiment of the present invention, specifically including the following steps:
[0022] Step 201: The terminal device reads the public information of the IC card and transmits it to the terminal management system host in an encrypted manner, hereinafter referred to as the management host.
[0023] The encrypted data transmitted between the terminal equipment and the management host in the present invention uses different process keys each time. The specific method is: for each transaction, the built-in security module of the terminal device generates a random number and a transaction sequence number to form a process factor, and uses the public key A agreed with the management host to disperse the process factor to generate a process key, and uses the process key Encrypt the transmission information to obtain the information ciphertext, and then use the public key B agreed with the management host to encrypt the process facto...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com