Device and method for protecting source code
A source code, code technology, applied in computer security devices, program/content distribution protection, instruments, etc., can solve problems such as complex processes
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
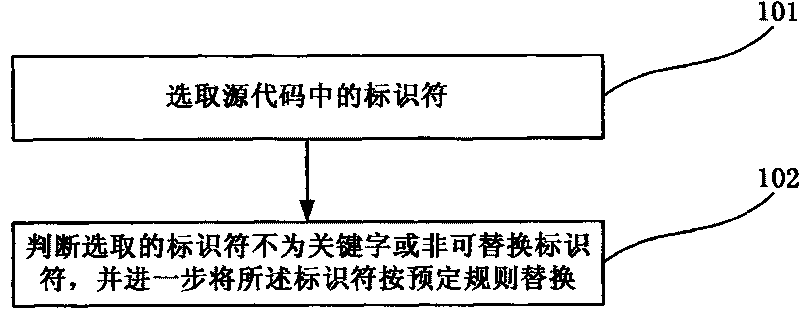
[0021] The present invention will be further described in detail below in conjunction with the accompanying drawings, so that those skilled in the art can implement it with reference to the description.
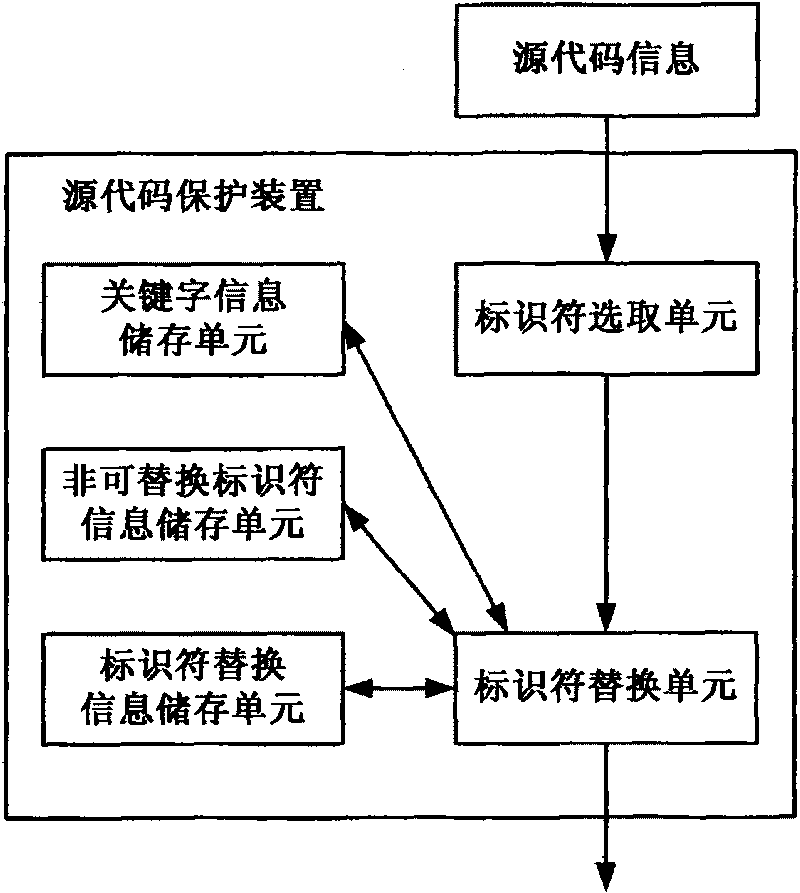
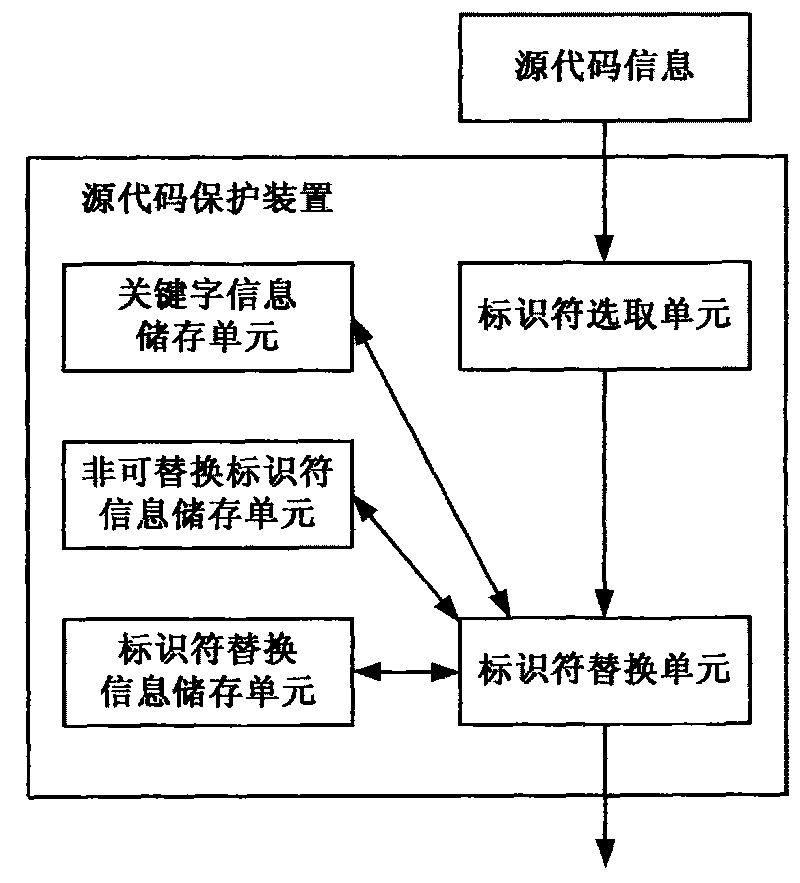
[0022] The source code protection device of the present invention, such as figure 1 shown, including:
[0023] Keyword information storage unit, non-replaceable identifier information storage unit, identifier replacement information storage unit, identifier selection unit, and identifier replacement unit.
[0024] Wherein, the keyword information storage unit is used for storing preset keyword information in the source code, generally speaking, the keyword in the source code is not allowed to be replaced.
[0025] The non-replaceable identifier information storage unit is used for storing non-replaceable identifier information in the preset source code. Generally speaking, the identifiers corresponding to the preset non-replaceable identifier information cannot be replaced....
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com