Notebook computer with hardware safety protection
A notebook computer, hardware security technology, applied in computer security devices, internal/peripheral computer component protection, electrical digital data processing and other directions, can solve network camera protection measures, threats, dangers and other issues
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
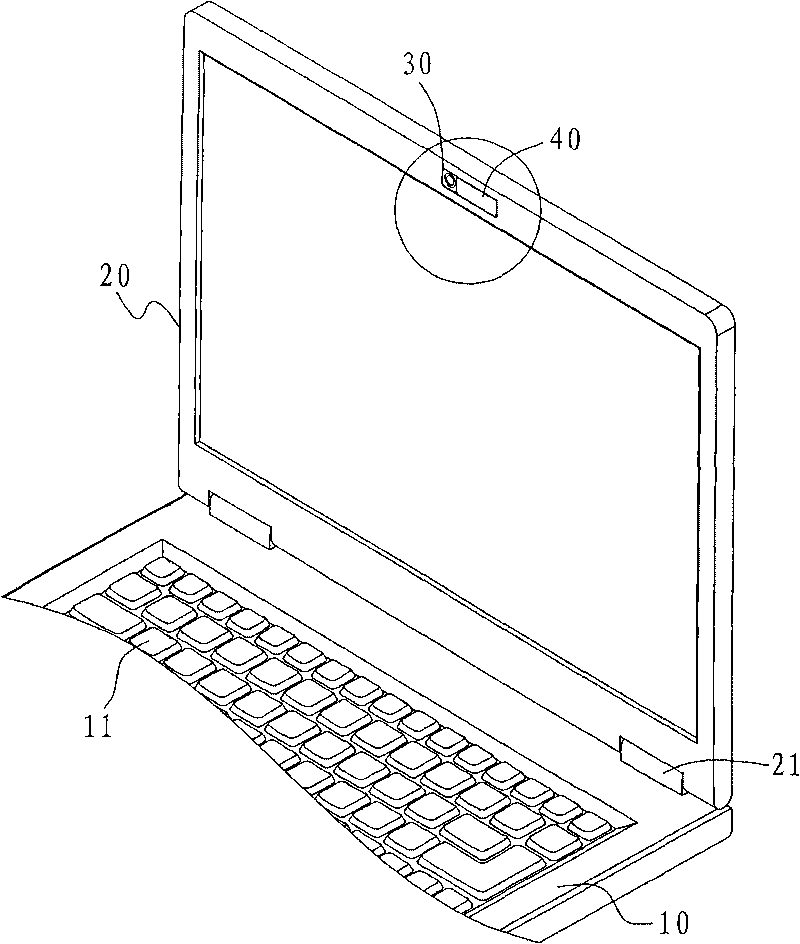
[0024] According to the notebook computer with hardware safety protection disclosed by the present invention, please refer to figure 1 As shown, it is a schematic diagram of a notebook computer with hardware security protection according to the present invention.
[0025] The notebook computer with hardware security protection disclosed by the present invention includes a host 10, a display 20, an image capture module 30, and a cover 40. The host 10 has electronic components such as a motherboard, a central processing unit, a control chipset, and a hard disk. , and can perform calculations on electronic data, audio-visual data, etc., and there is a keyboard set 11 on the outside for the user to input various information or instructions; When the host 10 is turned over and closed or opened, as shown in the figure, it is in an open state.
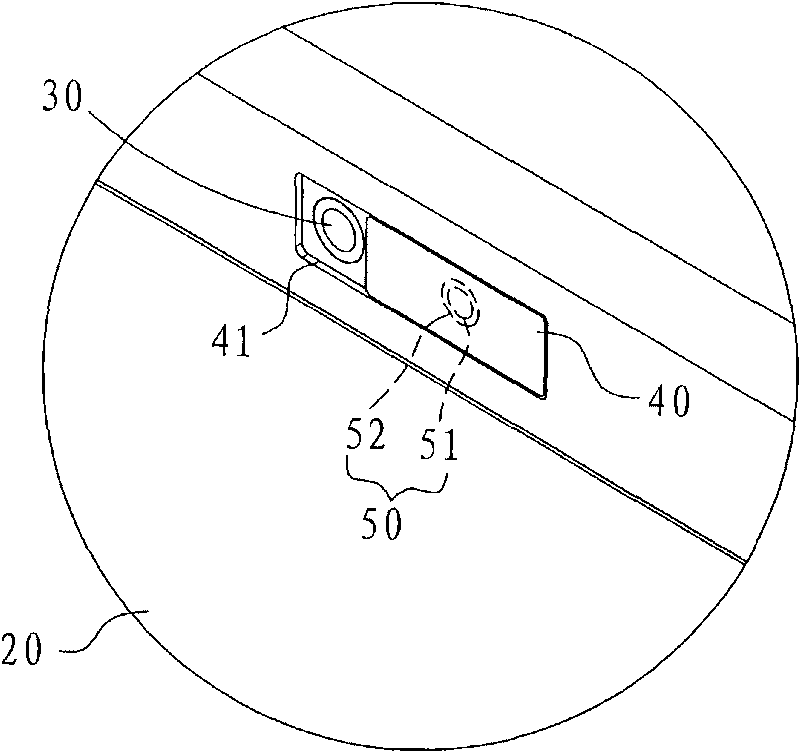
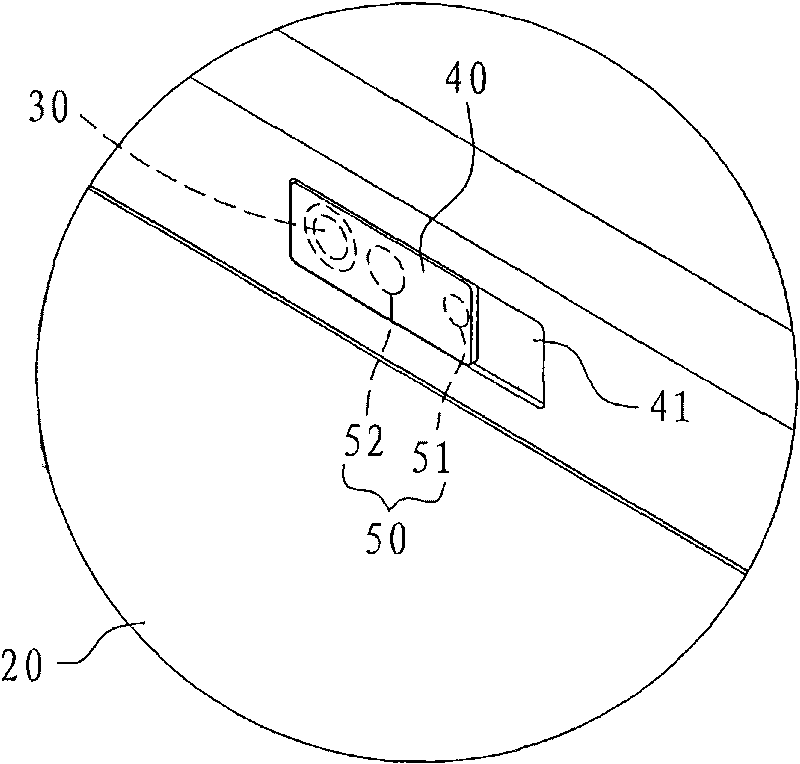
[0026] The image capture module 30 is located on the display 20. As shown in the figure, it is located on the top of the display 20, which ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com