Construction method for access control policy and system thereof
A technology of access control strategy and construction method, which is applied in the field of access control strategy construction and its system, which can solve the problems of lack of structure in language, complex policy rules, and inability to provide semantic analysis, so as to facilitate unified writing and management, and improve readability Sexuality, easy to understand the effect of using
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
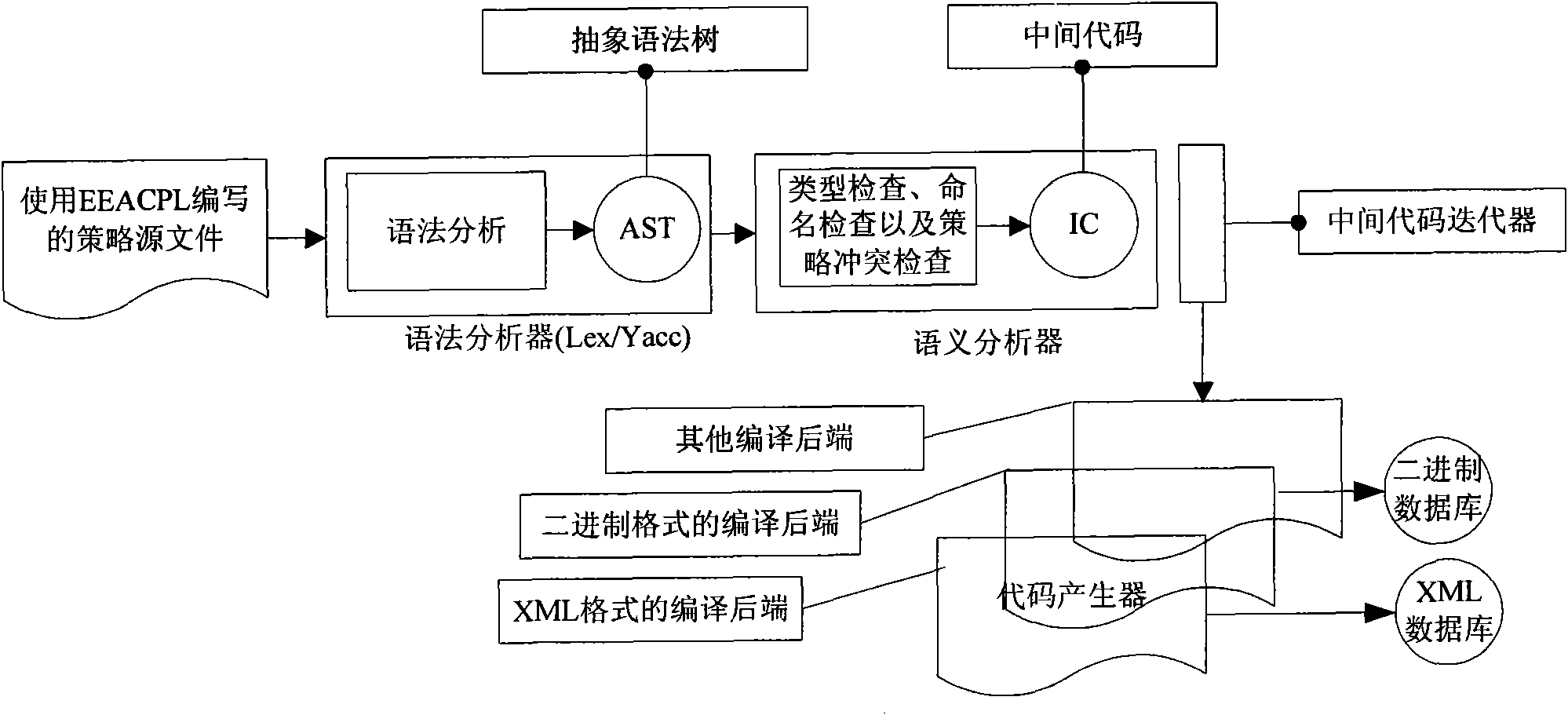
[0023] Based on the study of existing access control technologies and security models, such as BLP, DTE and RBAC models, this embodiment comprehensively analyzes the security principles of these models, extracts their common and unique security features, and analyzes the model Realize the abstraction and summary, and refine the design requirements of the general access control strategy.
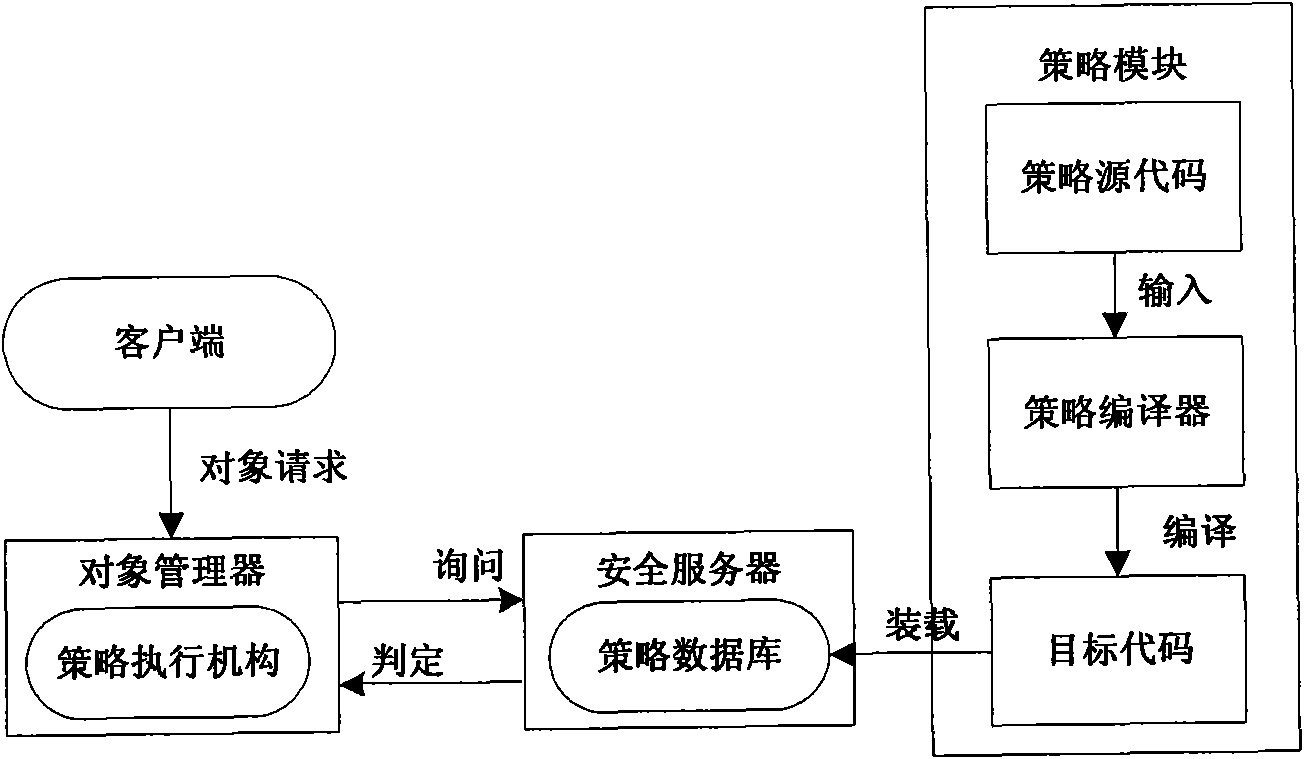
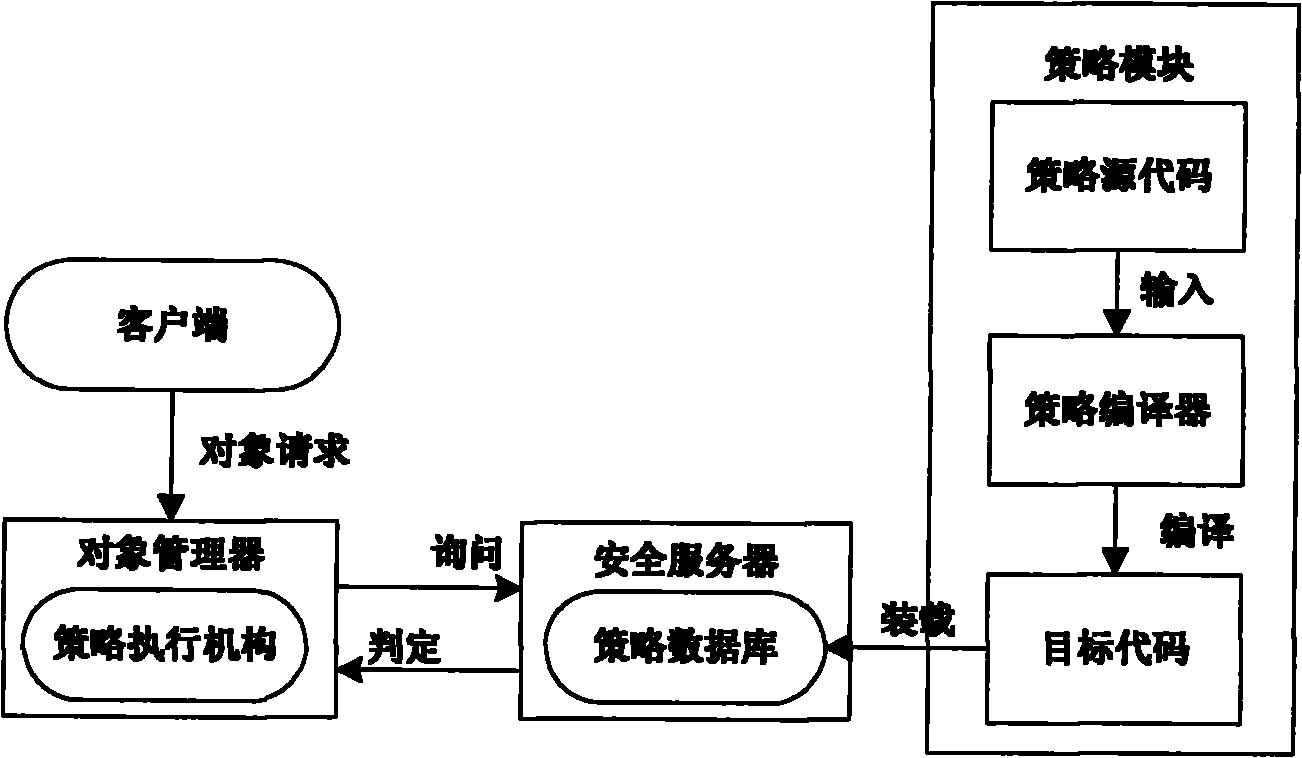
[0024] The access control policy is the realization basis of the security model, the specific description of the abstract security model, and the actual description object of the access control policy language. Generally speaking, access control policies mainly have three basic elements: policy subjects, policy objects and policy rules. These elements correspond to the system security field and can be divided into three basic concepts of system subject, system object and security rules. The system subject can be a policy subject or a policy object, which means a system object that can active...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com