Data processing method and data processing system for verification
A data processing system and data processing technology, applied in the field of commodity or logistics authenticity verification, can solve the problem that anti-counterfeiting objects cannot effectively verify the authenticity of anti-counterfeiting items, and achieve the effects of accurate and reliable detection results and simple and fast detection process.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
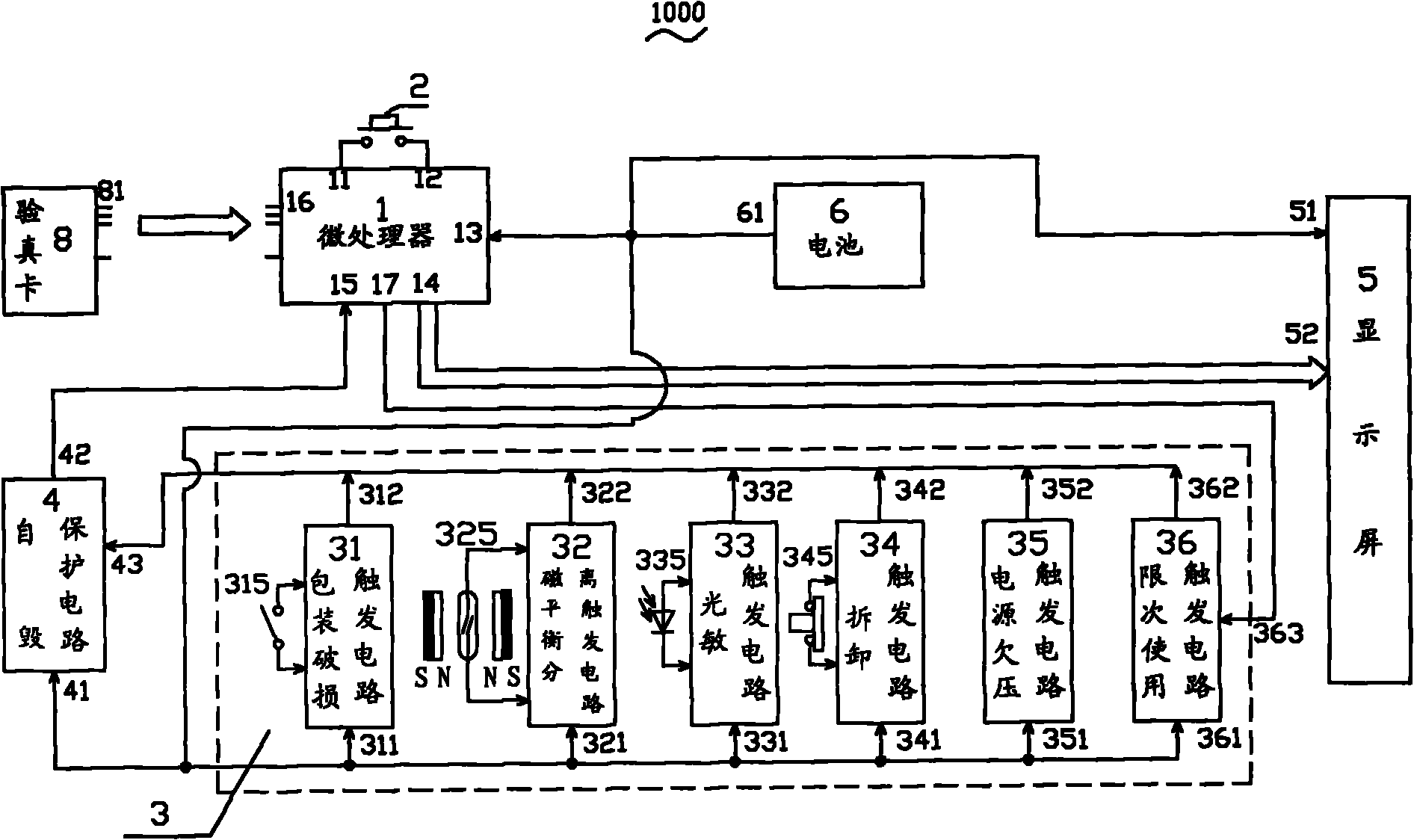
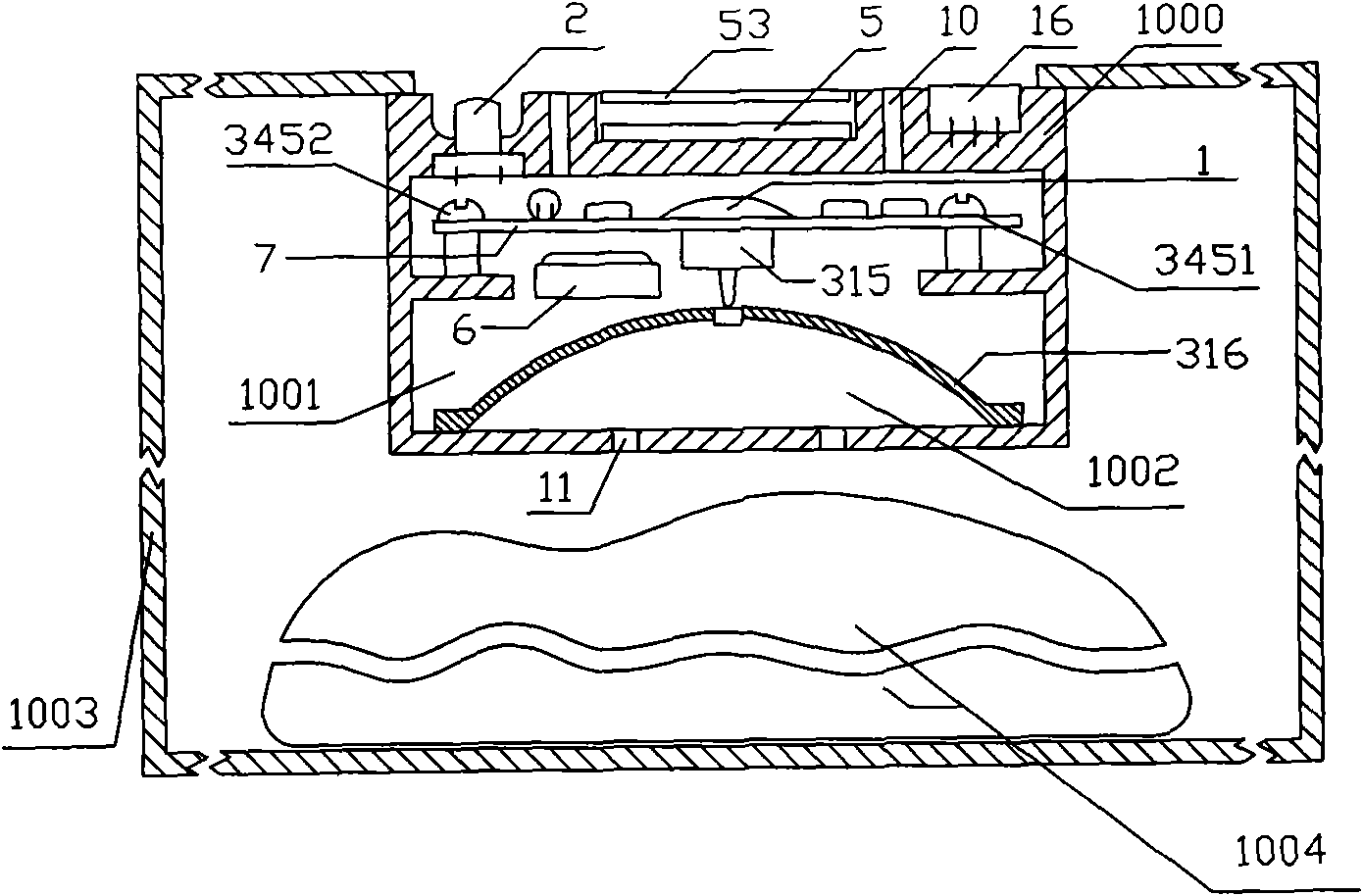
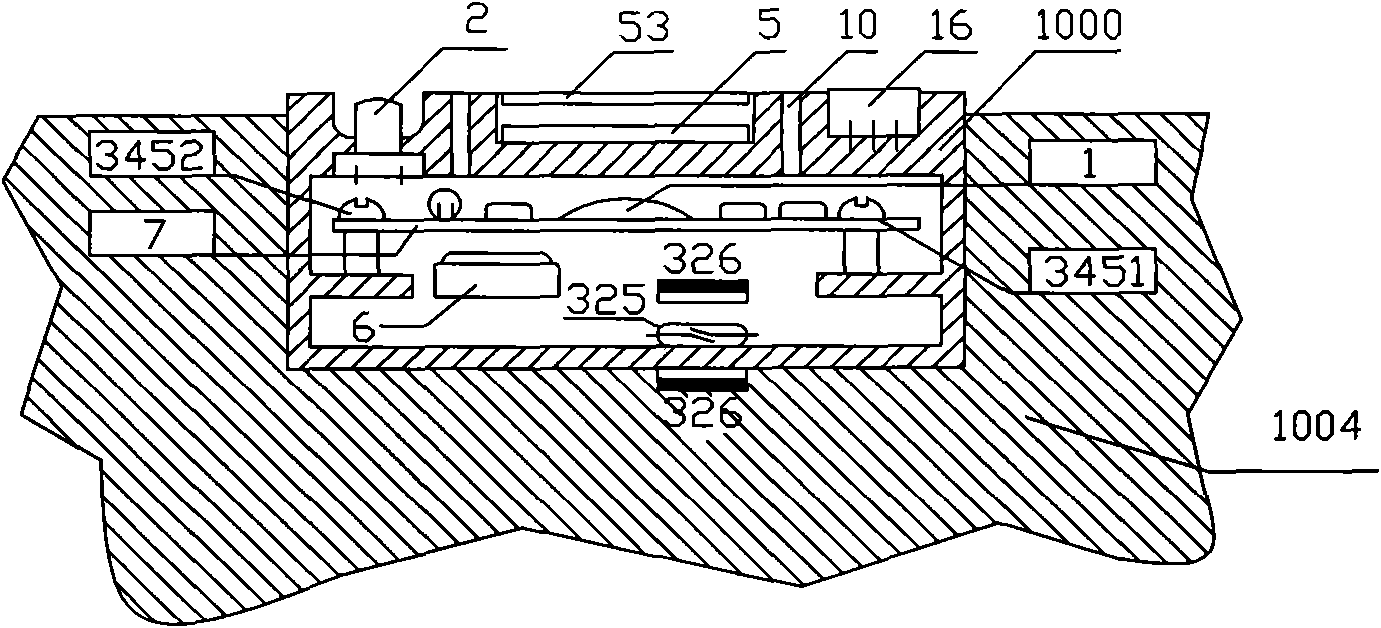
[0024] The present invention will be further described below in conjunction with the accompanying drawings and embodiments.
[0025] The design principle of the present invention is as follows: there are many anti-counterfeiting means in the market, but the anti-counterfeiting effect obtained is getting worse and worse. The packaging materials and anti-counterfeit stickers, logos, signs, anti-counterfeit query code stickers, etc. of individual materials and structures used in the existing anti-counterfeiting methods are attached to the body of the anti-counterfeiting commodity. All present in front of counterfeiters are in a state of being counterfeit and out of control. Anti-counterfeiting objects cannot simultaneously have the three major elements of being unique to authentic products, cannot be copied or imitated, and cannot be reused after leaving the genuine product. loophole. Therefore, counterfeiters can easily copy or imitate the above-mentioned anti-counterfeit produ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com