Network security quantitative estimation method based on network topology characteristic
A network security and network topology technology, applied in the field of network security, can solve problems such as ignoring network topology characteristics, and achieve the effect of eliminating information overlap
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
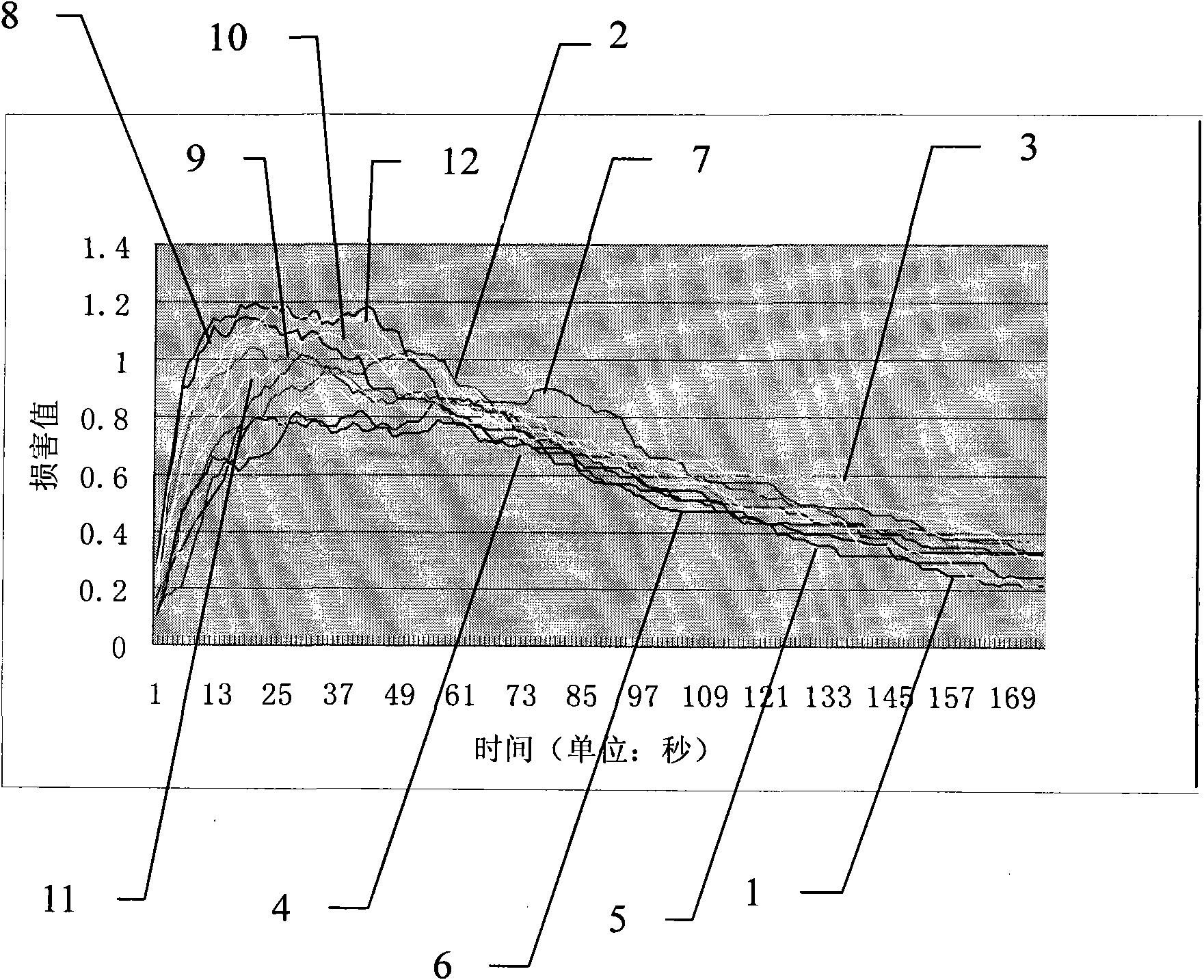
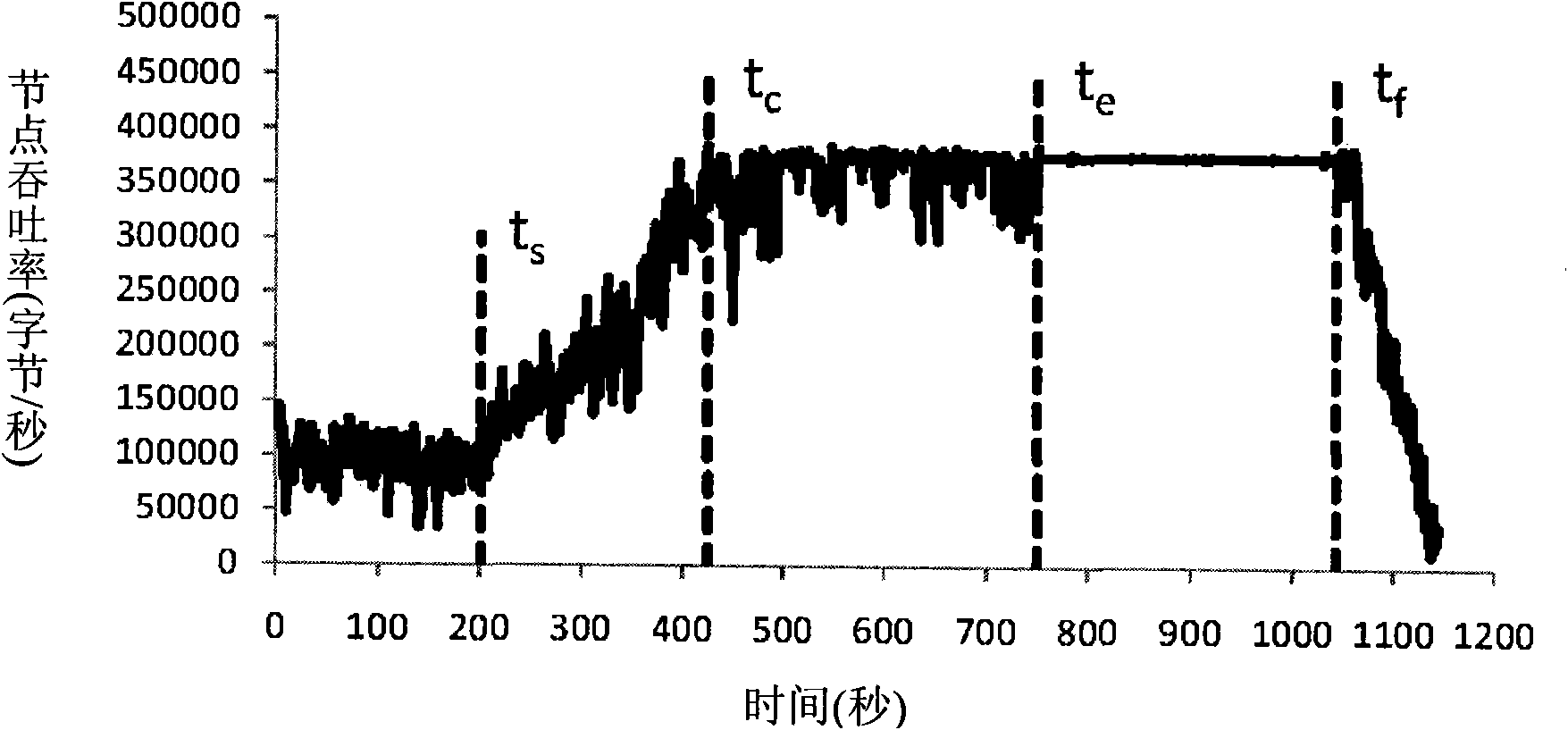
Image
Examples
specific Embodiment approach 1
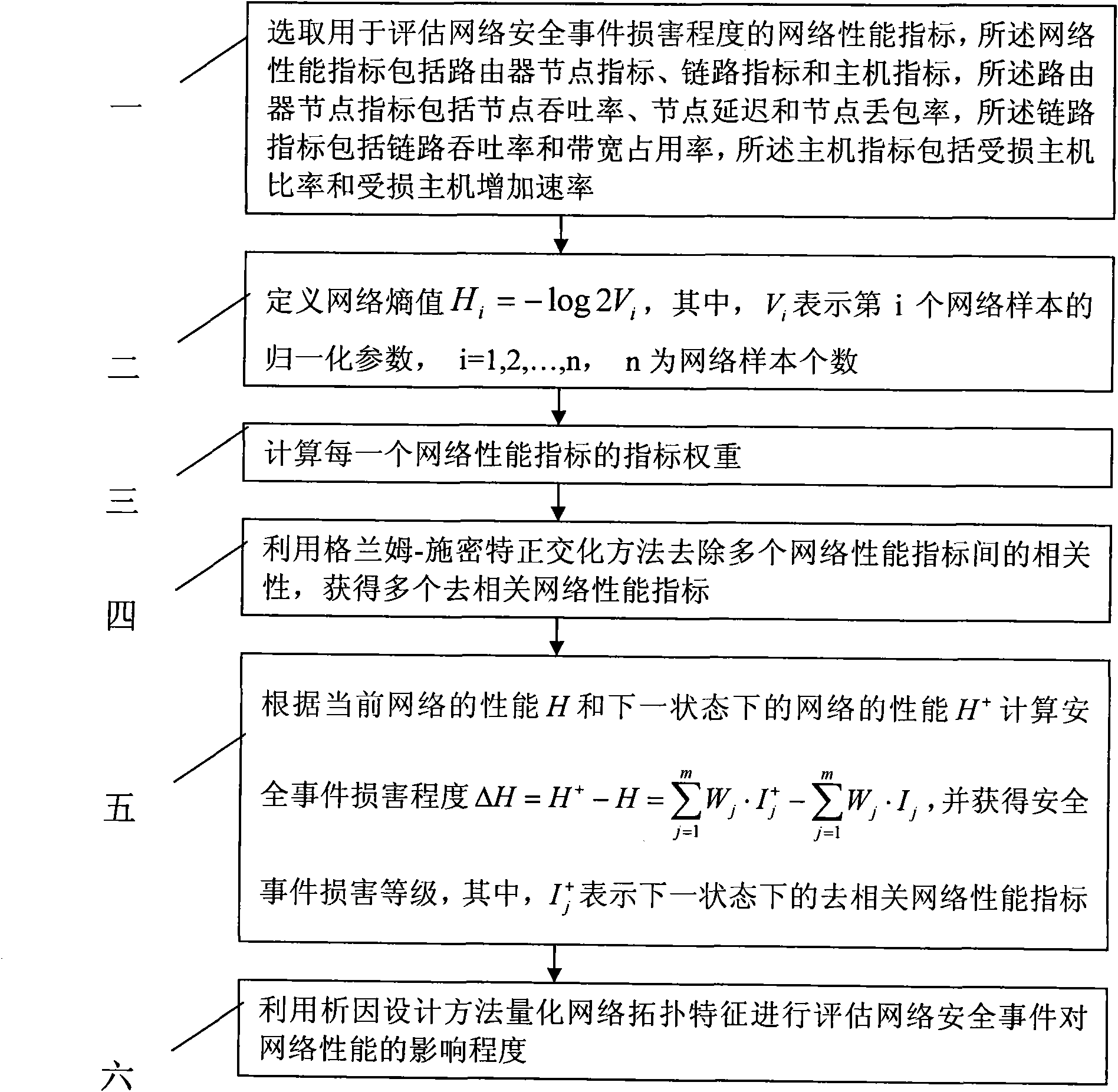
[0013] Specific implementation mode one: according to the instructions attached figure 1 Specifically explain this embodiment, a network security quantitative evaluation method based on network topology characteristics described in this embodiment, its evaluation process is:
[0014] Step 1: Select network performance indicators for assessing the damage degree of network security incidents, the network performance indicators include router node indicators, link indicators and host indicators, and the router node indicators include node throughput, node delay and node packet loss rate, the link index includes link throughput and bandwidth occupancy rate, and the host index includes damaged host ratio and damaged host increase rate;
[0015] Step 2: Define the network entropy value H i =-log2V i , where V i Represent the normalization parameter of the i-th network sample, i=1, 2,..., n, n is the number of network samples;
[0016] Step 3: Calculate the index weight of each n...
specific Embodiment approach 2
[0020] Embodiment 2: This embodiment is a further description of Embodiment 1. In Embodiment 1, in step 3, the method for calculating the index weight of each network performance index is:
[0021] Step 31: Establish a judgment matrix R about m network performance indicators and n network samples m×n =(xij), where xij represents the i-th network sample of the j-th index;
[0022] Step 32: Preprocessing each network sample to obtain the normalized sample value bij of the network sample xij;
[0023] Step 33: According to the network entropy value H i Obtain the entropy value of network performance indicators for m network performance indicators and n network samples H i n = - 1 ln m ( Σ j = 1 m f ij ...
specific Embodiment approach 3
[0026] Embodiment 3: This embodiment is a further description of Embodiment 1 or 2. In Embodiment 1 or 2, in step 4, multiple network performance indicators are removed by Gramm-Schmidt orthogonalization method The method of obtaining multiple decorrelation network performance indicators is as follows:
[0027] Step 41: Define m network performance indicators as I * 1 , I * j ......, I * m , and satisfy the following formula:
[0028] Formula 1: I 1 = I * 1 ,
[0029] Formula 2: I j = I * j -h j,j-1 I * j-1 -...-h j,1 I* 1 ,
[0030] Among them, h j,j-1 ,...,h j,1 are undetermined constants;
[0031] Step 42: Solve Formula 3 to obtain the specific values of each undetermined constant, and bring the specific values of each undetermined constant into Formula 2 to obtain the de-correlation network performance index I j ,
[0032] Formula 3: Cov(I j , I j-1 ) = Cov(I j , I j-2 )=...=Cov(I j , I 1 )=0.
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com