Method for safely transmitting physical activity monitoring data
A technology for safe transmission and motion monitoring, applied in the field of human motion monitoring data transmission, can solve the problem of not providing user monitoring, and achieve the effect of improving physical fitness
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment approach
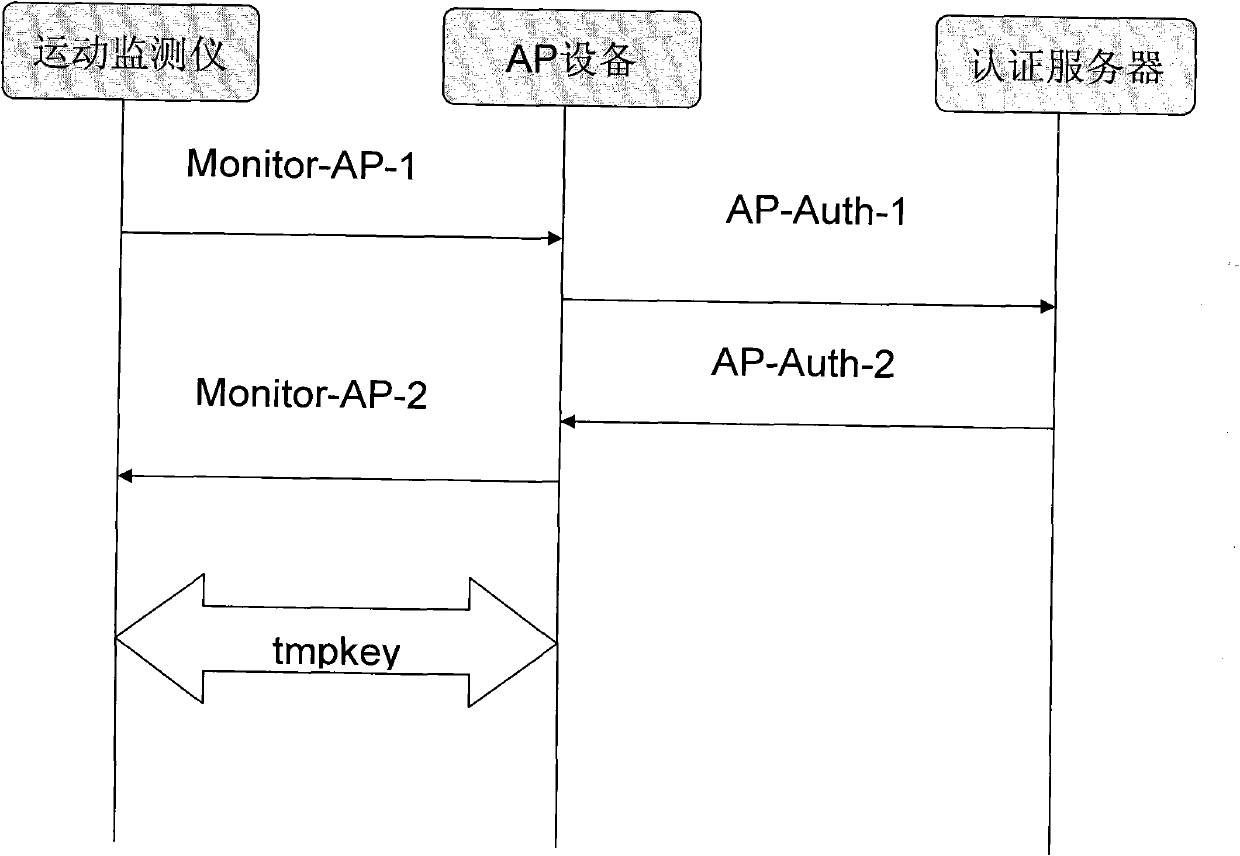
[0053] The following examples illustrate the specific implementation, see image 3 :
[0054] 1) After the Monitor device establishes a communication channel with the AP, it sends a message Monitor-AP-1 to the AP. The format of Monitor-AP-1 is as follows:
[0055] Monitor-AP-1 = MonitorID, EncMonitor_key(tmpkey, Monitor_time, MonitorID, ch).
[0056] Where MonitorID is the identification number of the Monitor device, ch is a random number randomly generated by the Monitor, and tmpkey is a random key generated by the Monitor.
[0057] 2) Since the AP does not have the key Monitor_key of the Monitor device, it cannot decrypt it, and generates a message AP-Auth-1 to the Monitor authentication server. The format of AP-Auth-1 is as follows:
[0058] AP-Auth-1 = Monitor-AP-1.
[0059] 3) The authentication server first authenticates the AP (that is, the user User). After the authentication is successful, it shares a key session_key with the AP. The authentication server queries t...
specific Embodiment approach
[0082] 1. Registration process
[0083] 1) The user registers his user name in AuthServer, sets a password, and is assigned the unique PID of the system. AuthServer saves the key User_key shared with the user.
[0084] 2) The application server AppServer also registers its own service Service with AuthServer, and shares a key Server_key with AuthServer.
[0085] 2. AP obtains Ticket from AuthServer
[0086] 1) When the user logs in from the AP, the user provides the user name, PID, password, and the application service to be used. The AP generates the user key User_key according to the user name, PID, and password, generates a random number Nonce, and combines it into a message AP-AuthServer- 1 to AuthServer, the format of AP-AuthServer-1 is as follows:
[0087] AP-AuthServer-1 = PID, Service, Nonce, AP_time, Hmac User_Key (PID, Service, Nonce, AP_time)
[0088] 2) AuthServer receives AP-AuthServer-1, decrypts the encrypted part, and verifies whether the data packet is cor...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com