Method for realizing mobile terminal to lock network or card by utilizing driver
A technology of mobile terminal and mobile network code, which is applied in network data management, wireless communication, electrical components, etc. It can solve problems such as abnormal use, low security, and easy leakage of secrets, so as to prevent illegal unlocking and improve security. Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
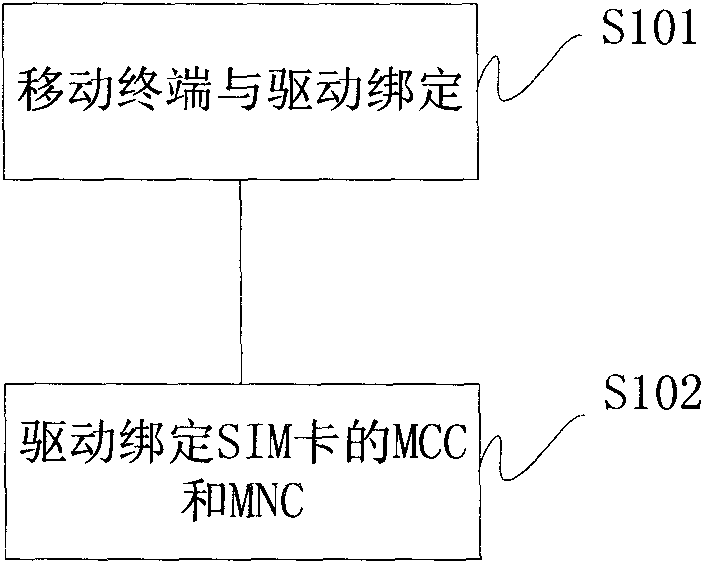
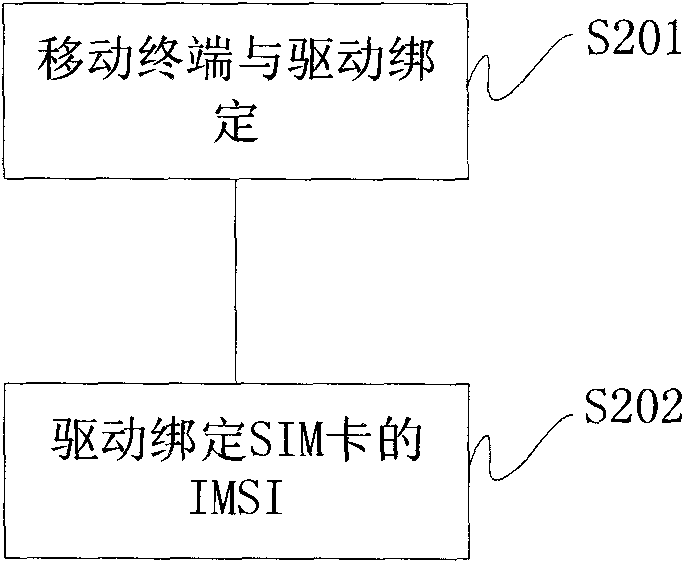
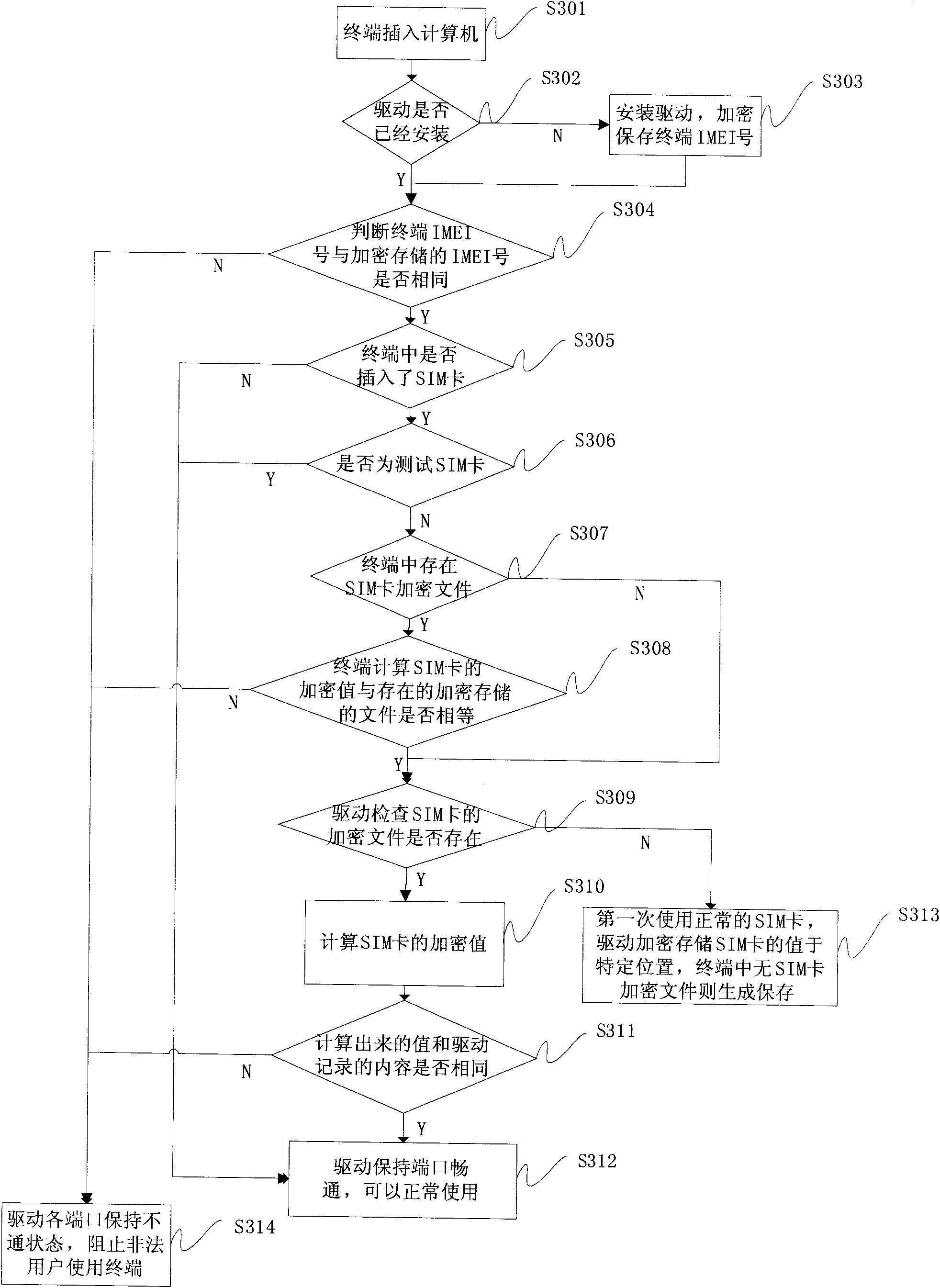
[0023] This patent proposes a method of using the driver to realize network lock and card lock. Firstly, the binding relationship between the driver and the terminal is realized, that is, the driver only guarantees smooth communication with one terminal port, and the terminal can be used normally with the support of this driver, and other terminals Under this drive, hackers are prevented from cracking the terminal action because the port is unreachable; then use the terminal and the driver to double bind the country code (Mobile Country Code, hereinafter referred to as MCC) and mobile network code (Mobile Network Code, hereinafter referred to as MNC) of the user's SIM card , that is, only this type of SIM card can guarantee the normal use of the driver, thereby realizing the network lock. If the driver is bound with the International Mobile Subscriber Identification number (IMSI) of the SIM card, the card can be locked. Since the method first uses the driver to bind the termina...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com