Asymmetrical group encryption/decryption method based on user identity identification
A user identification and identification technology, applied in the field of asymmetric group encryption and decryption, can solve the problem of low computing efficiency of multicast encryption technology, and achieve the effect of improving encrypted communication efficiency, ensuring static security, and ensuring dynamic security.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0021] In order to make the object, technical solution and advantages of the present invention clearer, the present invention will be further described in detail below with reference to the accompanying drawings and examples.
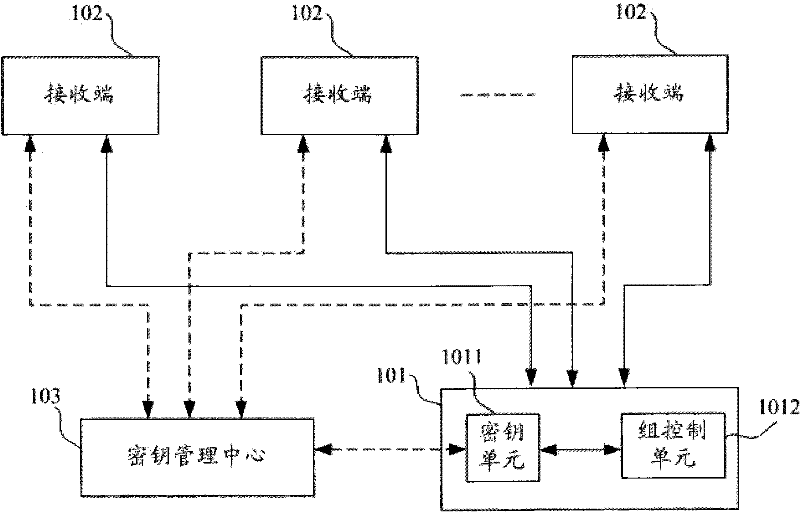
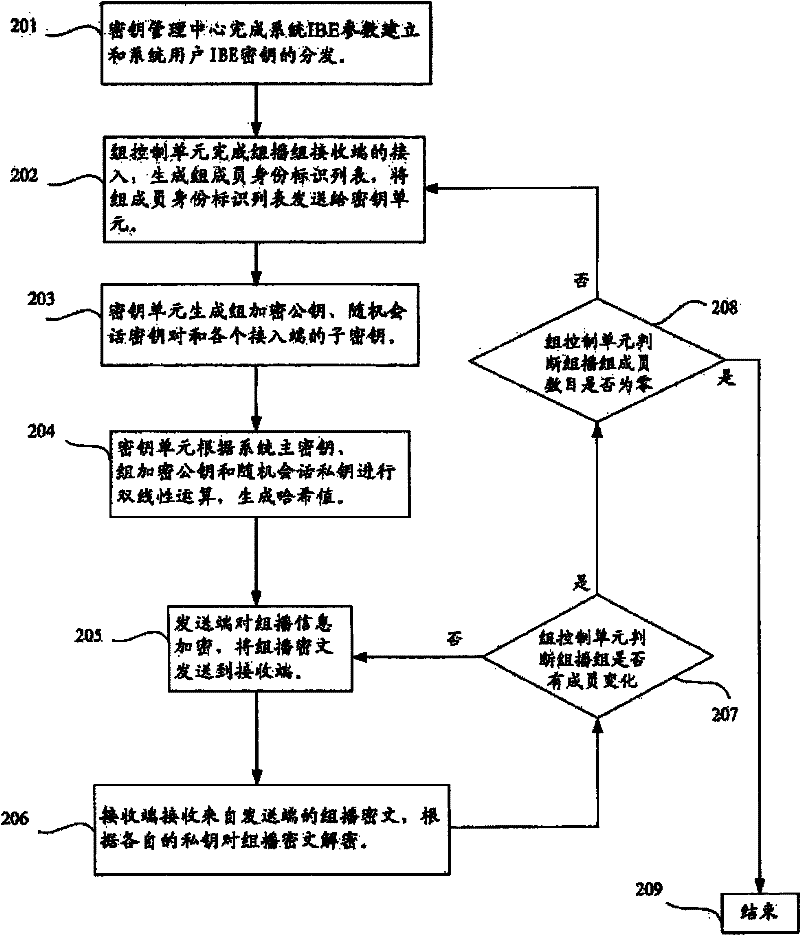
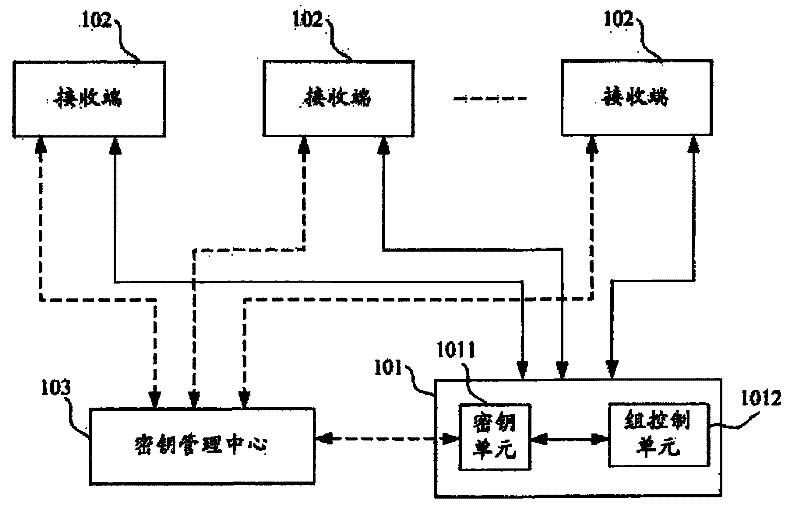
[0022] figure 1 It is a structural diagram of the multicast system adopting the asymmetric group encryption and decryption method based on the user identity of the present invention, wherein the dotted line shows the IBE key generation interaction process, and the solid line shows the group encryption and decryption information interaction process, the group The encryption and decryption information is group joining request information, group member identification information, multicast information, and the like. Such as figure 1 As shown, the multicast system includes system users and a key management center 103 . Wherein, the system user includes a sending end 101 and multiple receiving ends 102 , and the sending end 101 includes a key unit 1011 and...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com