Dynamic detection method for cross-site forged request
A technology of forged requests and dynamic detection, applied in the field of CSRF vulnerabilities, can solve problems that affect the performance of web applications and are difficult to implement, and achieve high test efficiency, accuracy, and high efficiency
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
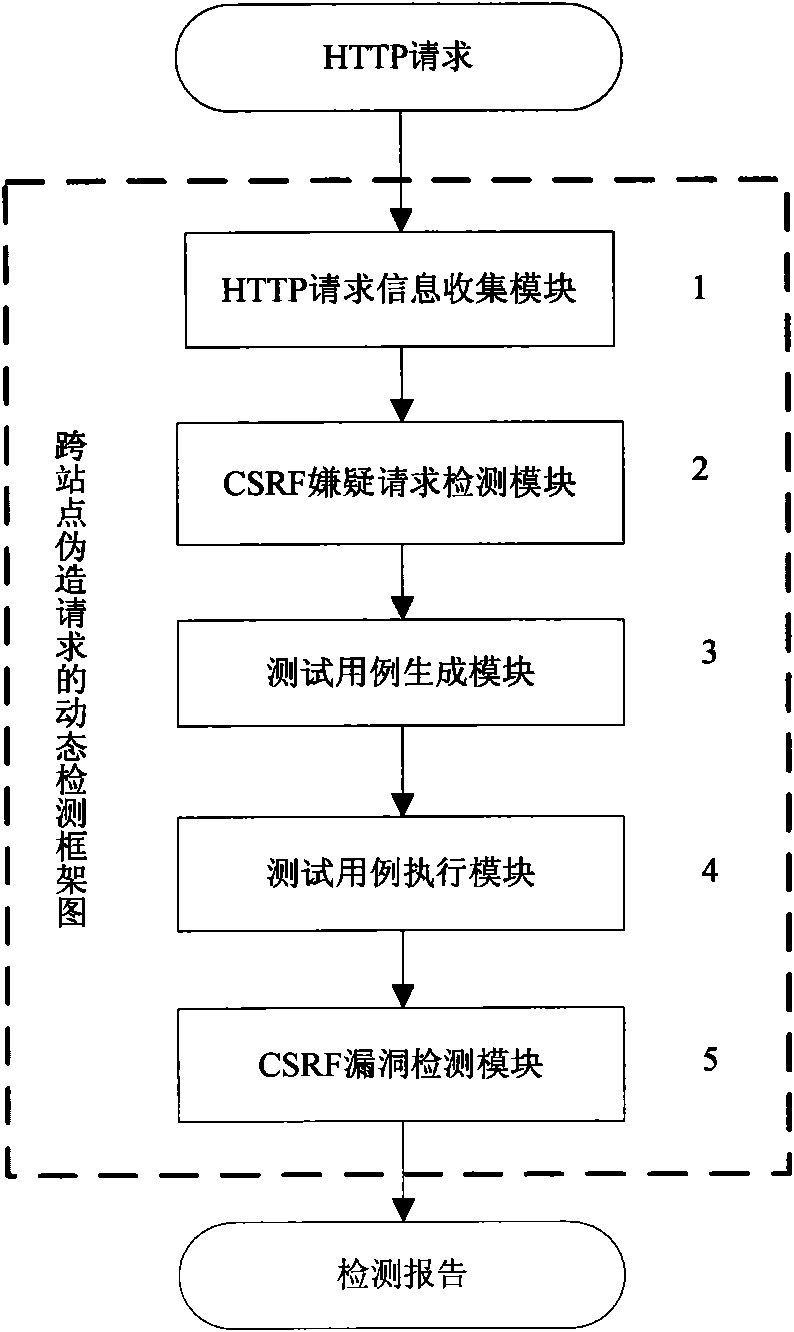
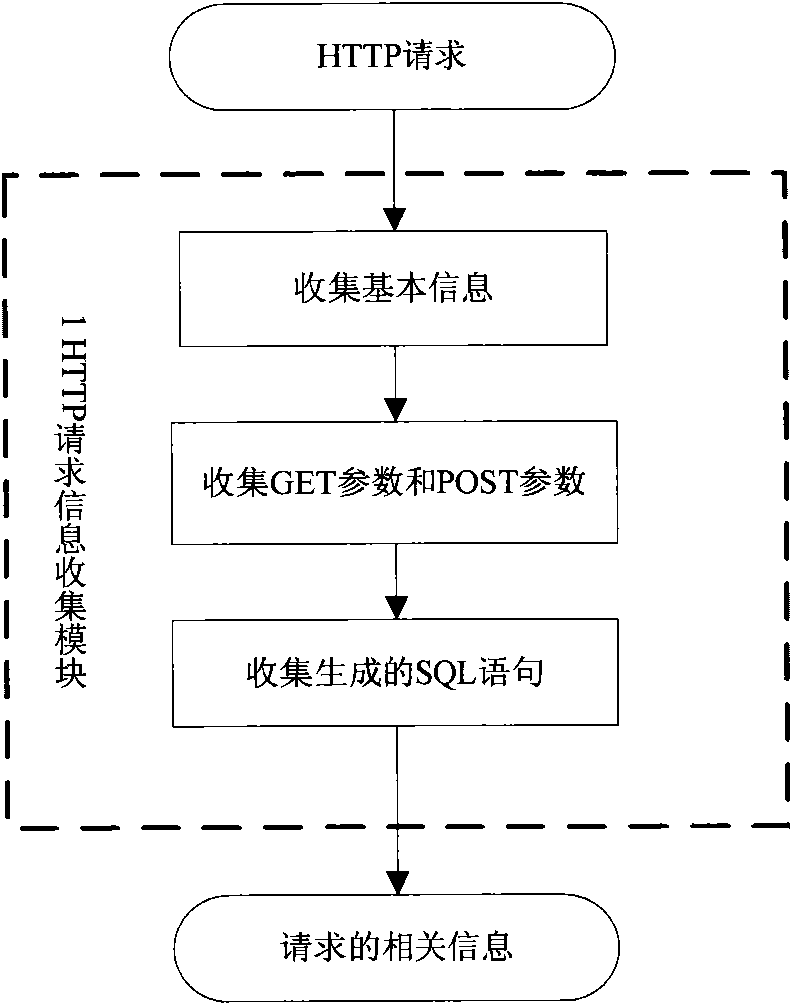
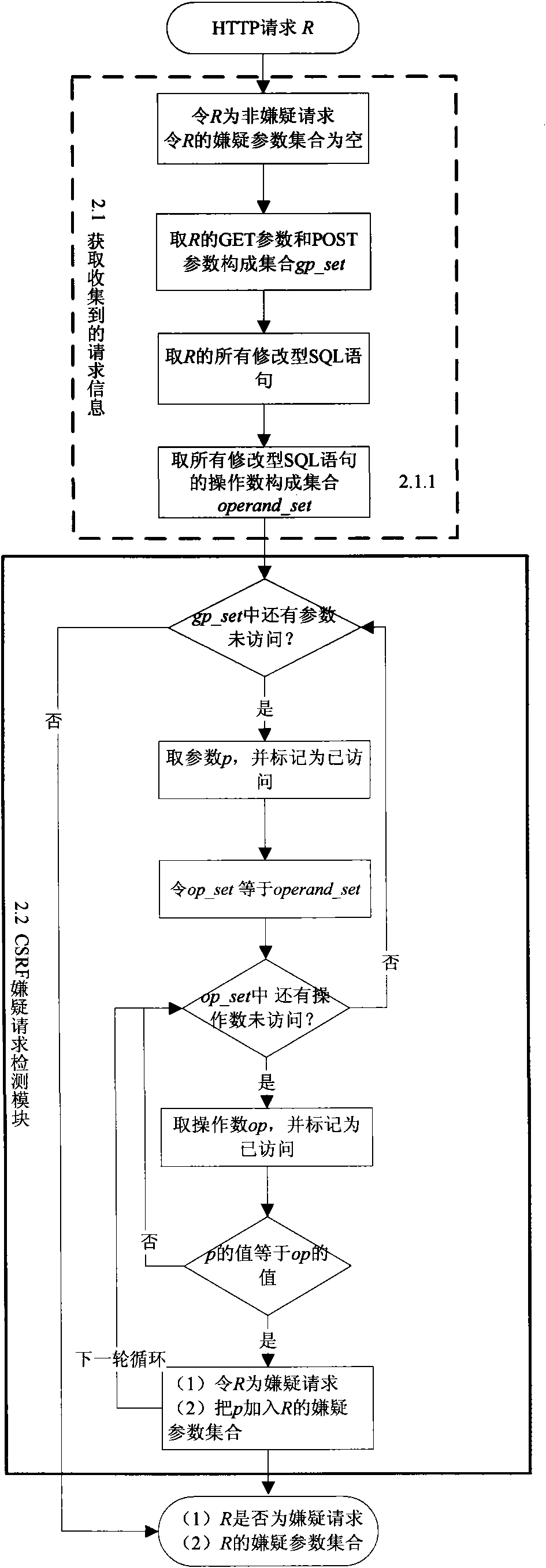
[0039] Such as figure 1As shown, the present invention is composed of five modules of HTTP request information collection module, CSRF suspicious request detection module, test case generation module, test case execution module and CSRF vulnerability detection module according to the "flow" system. The HTTP request information collected first is used for the next analysis; based on the collected information, it is possible to analyze whether a request is a CSRF suspect request, and which parameters in the request may be used in an attack. These parameters are called suspect parameters; The suspect parameter can generate several forged requests for each suspect request, and then generate test cases; when the conditions for generating suspect requests are met (the user browser has obtained the necessary authentication information), execute the test cases; Information, forged requests and execution information of forged requests can analyze whether CSRF vulnerabilities in web app...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com