Entity identification method and system of energy-constrained network
A resource-constrained, entity-based technology, applied in transmission systems, digital transmission systems, security devices, etc., can solve the problems of increasing the burden on network entities and the inability to execute authentication protocols, etc., to achieve computational cost savings, low overhead, and high operational efficiency Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
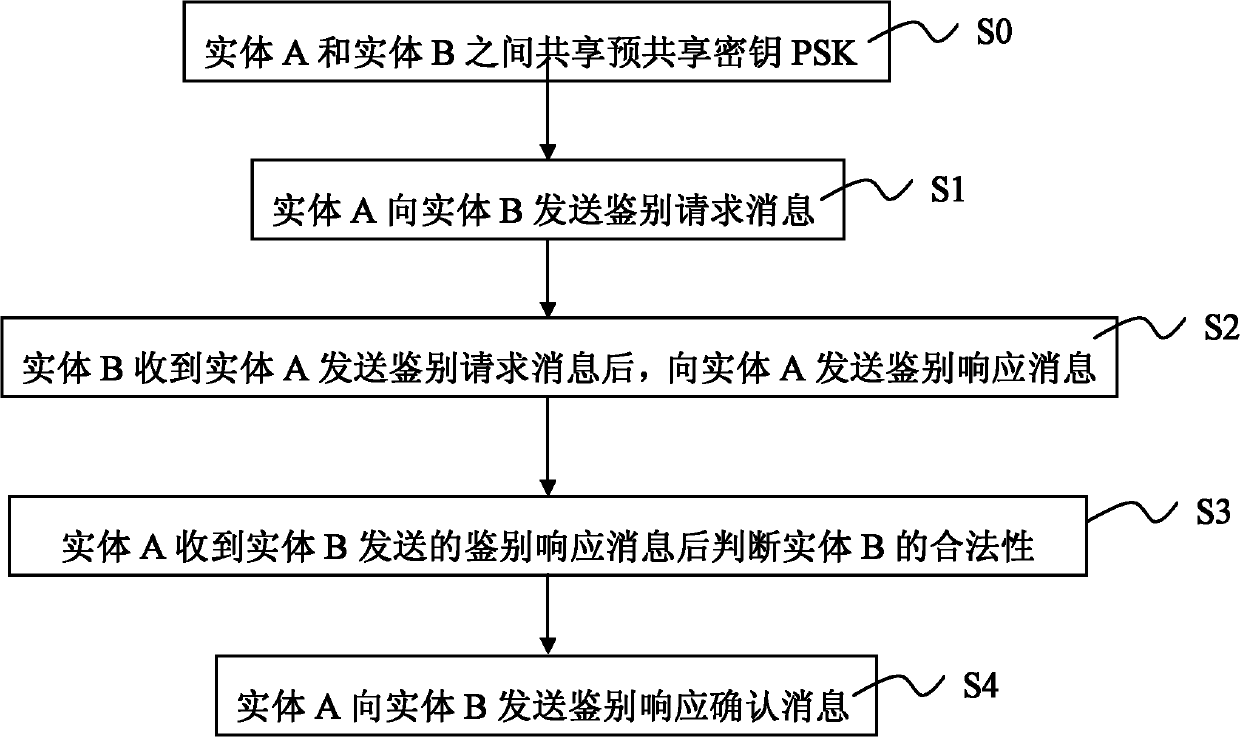
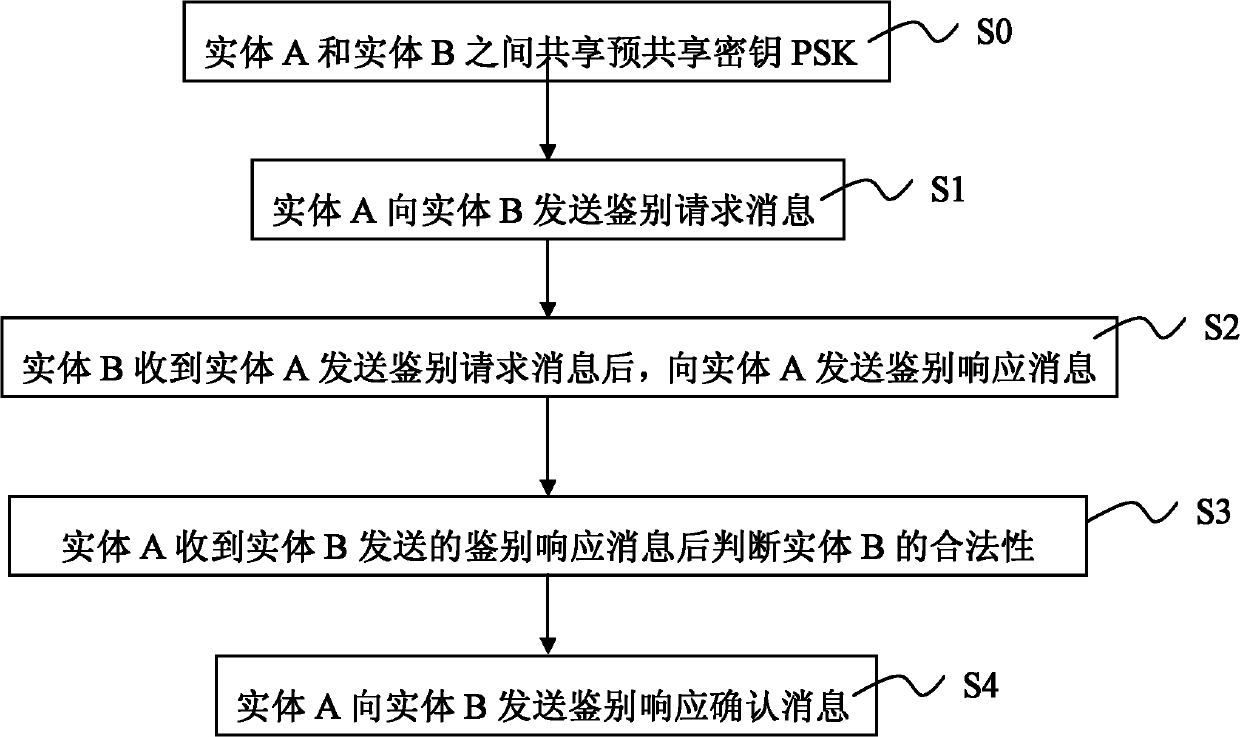
[0033] See figure 1 , the present invention provides a resource-constrained network entity identification method, the method comprising the following steps:
[0034] Step S0: A pre-shared key (Pre-Shared key, PSK) has been shared between entity A and entity B;
[0035] Step S1: Please refer to image 3 , entity A sends an authentication request message 10 to entity B. The authentication request message 10 includes SN1. SN1 is obtained by the following method: Entity A generates a random number N1, calculates Among them, the symbol Indicates a bit-by-bit XOR operation, the same below.
[0036] Step S2: Please refer to Figure 4 , after entity B receives the authentication request message 10 sent by entity A, it first calculates Invert N1 bit by bit to get RN1, and calculate Then, entity B generates a random number N2 and calculates Entity B constructs an authentication response message 20 and sends it to entity A. The authentication response message 20 includes SR...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com