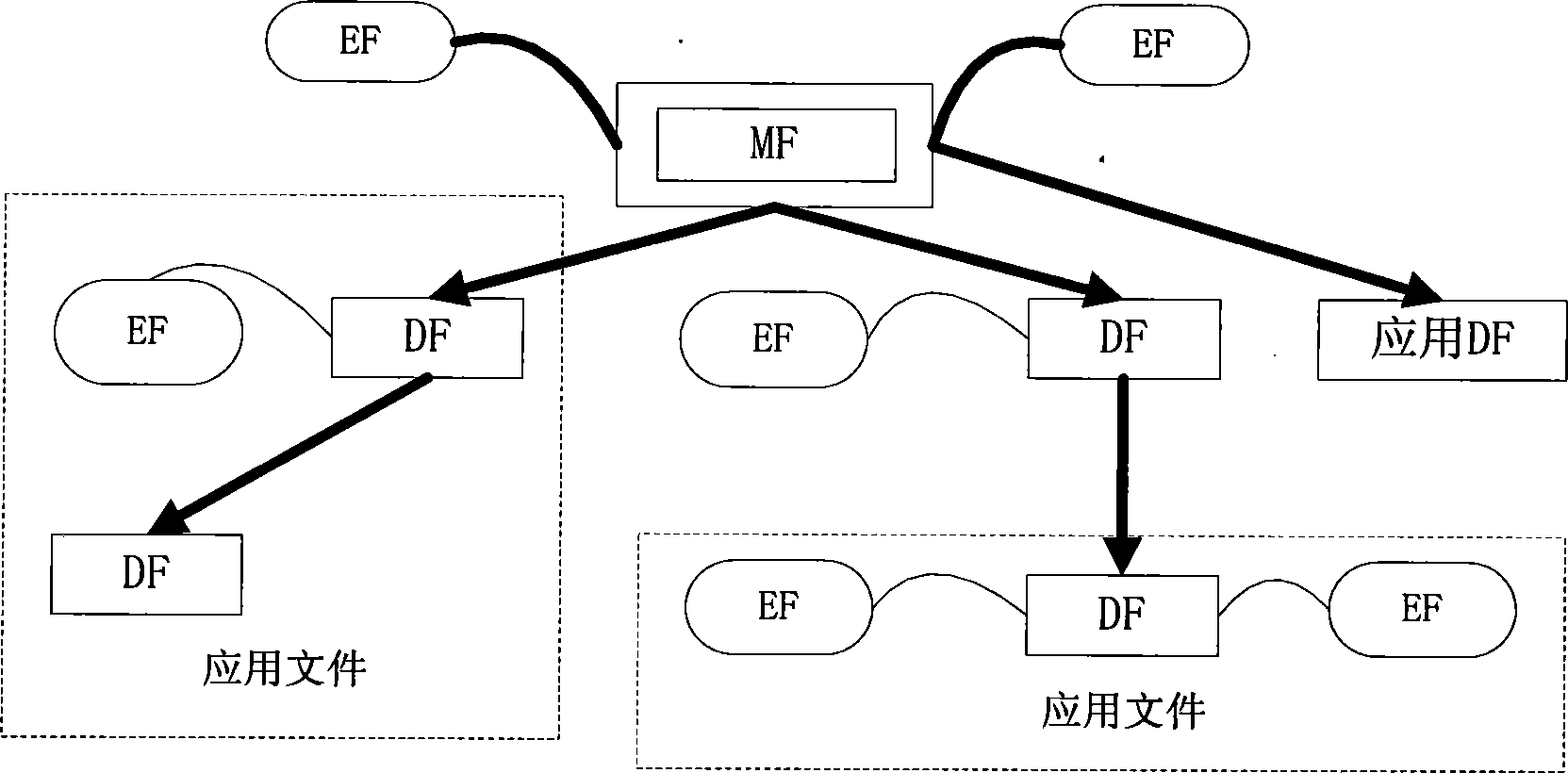
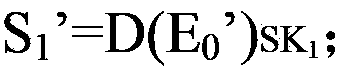Smart card external authentication method
An external authentication and smart card technology, applied in user identity/authority verification, electrical components, transmission systems, etc., can solve problems such as denial of service attacks, failure of signature verification, and information cannot be restored
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0066] In order to make the technical means, creative features, goals and effects achieved by the present invention easy to understand, the present invention will be further described below in conjunction with specific illustrations.
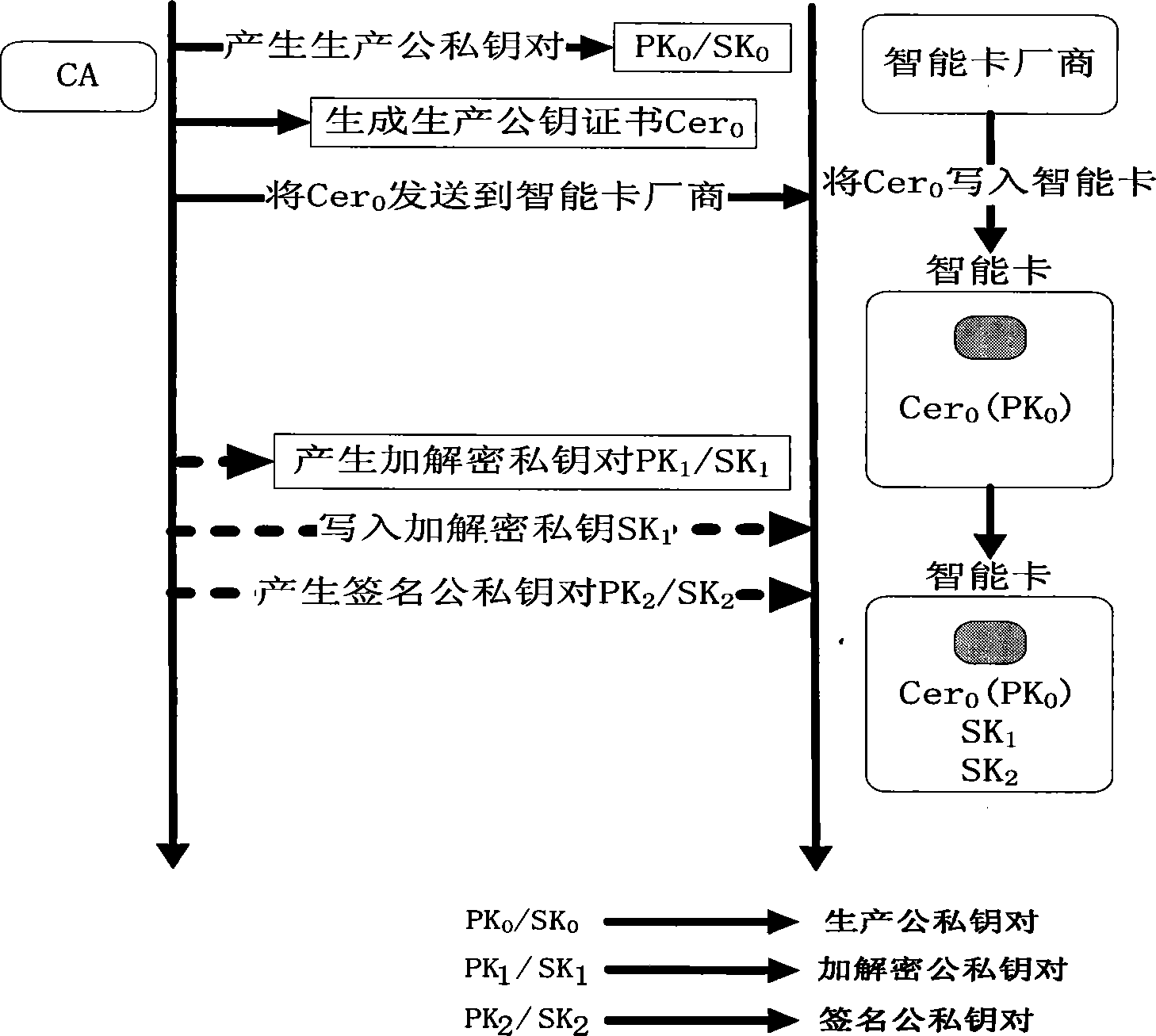
[0067] Such as figure 2 Shown, the smart card external authentication method of the present invention, it comprises the steps:
[0068] (1) Production public-private key pair PK generated by CA 0 / SK 0 , and will produce the public key PK 0 Written into the smart card at the factory;
[0069] (2) By producing the private key SK 0 Encryption and decryption public-private key pair PK 1 / SK 1 Encrypted and written into the smart card;
[0070] (3) By encrypting and decrypting the private key SK 1 Signature public-private key pair PK 2 / SK 2 Encrypted writing to the smart card;
[0071] (4) Produce private key SK 0 Managed by CA, the operation of the smart card private key must be produced by the CA using the private key SK 0 sign.
...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com