Method and equipment for preventing source address spoofing attack
A technology of spoofing attacks and source addresses, applied in the field of communication, can solve problems such as wrongly discarded packets, network failure, etc., and achieve the effect of avoiding wrongly discarded
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
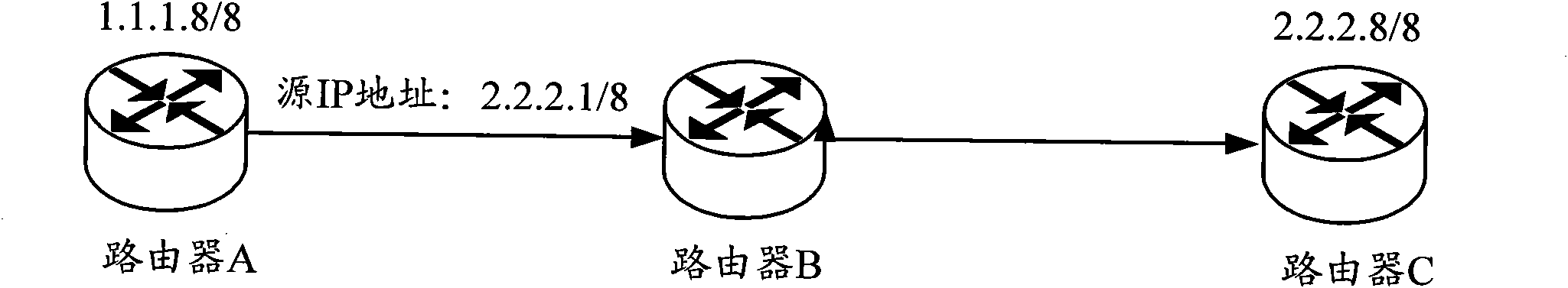
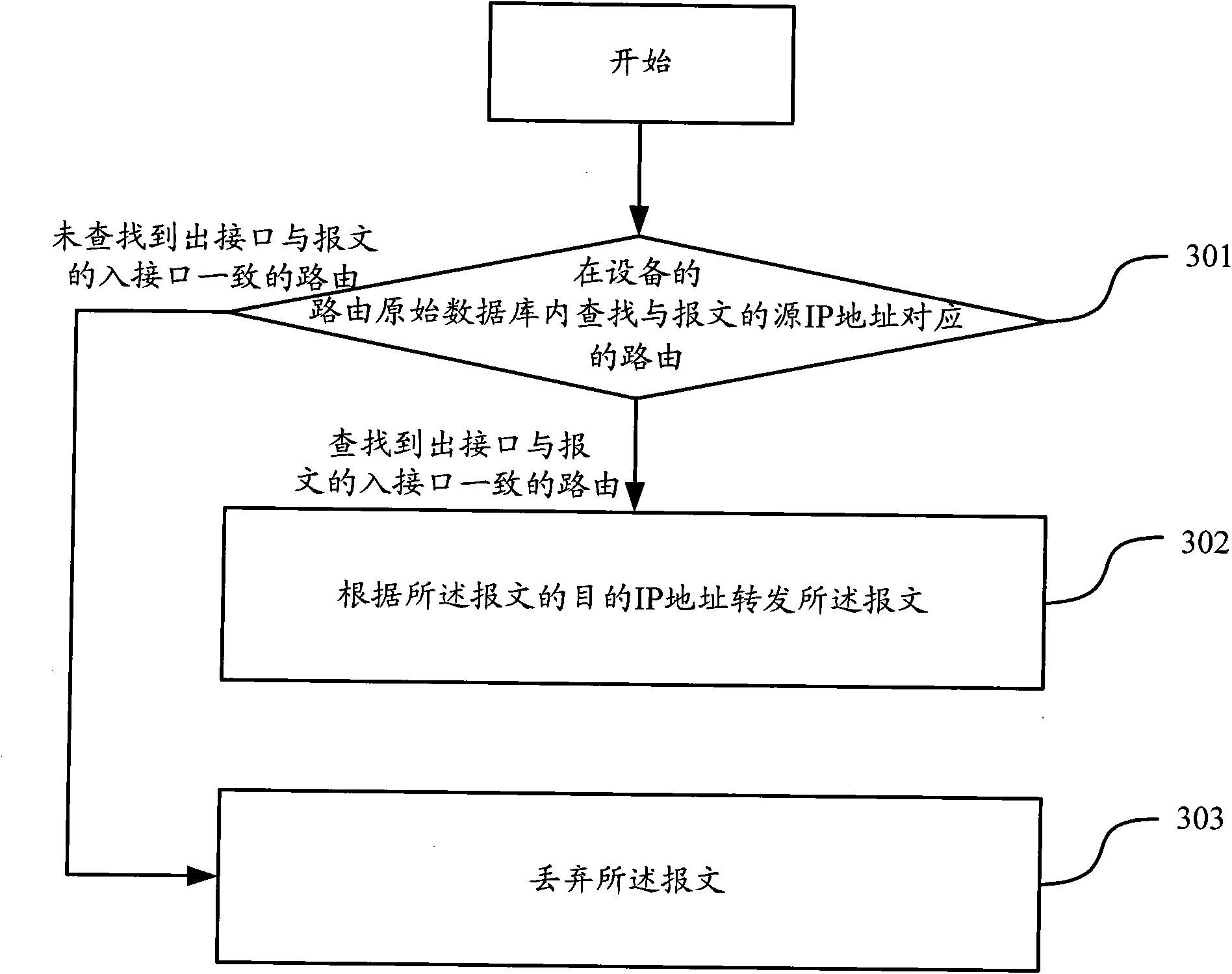
[0045] Embodiment 1 of the present invention provides a method for preventing source address spoofing attacks. The device uses URPF technology to prevent source address spoofing attacks. The device performs URPF check on the received message, and forwards the message when the check result is legal. When the check result is illegal, such as image 3 As shown, the method includes the following steps:
[0046] Step 301, search for the route corresponding to the source IP address of the message in the original routing database of the device; if the outgoing interface of any route in the found route is consistent with the incoming interface of the message, perform step 302; if not found If the outbound interface of the corresponding route or all the found routes is inconsistent with the inbound interface of the packet, step 303 is executed.
[0047] When the device is learning routes, it can learn multiple routes to the same IP address. At this time, the device will select an opti...
Embodiment 2
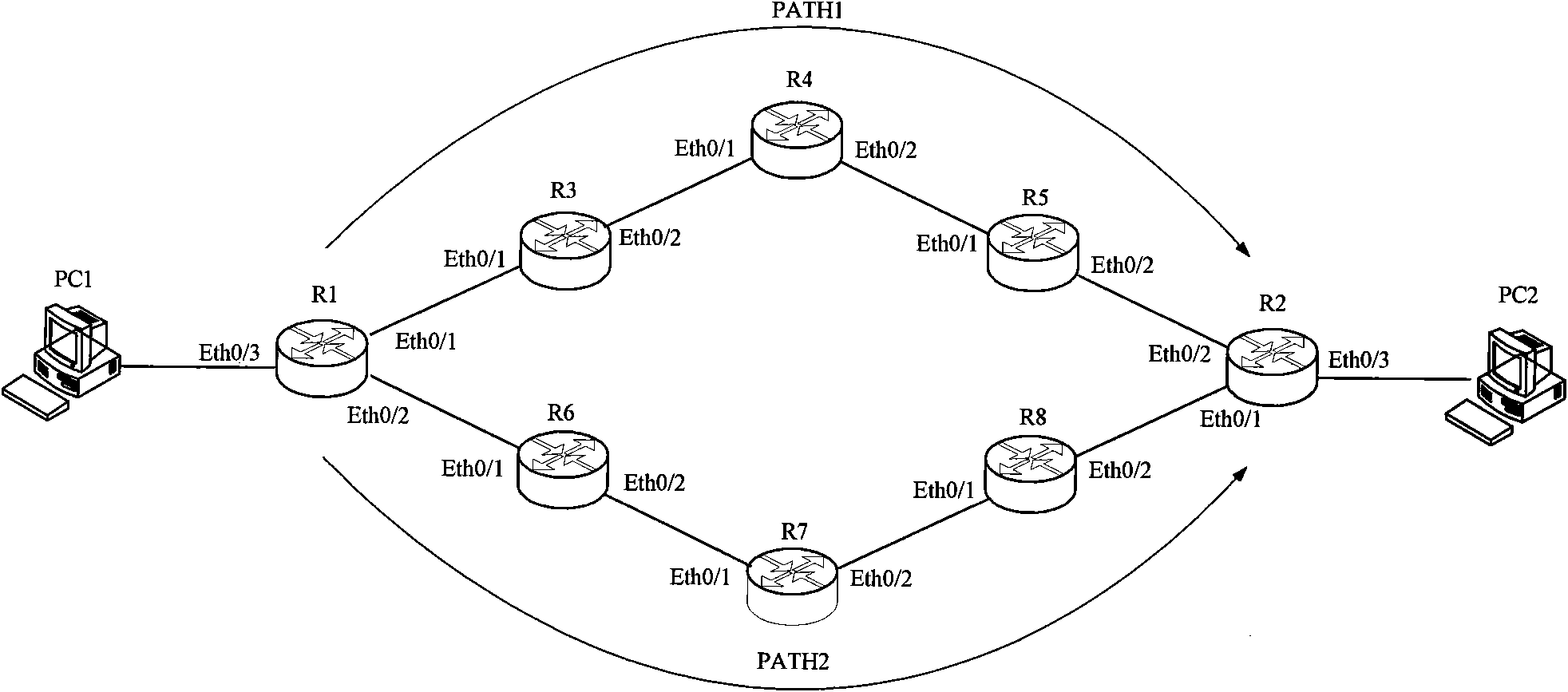
[0055] Embodiment 2 of the present invention provides a method for preventing source address spoofing attacks. On the basis of Embodiment 1, in order to prevent the device from repeatedly searching the original route database for packets of the same data flow, when the route found by the device in the original route database If the outbound interface of any route is the same as the inbound interface of the packet, the device also stores the correspondence between the found IP address and the interface.
[0056] Below to figure 2 Take R7 as an example to illustrate the method provided in this embodiment. Assume that R7 can learn the IP address A of PC2 from R8 and R6 respectively during route learning. R7 judges that the priority of the route from R6 is high, and stores address A in the forwarding table. The corresponding relationship with Eth0 / 1, but the route to PC2 learned from R8 is stored in the original route database, and the outbound interface of this route is Eth0 / 2, ...
Embodiment 3
[0084] Embodiment 3 of the present invention provides a device for preventing source address spoofing attacks, using unicast reverse path forwarding URPF technology to prevent source address spoofing attacks, such as Figure 5 As shown, the equipment includes:
[0085] A checking unit 10, configured to perform a URPF check on the message received by the device;
[0086] A search unit 11, connected to the check unit 10, is used to search for the source IP address corresponding to the message in the original routing database of the device when the check result of the check unit 10 is that the message is illegal. routing;
[0087] The forwarding unit 12 is connected with the inspection unit 10 and the search unit 11, and is used to forward the message when the inspection result of the inspection unit 10 is that the message is legal; when the search unit 11 finds When the outbound interface of any route in the route is consistent with the inbound interface of the message, forwar...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com