Data comparison method and device
A technology of data comparison and data information, applied in the field of communication, can solve the problem of high memory usage, achieve the effect of reducing execution time and improving processing efficiency
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
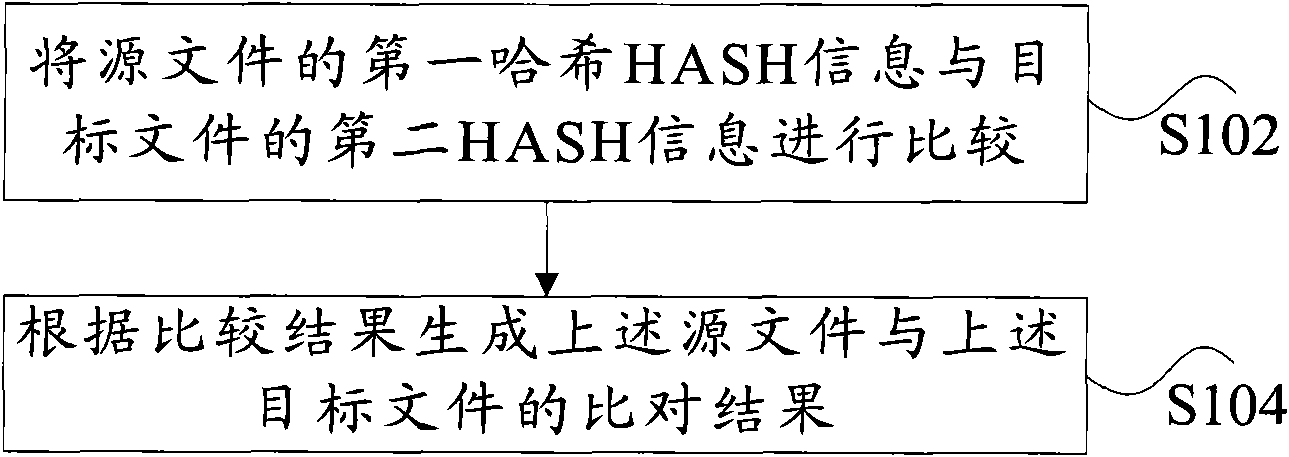
[0031] figure 1 It is a preferred flowchart of the data comparison method according to the embodiment of the present invention, which includes:
[0032] S102, comparing the first HASH information of the source file with the second HASH information of the target file;
[0033] S104. Generate a comparison result between the above-mentioned source file and the above-mentioned target file according to the comparison result.
[0034] This embodiment solves the problem of high memory usage caused by the data comparison method in the prior art by comparing the HASH information of the source file and the target file instead of the data itself, thereby reducing execution time and improving processing efficiency Effect.
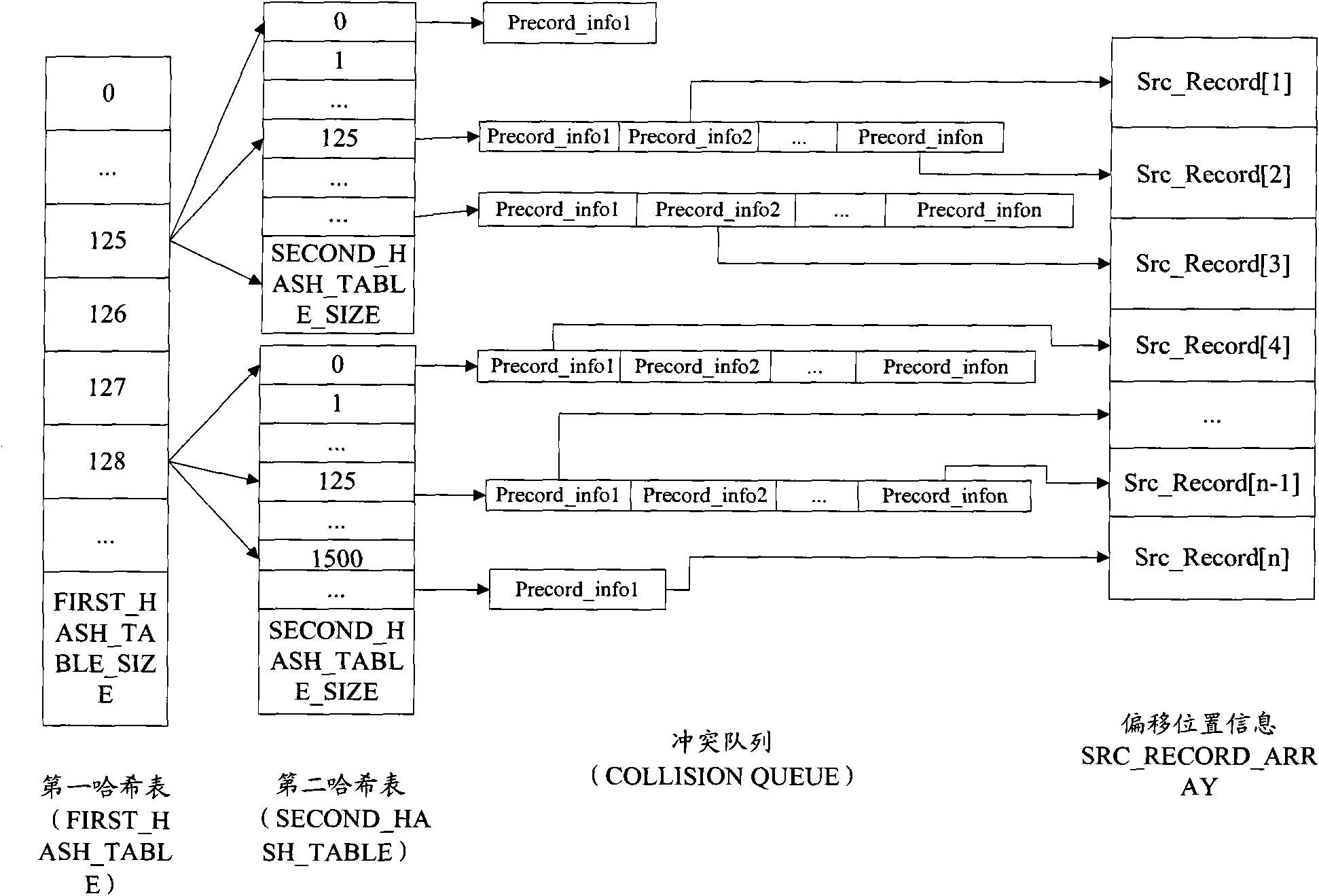
[0035] Preferably, comparing the first hash HASH information of the source file with the second HASH information of the target file includes: establishing a memory index table corresponding to the source file in the memory, wherein the memory index table includes the...
Embodiment 2
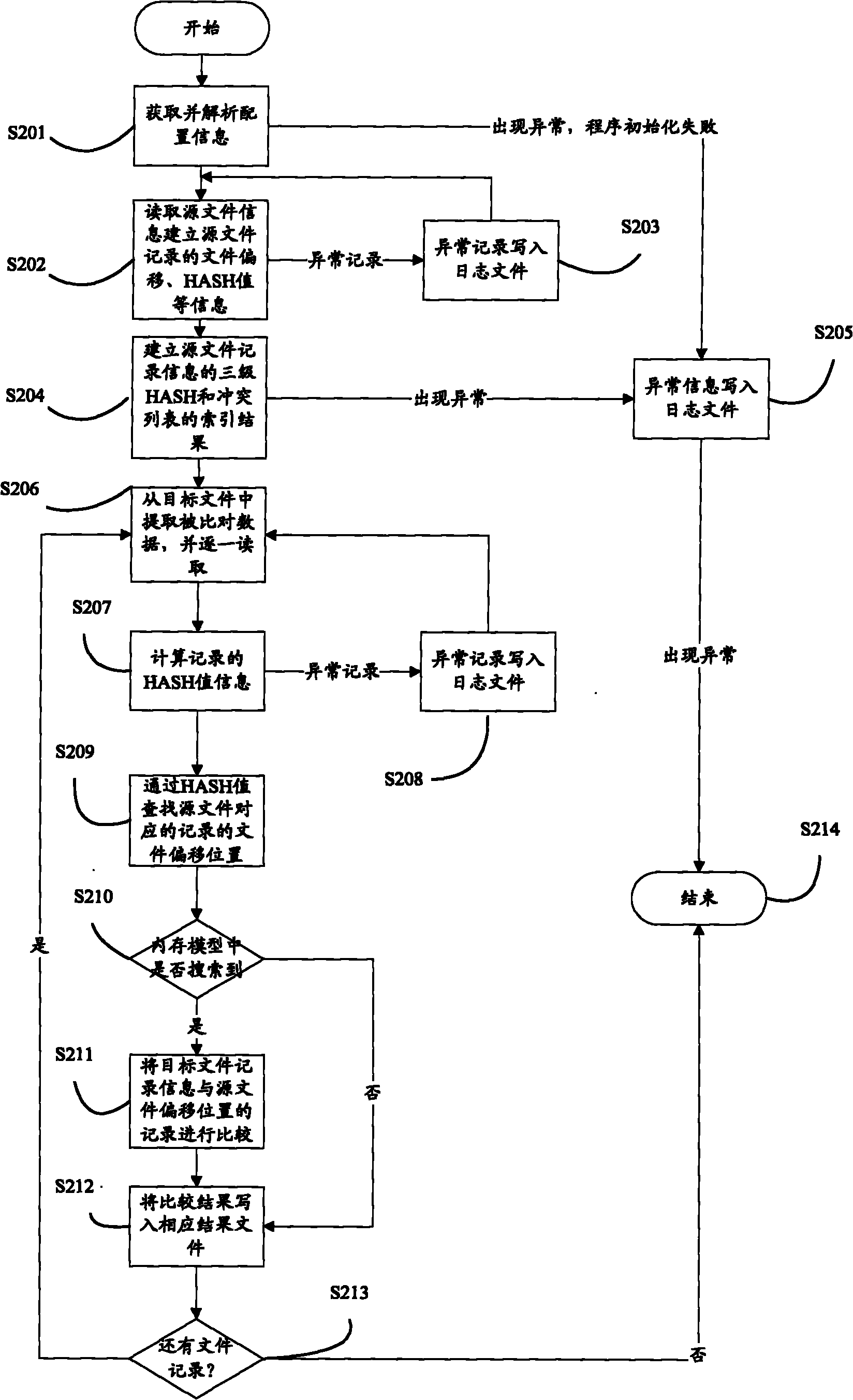
[0042] figure 2 It is another preferred flow chart of the data comparison method according to the embodiment of the present invention, which includes:
[0043] Step S201: Obtain the system configuration parameters provided by the user and perform corresponding analysis. If an exception occurs, go to step S203, otherwise go to step S202.
[0044] Step S202: read the source file into memory, and store the HASH value information and file offset information of the source file data. If there is abnormal data, go to step S203; otherwise, go to step S204.
[0045] Step S203: Write abnormal data into the log, and then jump to step S201.
[0046] Step S204: Establish an in-memory index model for source file information, mainly including three-layer HASH indexes and corresponding conflict lists. If abnormality occurs, go to step S205, otherwise go to step S206.
[0047] Step S205: Write the failure of the memory model into the log, and jump to step S214.
[0048] Step S206: extra...
Embodiment 3
[0060] The present embodiment provides source file a.txt and object file b.txt, and wherein a.txt contains following two records:
[0061] 2013|950112345|13012345678
[0062] 2013|950112345|13098765432
[0063] b.txt contains the following two records:
[0064] 2013|950112345|13012345678
[0065] 2014|950112345|13098765432
[0066] The user specifies to compare by all fields respectively.
[0067] According to the above steps S201 to S214, firstly, a.txt is loaded into the memory, and a corresponding memory model is established. Then read the b.txt file, calculate the HASH value, search in the memory model, and then read the corresponding records in the a.txt file for comparison. Generate result files.
[0068] Unique record of a.txt: 2013|950112345|13098765432
[0069] Unique record of b.txt: 2014|950112345|13098765432
[0070] Records shared by a.txt and b.txt files: 2013|950112345|13012345678
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com