Method and system for detecting web page horse hanging
A webpage hanging horse and detection method technology, applied in the transmission system, special data processing applications, instruments, etc., can solve the problems of dangerous data detection, low efficiency, low accuracy, etc., and achieve the effect of accurate detection
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0026] The present invention will be further described below in conjunction with the accompanying drawings and specific embodiments.
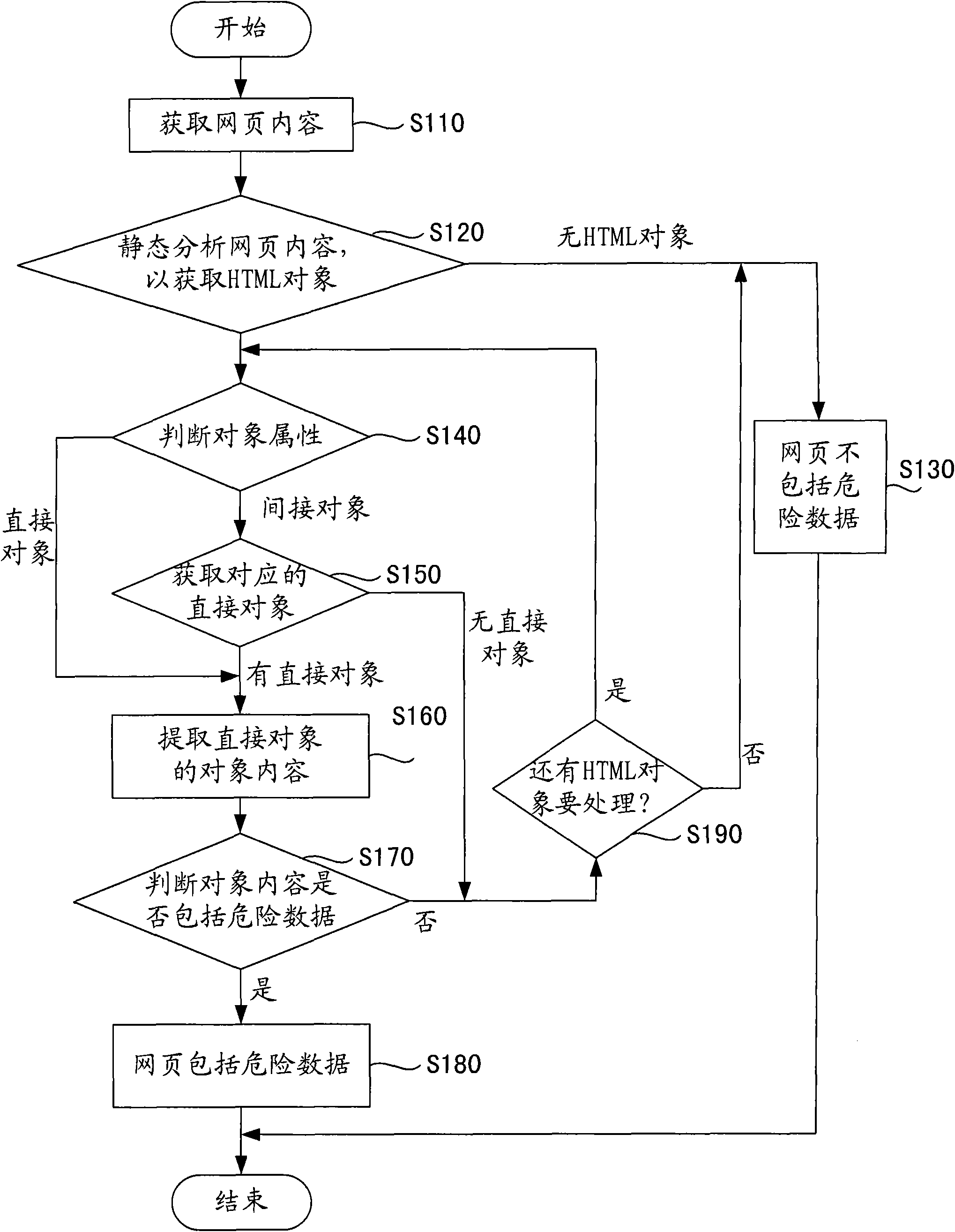
[0027] figure 1 A method for detecting a webpage trolling horse according to an embodiment of the present invention is shown, which is used for detecting whether dangerous data is contained in a webpage.
[0028] At step S110, web page content is acquired. The webpage content can be obtained in various known ways, for example, by constructing a client following HTTP or HTTPS to obtain the webpage content.
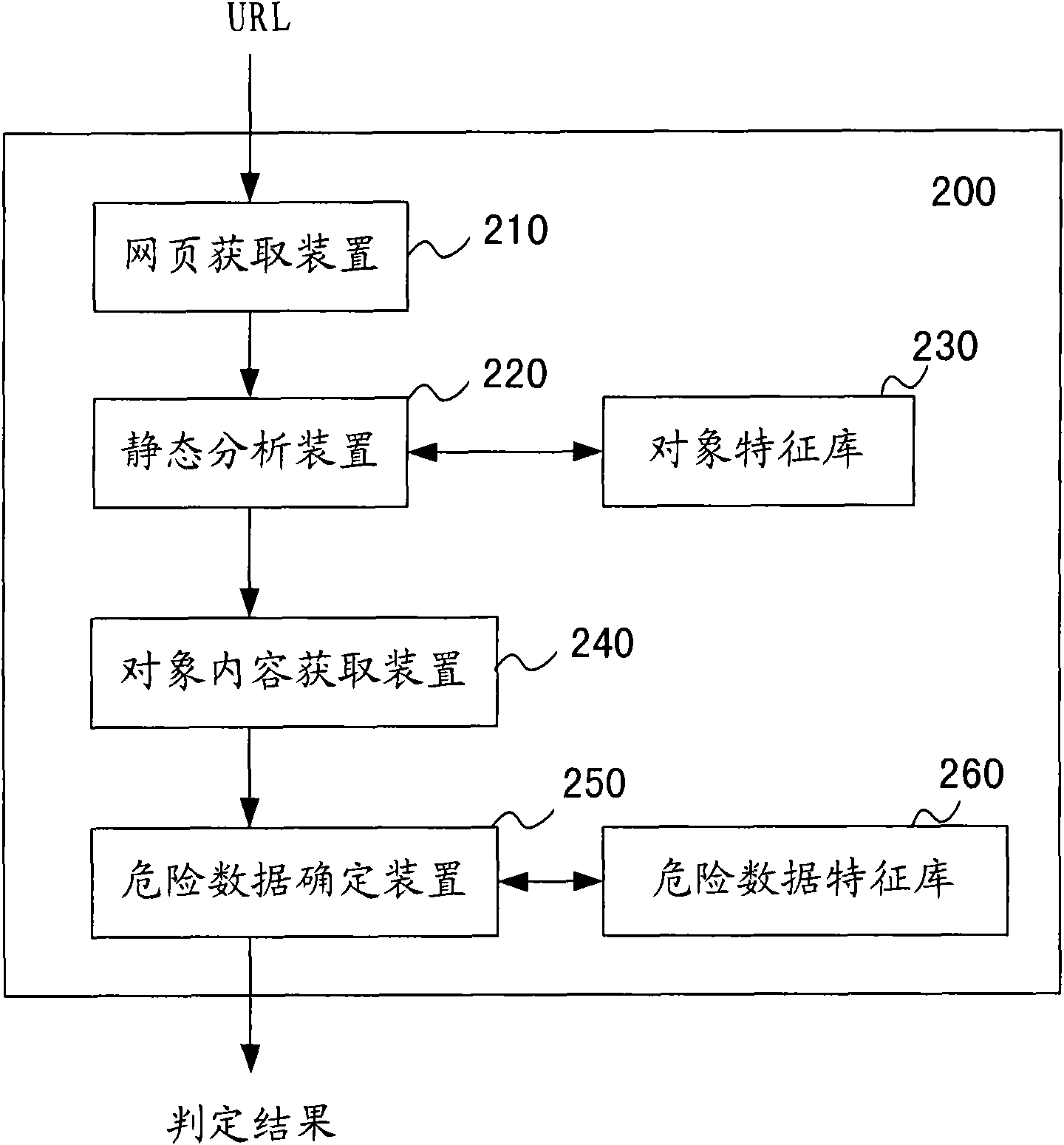
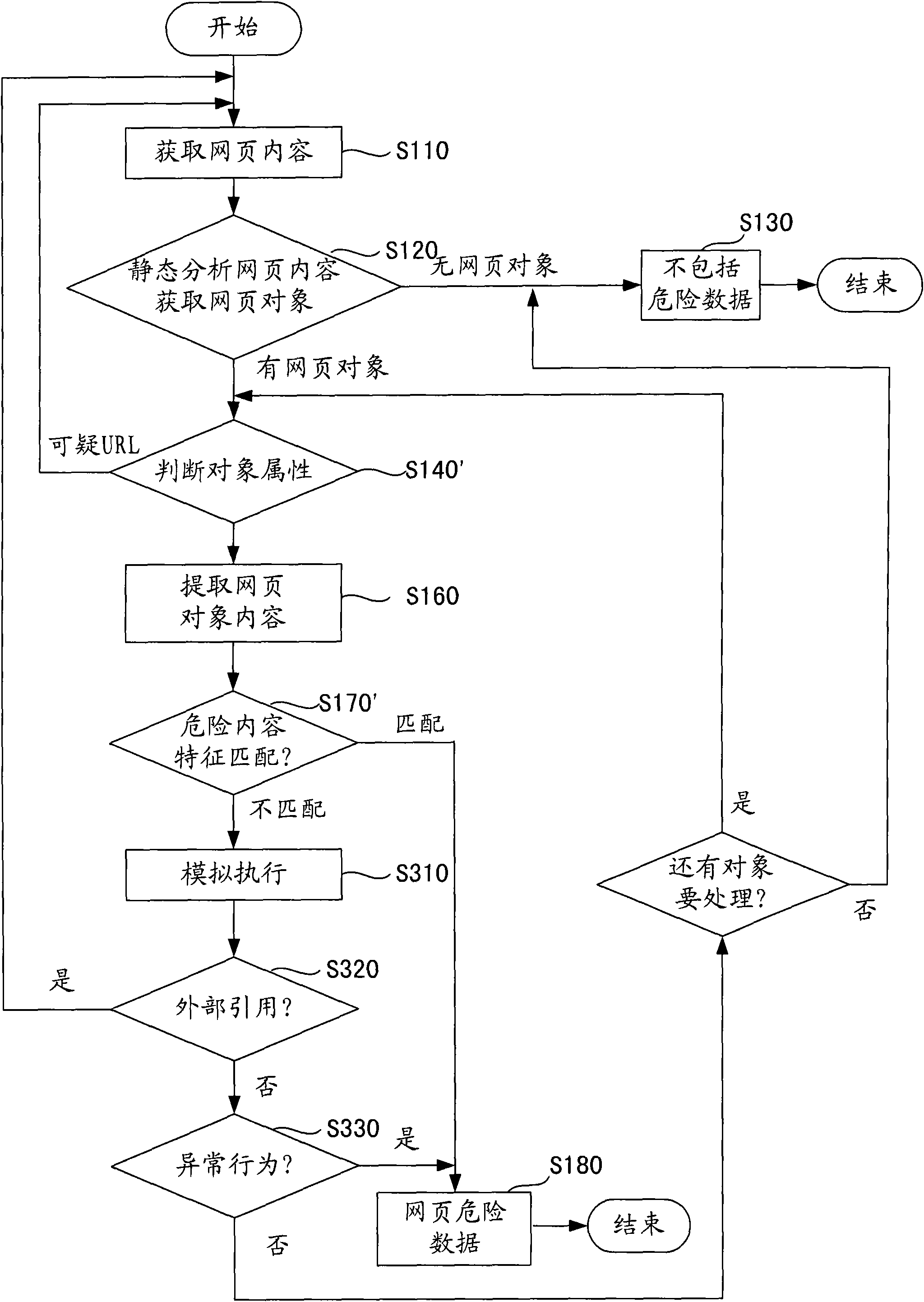
[0029] Then at step S120, static analysis is performed on the acquired webpage content, so as to detect HTML objects that may contain dangerous data. The content of the web page includes multiple HTML objects, such as table, title, or img, and so on. The applicant of the present invention found that dangerous data usually appears in specific HTML objects, such as iframes, frames, URL addresses referencing javascript scripts, ActiveX contr...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com