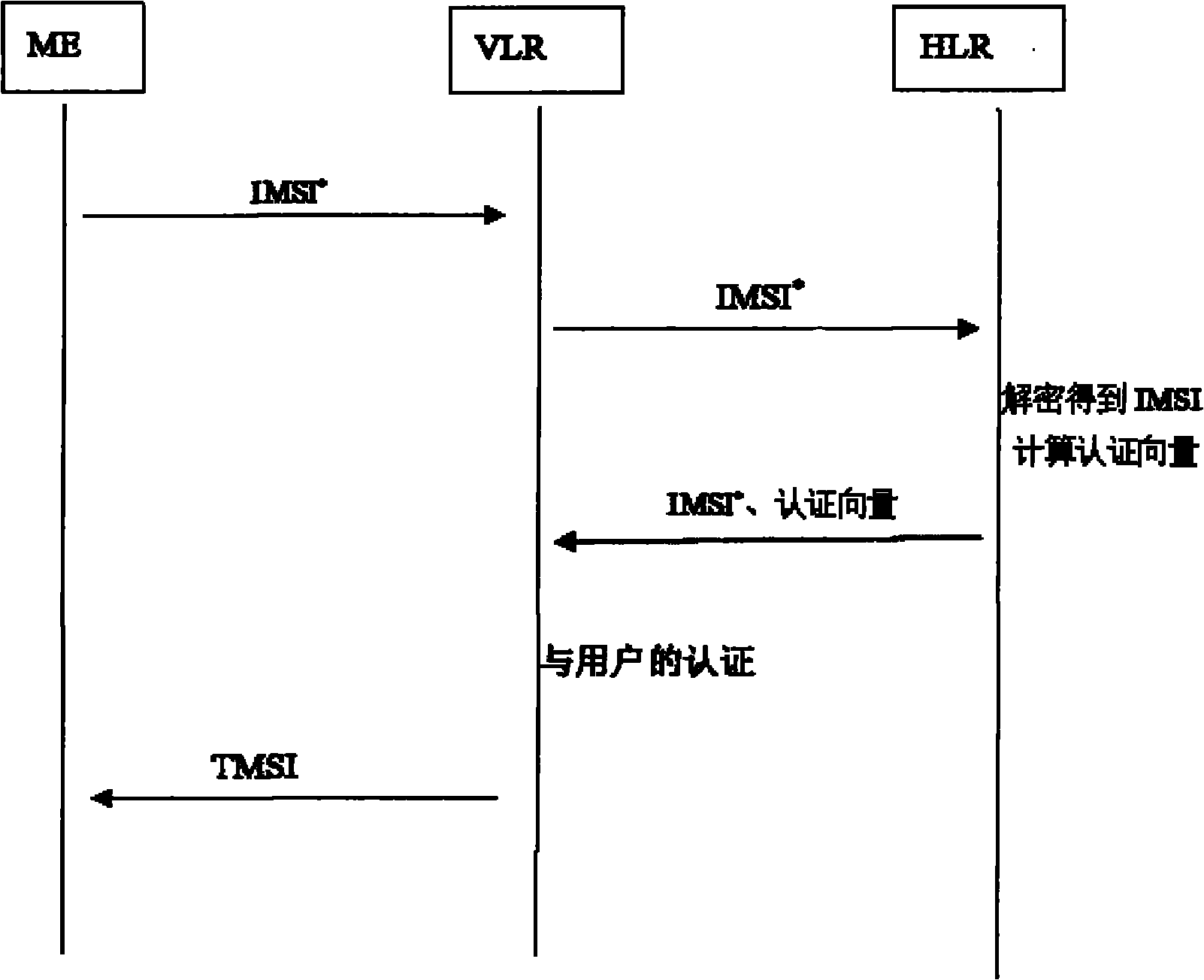
Method for protecting international mobile subscriber identity (IMSI) in mobile communication
A mobile communication and trusted technology, applied in wireless communication, electrical components, security devices, etc., can solve problems such as loss of TMSI on the network side
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
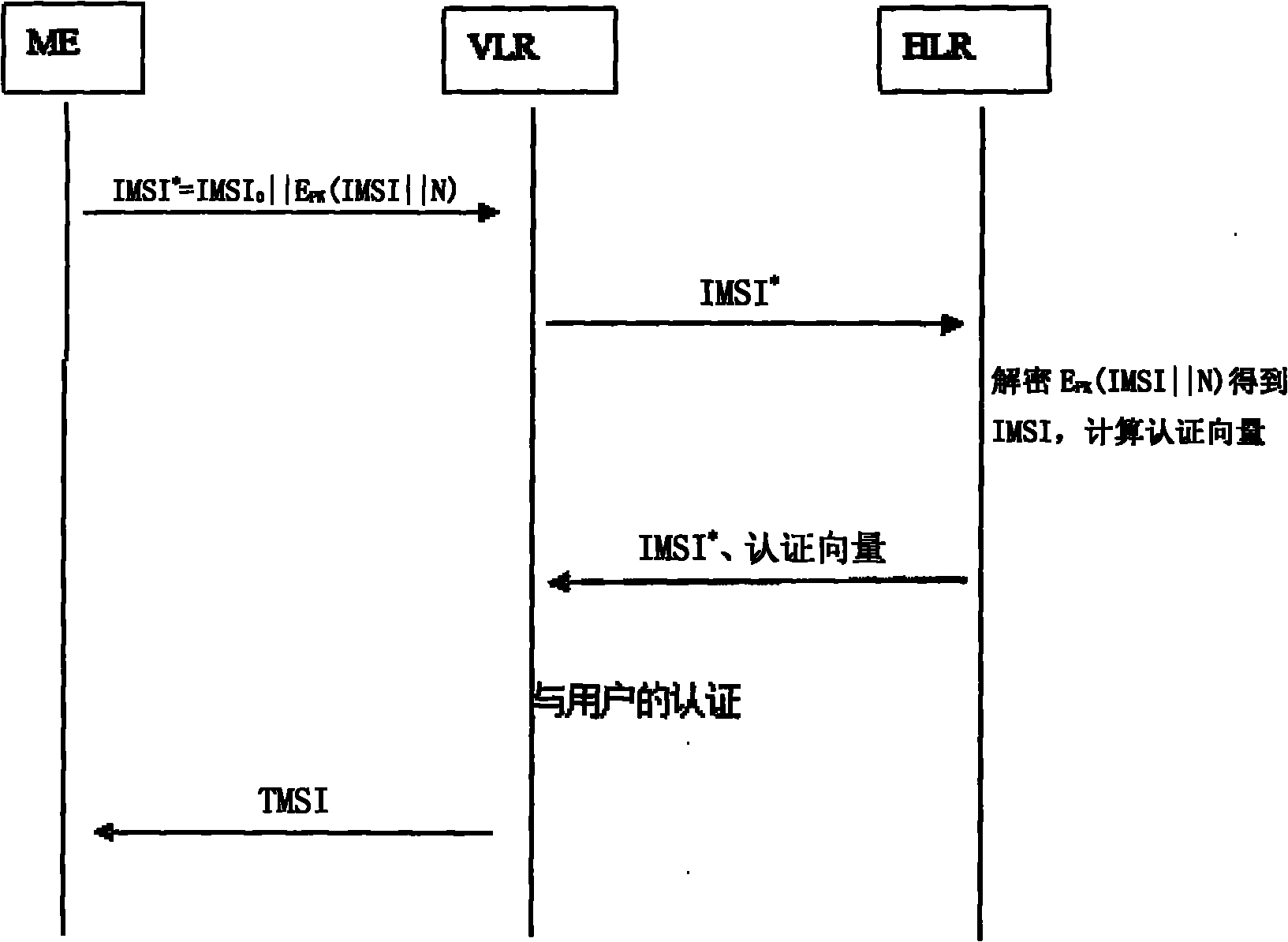
[0068] Embodiment 1: Scheme 1 for IMSI encryption processing
[0069] Such as figure 2 As shown, the user calculates the IMSI * = IMSI 0 ||EPK (IMSI||N), the user stores the IMSI * and sent to the VLR, where the IMSI 0 Including the part that identifies HLR in IMSI, N is a random number generated by the user, E PK Is the public key encryption algorithm; VLR according to IMSI 0 Get HLR information and put IMSI * Send to relevant HLR; HLR uses private key to IMSI * IMSI 0 The latter part is decrypted to obtain the IMSI; after the user is determined, the HLR uses the corresponding key K shared with the user to generate multiple quintuples of the AKA authentication protocol, and combines these quintuples with the IMSI * Sent to VLR; VLR stores quintuple, and according to IMSI * Perform the AKA protocol with any group of five-tuples to authenticate the user.
Embodiment 2
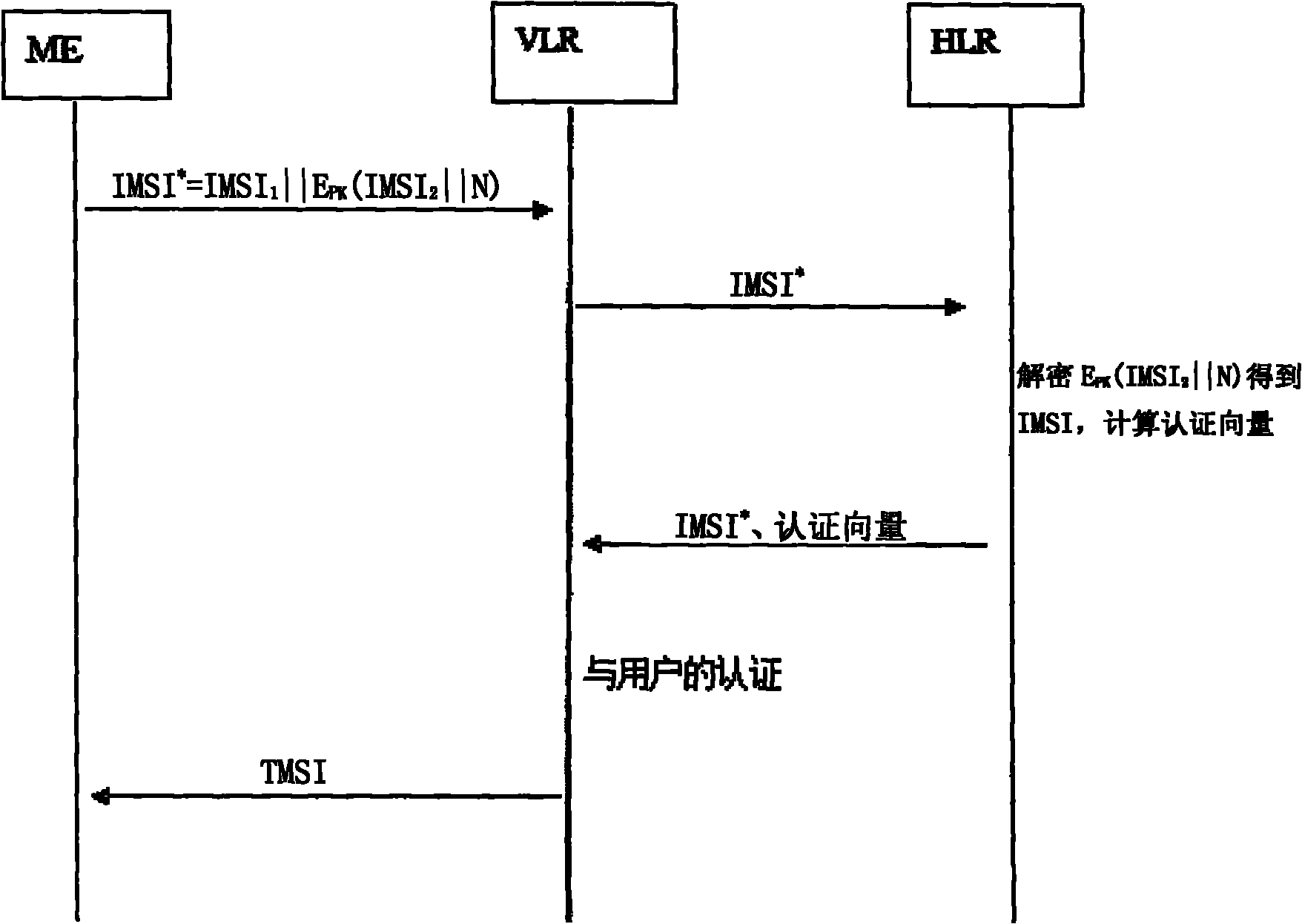
[0070] Embodiment 2: Scheme 2 for IMSI encryption processing
[0071] Such as image 3 As shown, the user calculates the IMSI * = IMSI 1 ||E PK (IMSI 2 ||N), the user stores the IMSI * and sent to the VLR, where the IMSI 1 Including MCC, MNC in IMSI and the part identifying HLR in MSIN, IMSI 2 is the part that identifies the user identity, N is the random number generated by the user, E PK Is the public key encryption algorithm; VLR according to IMSI 1 Get HLR information, put IMSI * Send to relevant HLR, HLR uses private key to decrypt, get IMSI 2 , so as to obtain the complete IMSI; after determining the user, the HLR uses the corresponding key K shared with the user to generate multiple quintuples of the AKA authentication protocol, and combines these quintuples with the IMSI * Sent to VLR; VLR stores quintuple, and according to IMSI * Perform the AKA protocol with any group of five-tuples to authenticate the user.
[0072] After passing the authentication in Em...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com