Method for preventing address resolution protocol (ARP) attack
A technology of ARP tables and ARP messages, applied in electrical components, transmission systems, etc., can solve the problems that the host cannot get, cannot communicate with the outside world, and messages cannot be processed, etc., to achieve the effect of preventing ARP attacks
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0021] The specific implementation manners of the present invention will be further described in detail below in conjunction with the accompanying drawings and embodiments. The following examples are used to illustrate the present invention, but are not intended to limit the scope of the present invention.
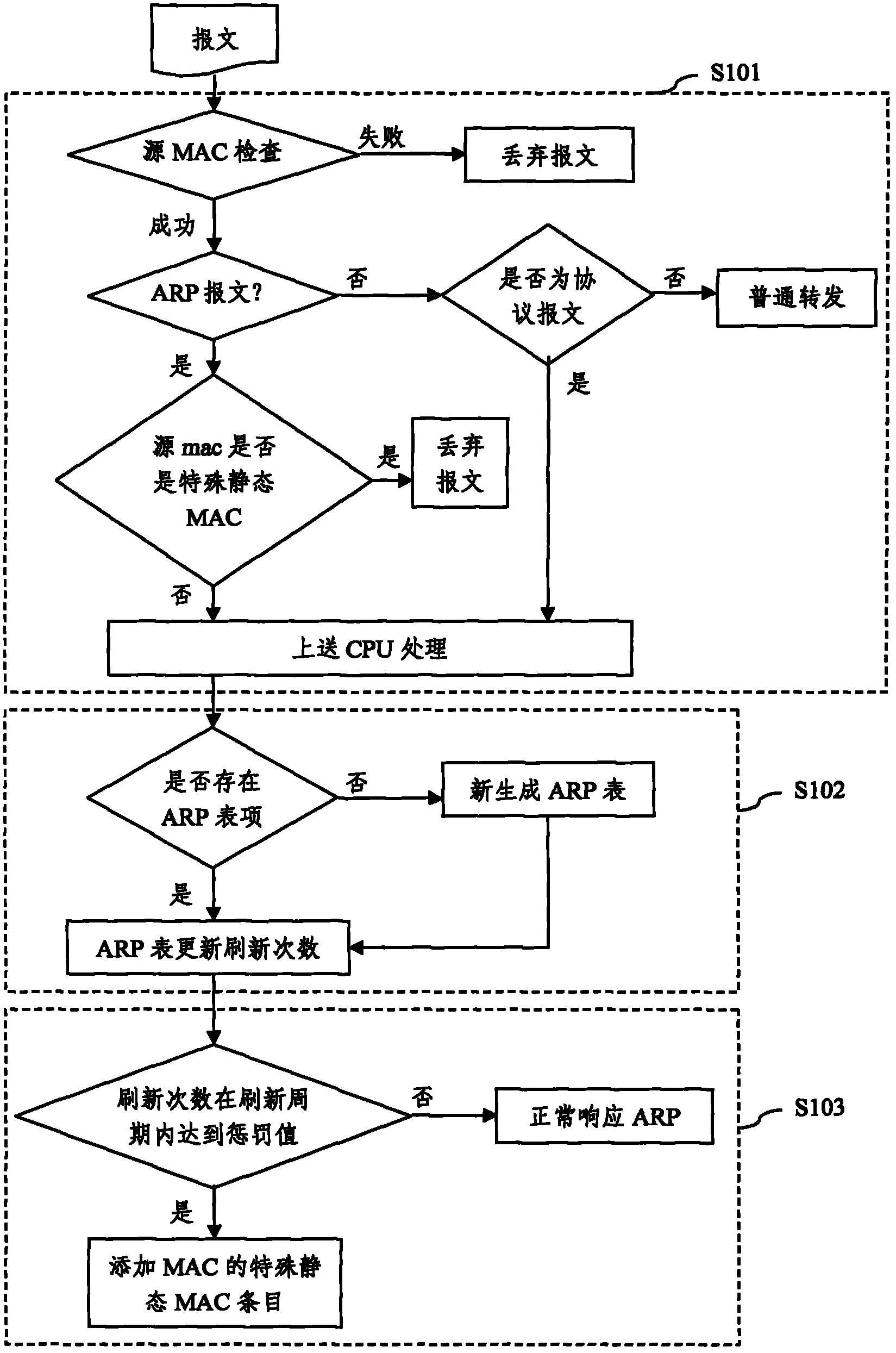
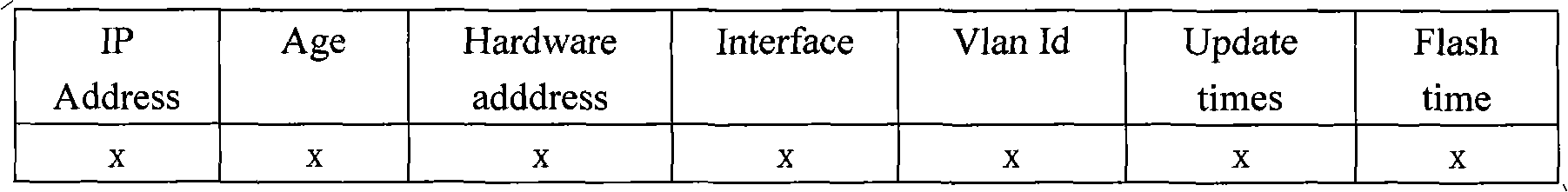
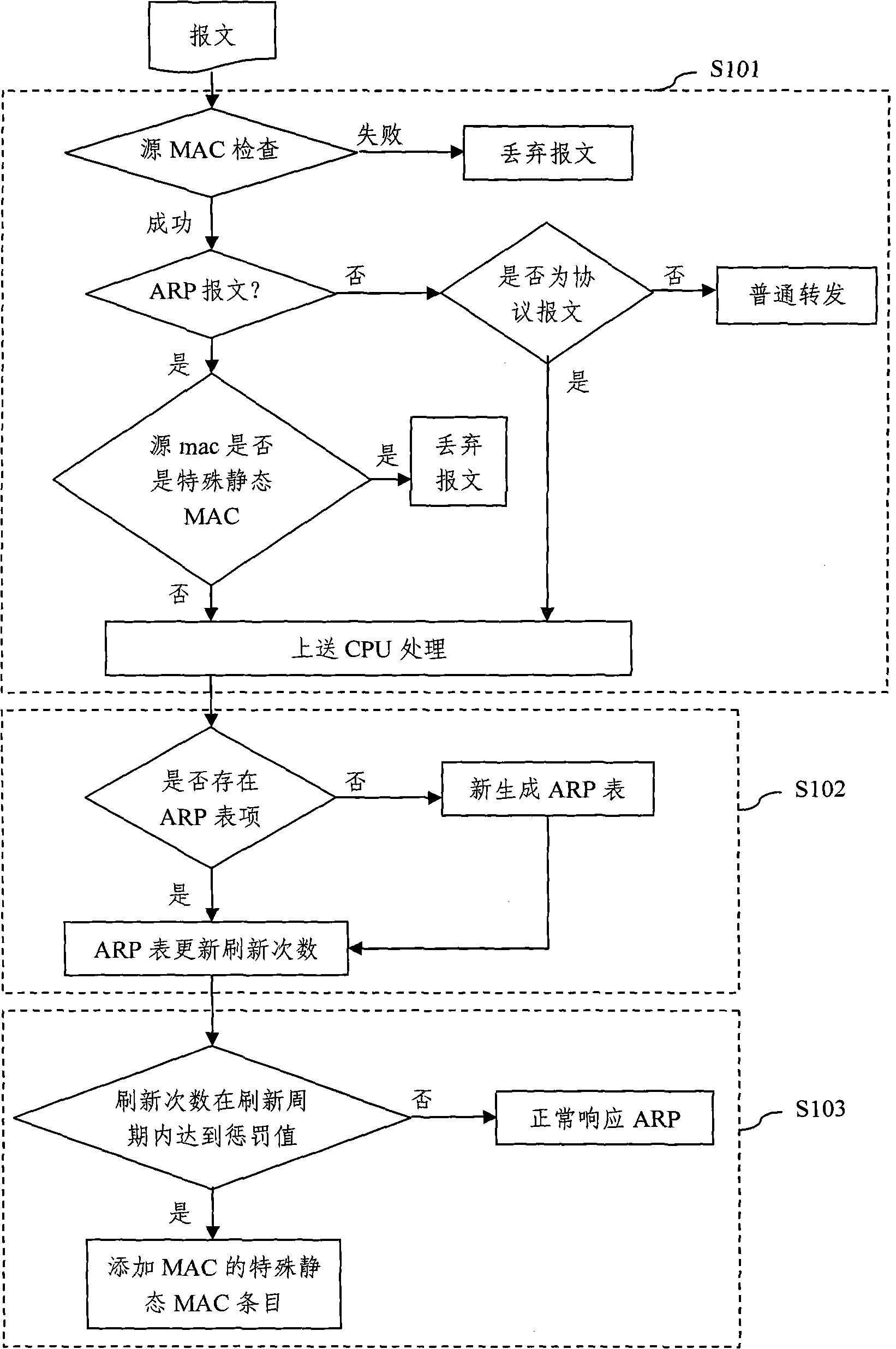
[0022] In the method of this embodiment, the ARP table is expanded, and two parameters are added: the number of refreshes and the refresh cycle, which respectively represent the number of times the ARP table is refreshed and the cycle of being refreshed, and are added to the static MAC in the MAC table. The time-to-live parameter. The specific process is as figure 1 shown, including:
[0023] Step S101, when a network device (such as a switch or a router) receives an ARP message, check whether the source MAC address therein is the static MAC in the MAC table, if it exists, then directly discard the ARP message, If it does not exist, it will be sent to the CPU for proces...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com