Security component of database system
A security component and database technology, which is applied in the security field of database systems, can solve problems such as unreliable storage methods, inability of developers, information exposure to clients, etc., to achieve the effect of preventing threats and improving security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
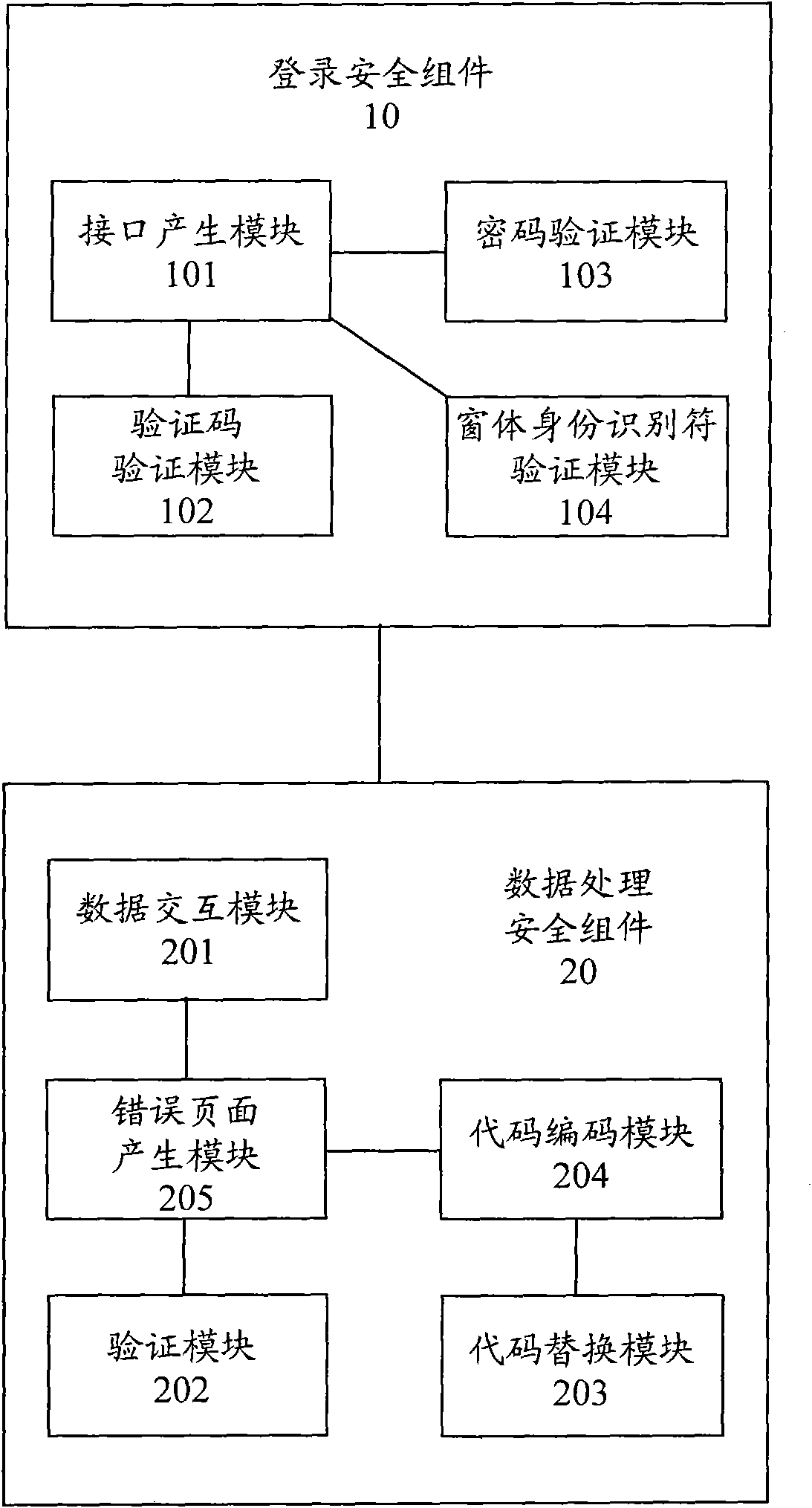
[0032] refer to figure 1 As shown, the security components of the database system of the present invention include a login security component 10 and a data processing security component 20 .
[0033] The login security component 10 includes an interface generation module 101, a verification code verification module 102, a password verification module 103 and a form identity identifier verification module 104, wherein,
[0034] The interface generating module 101 provides a user name input interface, a password input interface, a verification code input interface and a form ID input interface on the login page.
[0035] The verification code verification module 102 obtains the verification code through the verification code input interface, and compares it with the set verification code. If the two are consistent, then proceed to the subsequent steps, and if the two are inconsistent, the login is refused.
[0036] The password data interface 103 obtains the password through th...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com