Document encrypting method and document decrypting method on basis of voice print
An encryption method and encryption key technology, which is applied in the direction of instruments, electrical digital data processing, digital data protection, etc., can solve the problems of limited memory key ability and low key security, and achieve high security and convenient use Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0023] The present invention will be further described below in conjunction with accompanying drawing.
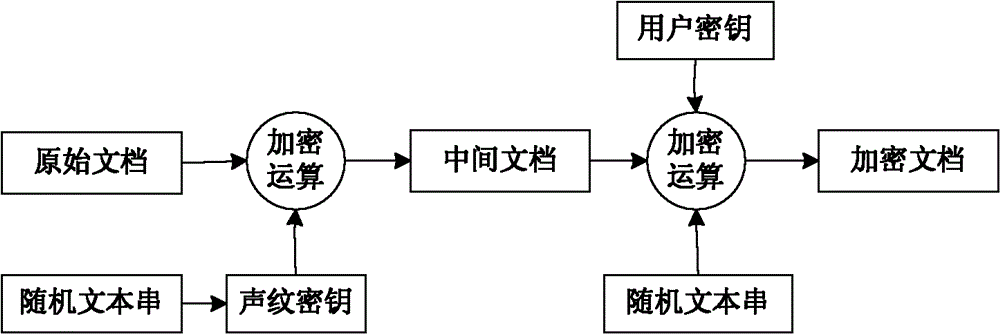
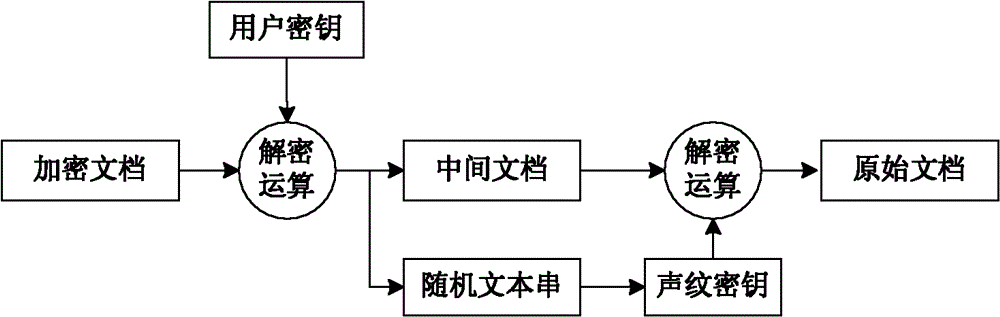
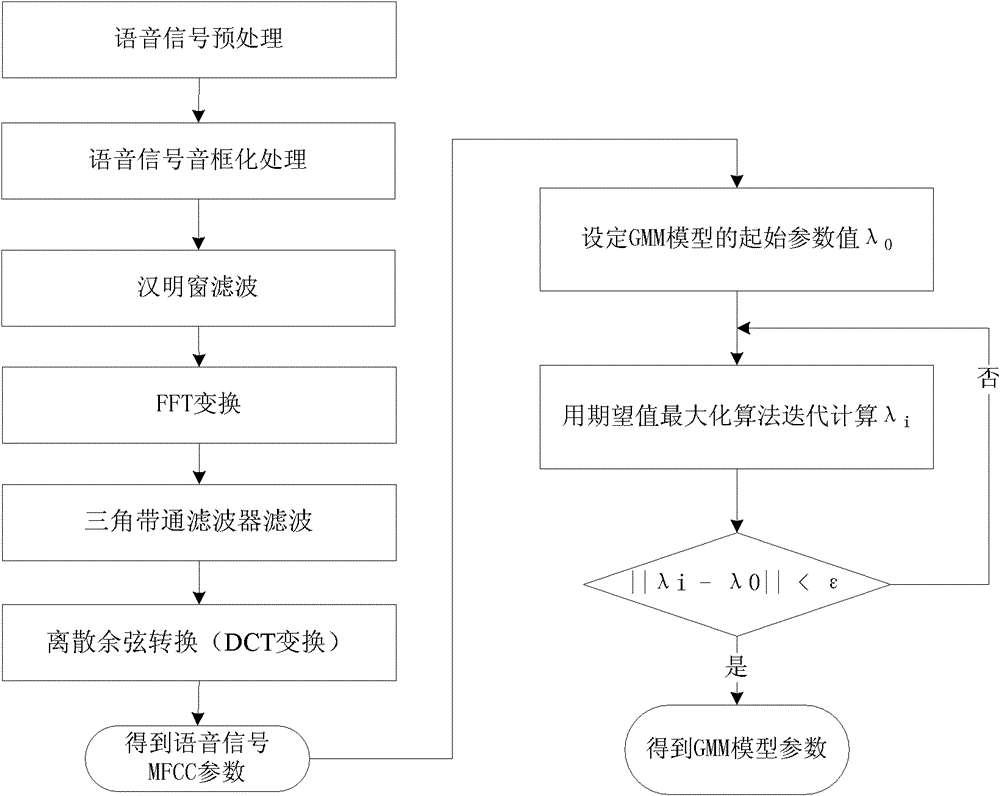
[0024] Speech features MFCC parameters vary with the speaker's pitch, syllable, syllable context, glottal airflow model, and each individual's unique pronunciation. After being trained by the GMM Gaussian mixture model, the parameter values of the speech feature GMM model are stable within a certain numerical range, which is determined by the speaker's voiceprint (the speaker's unique glottal airflow characteristics, pronunciation, etc.) and semantic content. Given the semantic content, the model parameter values are further stabilized around the speaker's voiceprint. Stable key information can be extracted from this model parameter value, that is, the encryption and decryption key determined by the voiceprint characteristics of the voice. The above is the basic principle of the present invention. The process of document encryption in the present invention is as follo...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com