Method and device for controlling subscriber strategy
A user policy, user technology, applied in the field of communication, can solve the problem of no policy server controlling user policy and so on
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
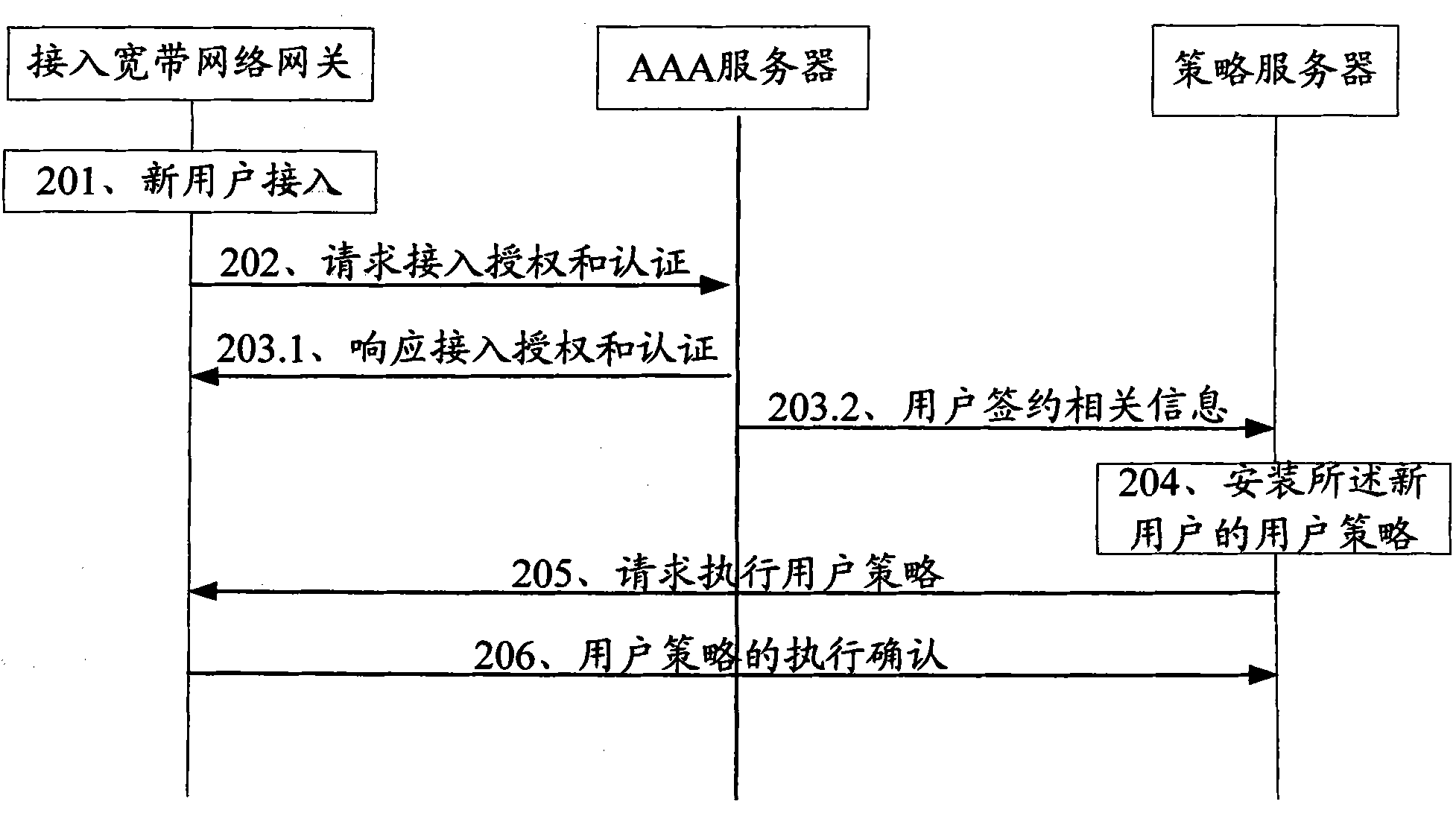
[0083] In this embodiment, when a user initially accesses the network, an AAA (Authentication, Authorization, Accounting, verification, authorization, and accounting) Server interacts with a policy server and triggers the policy server to issue user policies as an example. Process such as figure 2 Shown:
[0084] In step 201, the gateway for accessing the broadband network receives an indication of the user's access to the network, such as a DHCP Discovery message.
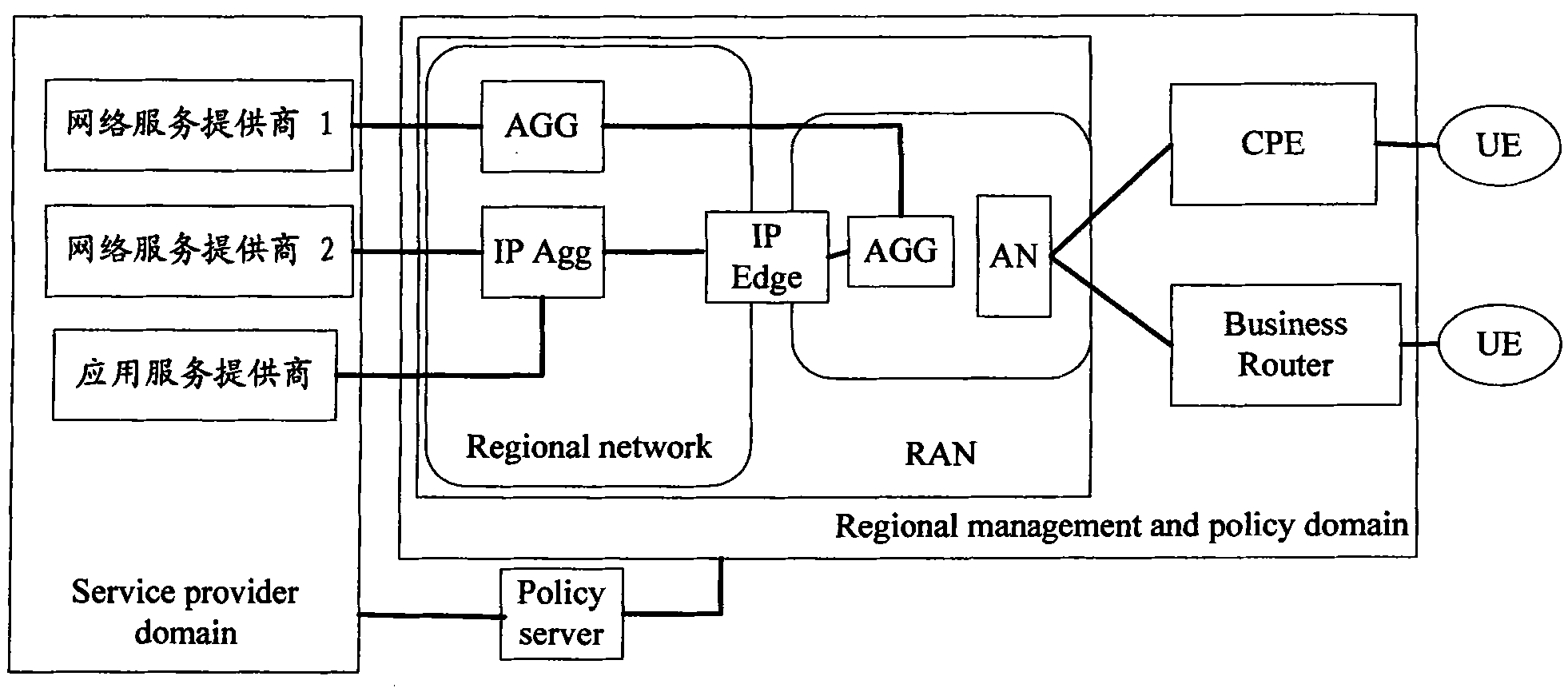
[0085] In the present invention, the access broadband network gateway is an IP edge device.
[0086] Step 202, the gateway for accessing the broadband network sends an access request message to the AAA server, requesting the AAA server to perform access authentication and authorization for the user.
[0087] Step 203.1: The AAA server responds to the user access authentication and authorization request to the access broadband network gateway, authenticates the user and provides authorization information of the ...
Embodiment 2
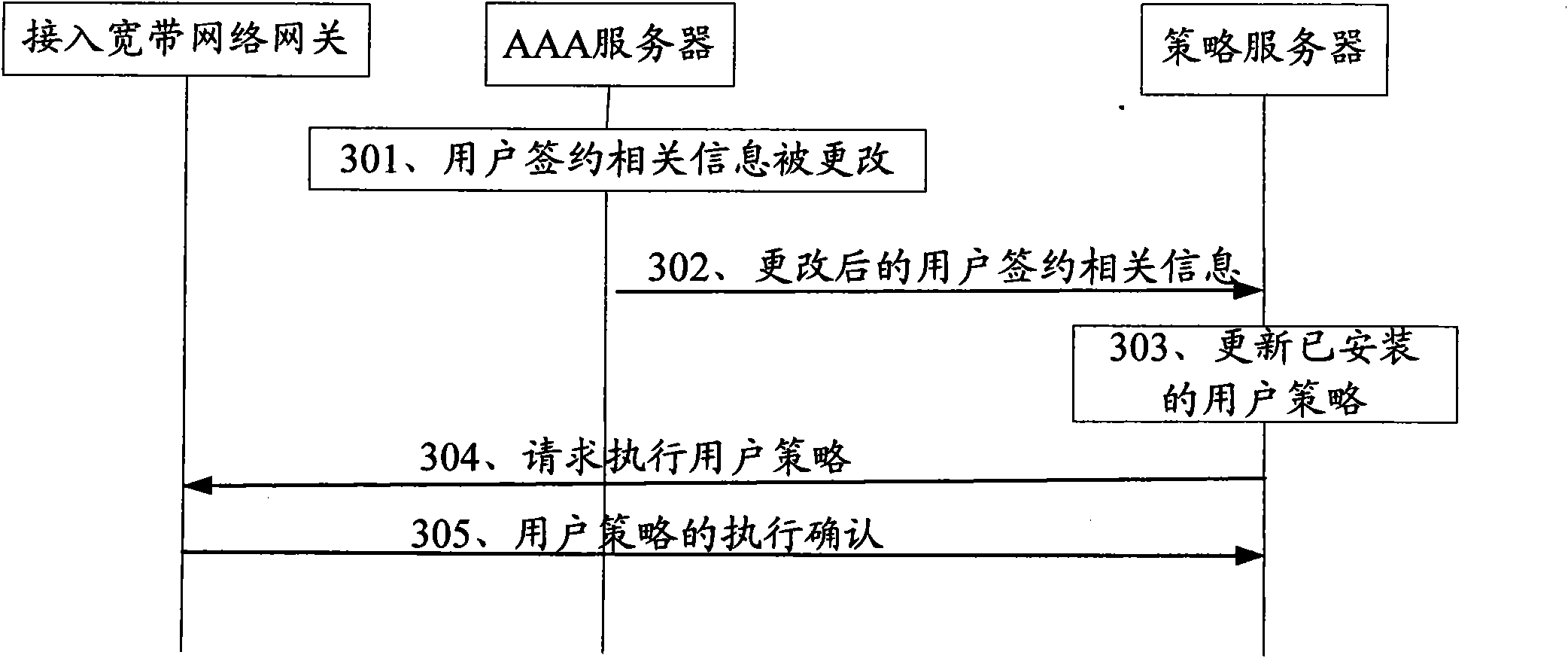
[0095] In this embodiment, when the user subscription information in the AAA Server is changed, the AAA Server interacts with the policy server to trigger the policy server to update the installed user policy as an example. The specific process is as follows: image 3 Shown:
[0096] In step 301, the AAA server detects that information related to user subscription has been changed.
[0097] For example, a user who has already accessed the network changes his subscription-related information in the AAA server. This embodiment is not limited to the user's modification of user subscription-related information, and is also applicable to other entities in the network that have modified user subscription information.
[0098] Step 302, the AAA server sends the changed user subscription related information to the policy server.
[0099] Specifically, if the AAA server interacts with the policy server through the diameter protocol, the AAA server sends the user subscription-related ...
Embodiment 3
[0105] In this embodiment, when the user subscription information in the policy server is not available, the policy server actively requests the AAA server for the subscription information and installs the user policy as an example. The specific process is as follows: Figure 4 Shown:
[0106] Step 401, the policy server detects that the user subscription-related information is unavailable;
[0107] The unavailability of the user subscription-related information may be that the user subscription-related information is lost or incomplete.
[0108] For example, when receiving a service resource request sent by a network service provider or an application service provider, the policy server detects that information related to user subscription related to the application is unavailable.
[0109] Step 402, the policy server requests the user subscription related information from the AAA server.
[0110] Specifically, if the AAA server interacts with the policy server through the ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com