Method for accessing and monitoring private network through layer 2 tunnel protocol and server
A layer-2 tunneling protocol and server technology, applied in the field of L2TP server and public network user equipment, can solve the problems of wasting egress bandwidth resources, occupation, public network user impact, etc.
Inactive Publication Date: 2011-06-29
NEW H3C TECH CO LTD
View PDF6 Cites 27 Cited by
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
If there are access restrictions or access prohibition at the export of the enterprise, it will affect the public network users, and also occupy and waste the bandwidth resources of the enterprise's export
Method used
the structure of the environmentally friendly knitted fabric provided by the present invention; figure 2 Flow chart of the yarn wrapping machine for environmentally friendly knitted fabrics and storage devices; image 3 Is the parameter map of the yarn covering machine
View moreImage
Smart Image Click on the blue labels to locate them in the text.
Smart ImageViewing Examples
Examples
Experimental program
Comparison scheme
Effect test
Embodiment Construction
the structure of the environmentally friendly knitted fabric provided by the present invention; figure 2 Flow chart of the yarn wrapping machine for environmentally friendly knitted fabrics and storage devices; image 3 Is the parameter map of the yarn covering machine
Login to View More PUM
 Login to View More
Login to View More Abstract
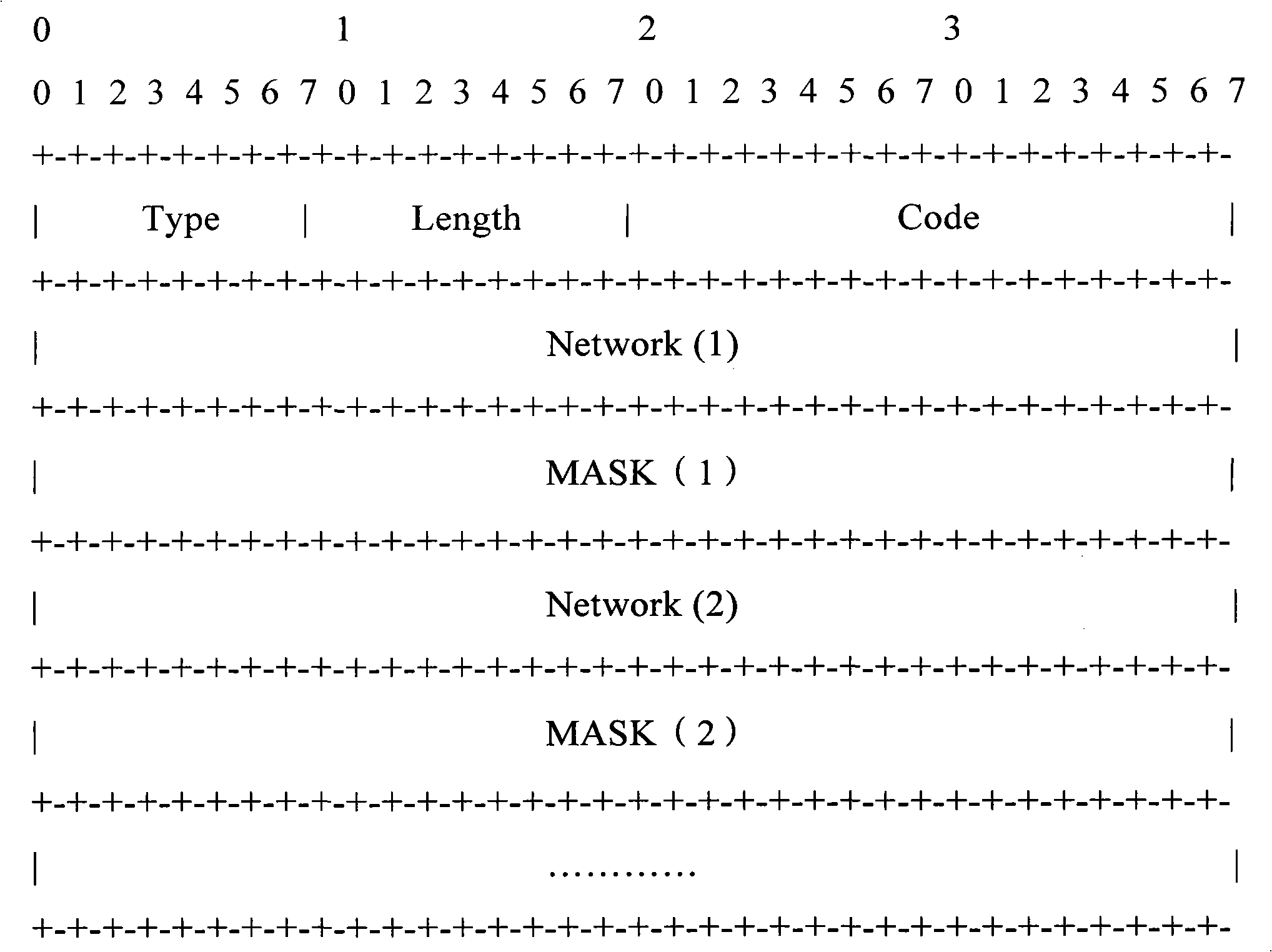
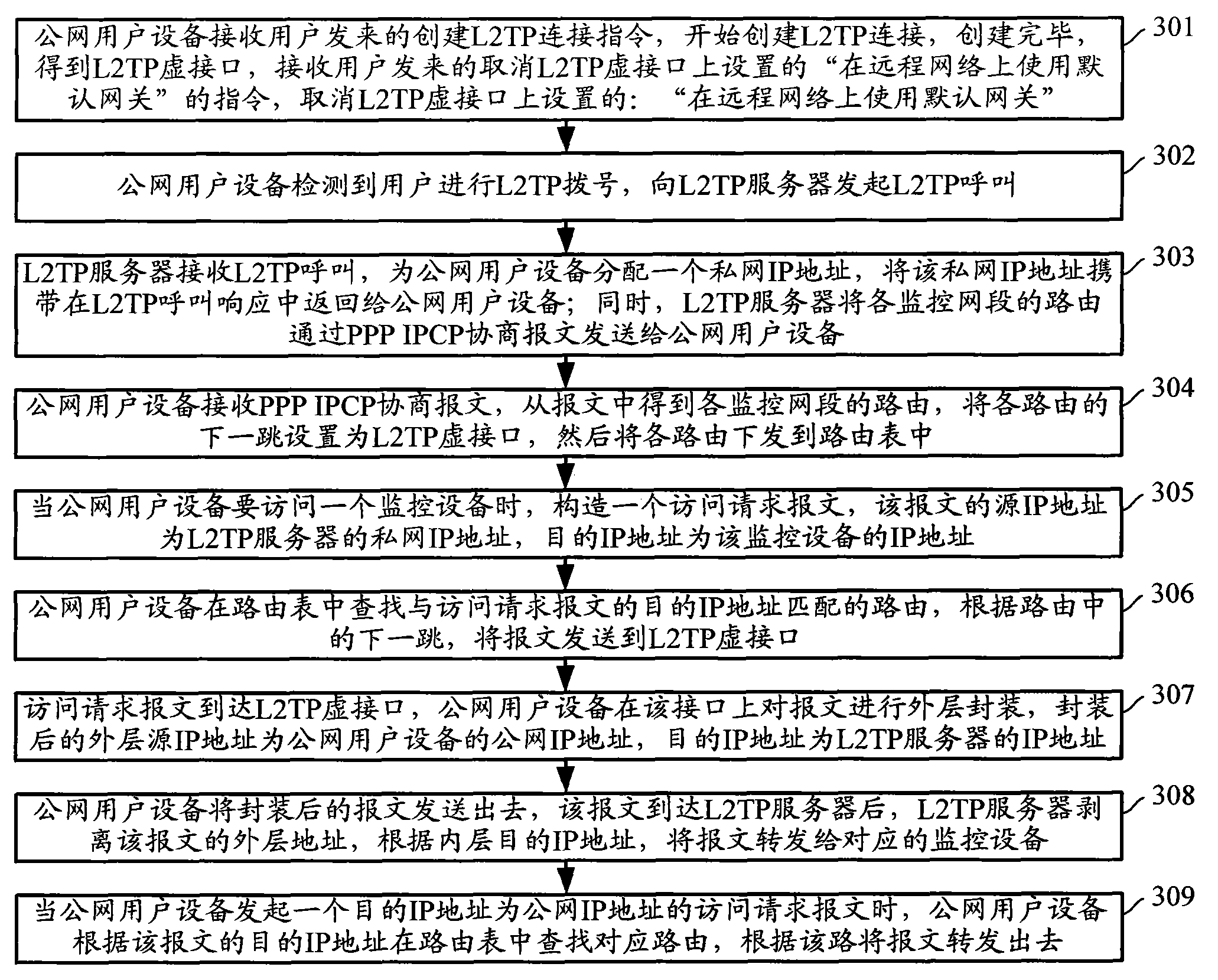
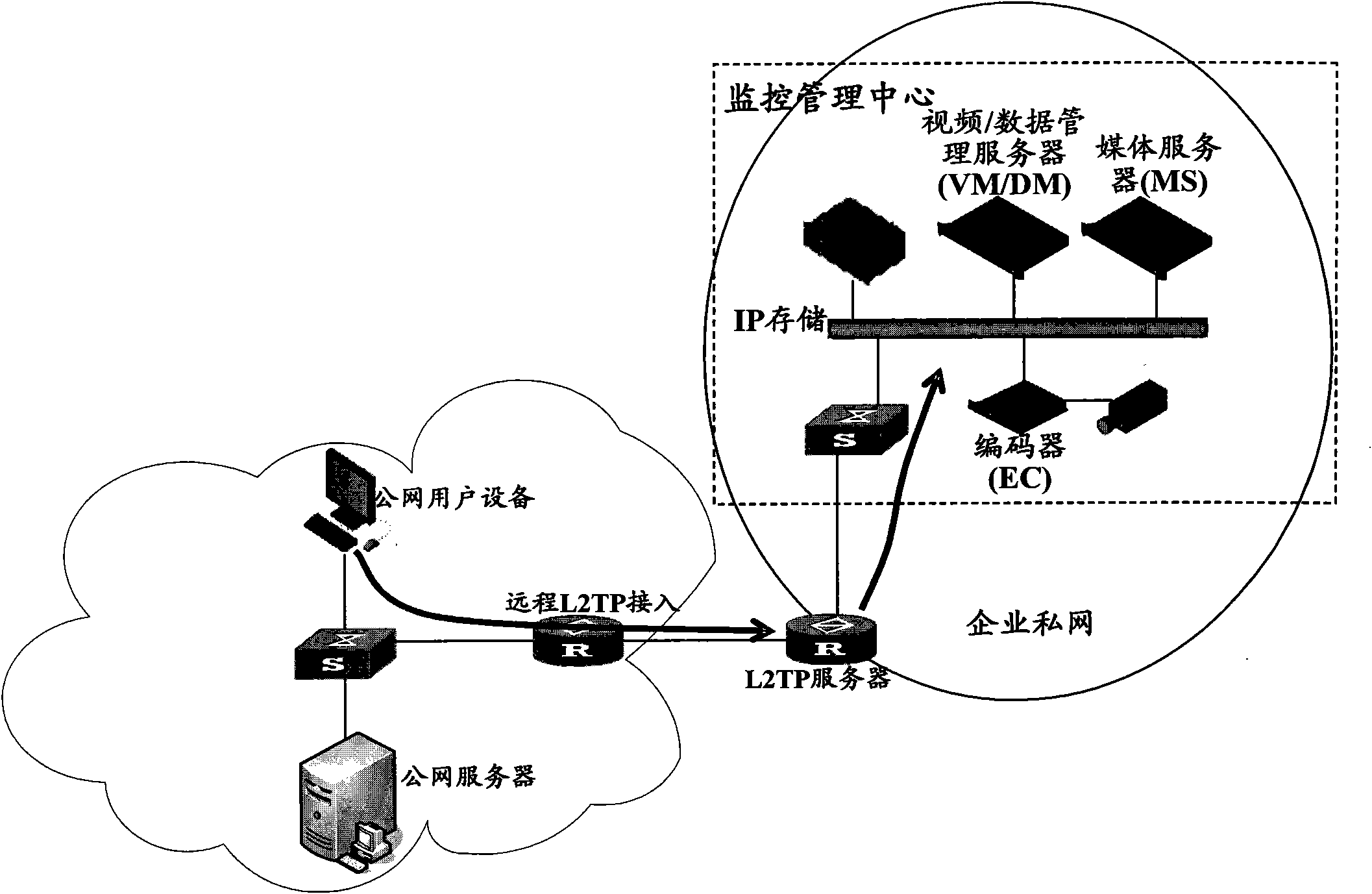
The invention discloses a method for accessing and monitoring a private network through a layer 2 tunnel protocol (L2TP) and a server. The method comprises that: 'use of a default gateway on a remote network' set on an L2TP virtual interface of public network user equipment is canceled in advance; an L2TP server receives an L2TP call initiated by the public network user equipment, distributes a private network internet protocol (IP) address to the public network user equipment, and simultaneously sends the route of each monitored network segment to the public network user equipment; the public network user equipment receives each route, sets the L2TP virtual interface thereof for next hop of each route, and transmits each route to a routing table; the public network user equipment initiates an access request aiming at monitoring equipment of the private network, finds the route of the matched monitored network segment in the routing table according to the IP address of the monitoring equipment, and sends the access request to the L2TP server through the L2TP virtual interface according to the next hop of the route; and the L2TP server forwards the access request to the monitoring equipment. The method enables a public network user to normally access the public network and monitor the private network.
Description
Method and server for accessing and monitoring private network through Layer 2 Tunneling Protocol technical field The invention relates to the technical field of monitoring, in particular to a method for accessing and monitoring a private network through a Layer 2 Tunnel Protocol (L2TP, Layer 2 Tunnel Protocol), an L2TP server, and public network user equipment. Background technique With the continuous development of standardized and easily expandable network technology and Internet Protocol (IP, Internet Protocol) technology, intelligent monitoring technology based on IP and network has developed rapidly, and IP monitoring has become the mainstream of current monitoring. For security and cost reasons, most surveillance networks are deployed on private networks. Many mobile users or public network users as video clients (VC, VideoClient) want to access the monitoring resources of the private network, they will dial up through the Layer 2 Tunneling Protocol (L2TP, Layer2Tun...
Claims
the structure of the environmentally friendly knitted fabric provided by the present invention; figure 2 Flow chart of the yarn wrapping machine for environmentally friendly knitted fabrics and storage devices; image 3 Is the parameter map of the yarn covering machine
Login to View More Application Information
Patent Timeline
 Login to View More
Login to View More Patent Type & Authority Applications(China)
IPC IPC(8): H04L12/26H04L12/24H04L12/56H04L29/06
CPCH04L61/2038H04L63/0272H04L63/306H04L67/14H04L41/0806H04L63/00H04L63/162H04L12/4633H04L12/4641H04L61/5038H04L41/0895H04L41/0897
Inventor 任俊峰周迪
Owner NEW H3C TECH CO LTD
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com