Mobile phone software encryption method
A technology of mobile phone software and encryption method, applied in electrical components, wireless communication, network data management, etc., can solve problems such as increasing costs, and achieve the effect of preventing theft
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0015] The present invention will be further described below in conjunction with accompanying drawing:
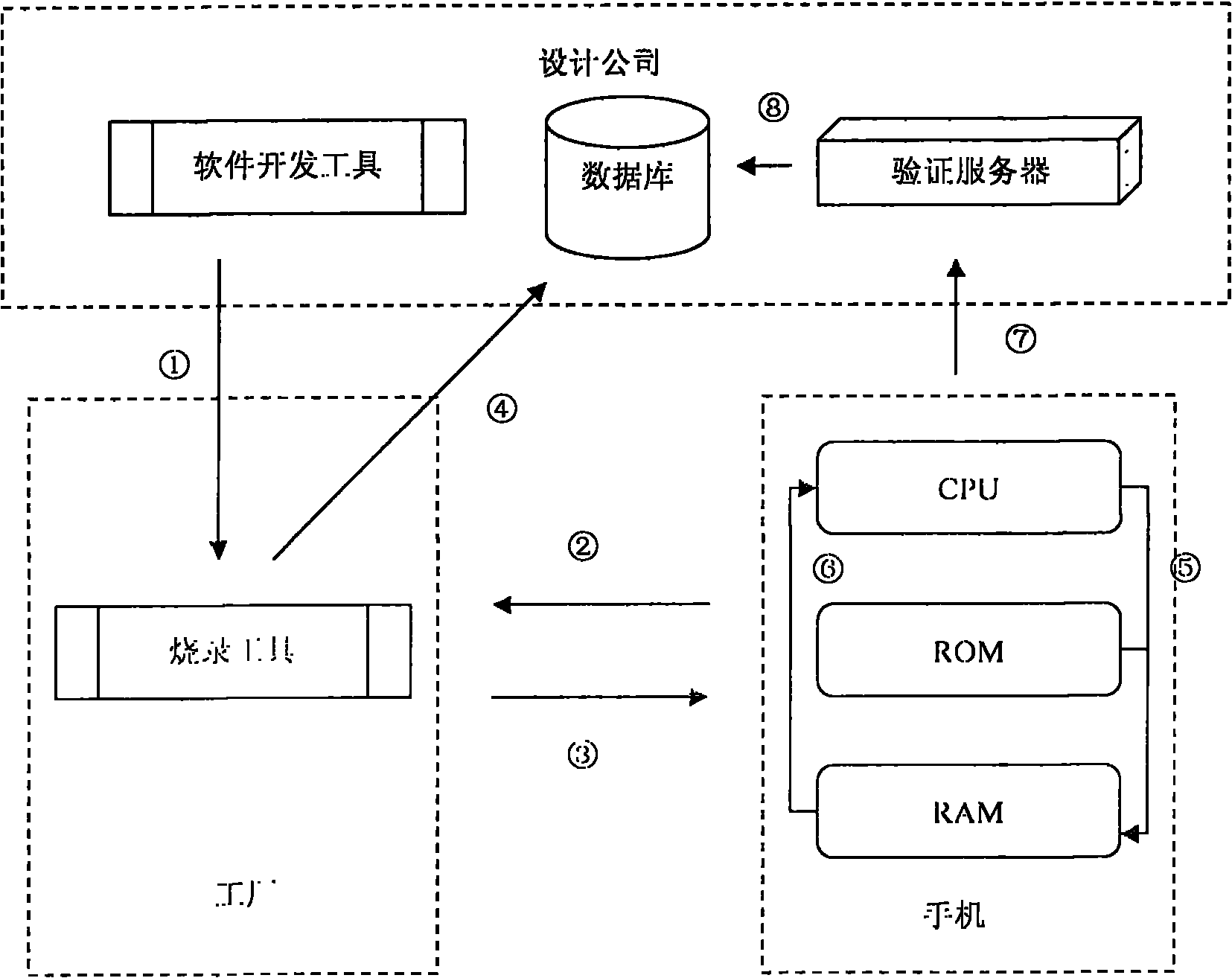
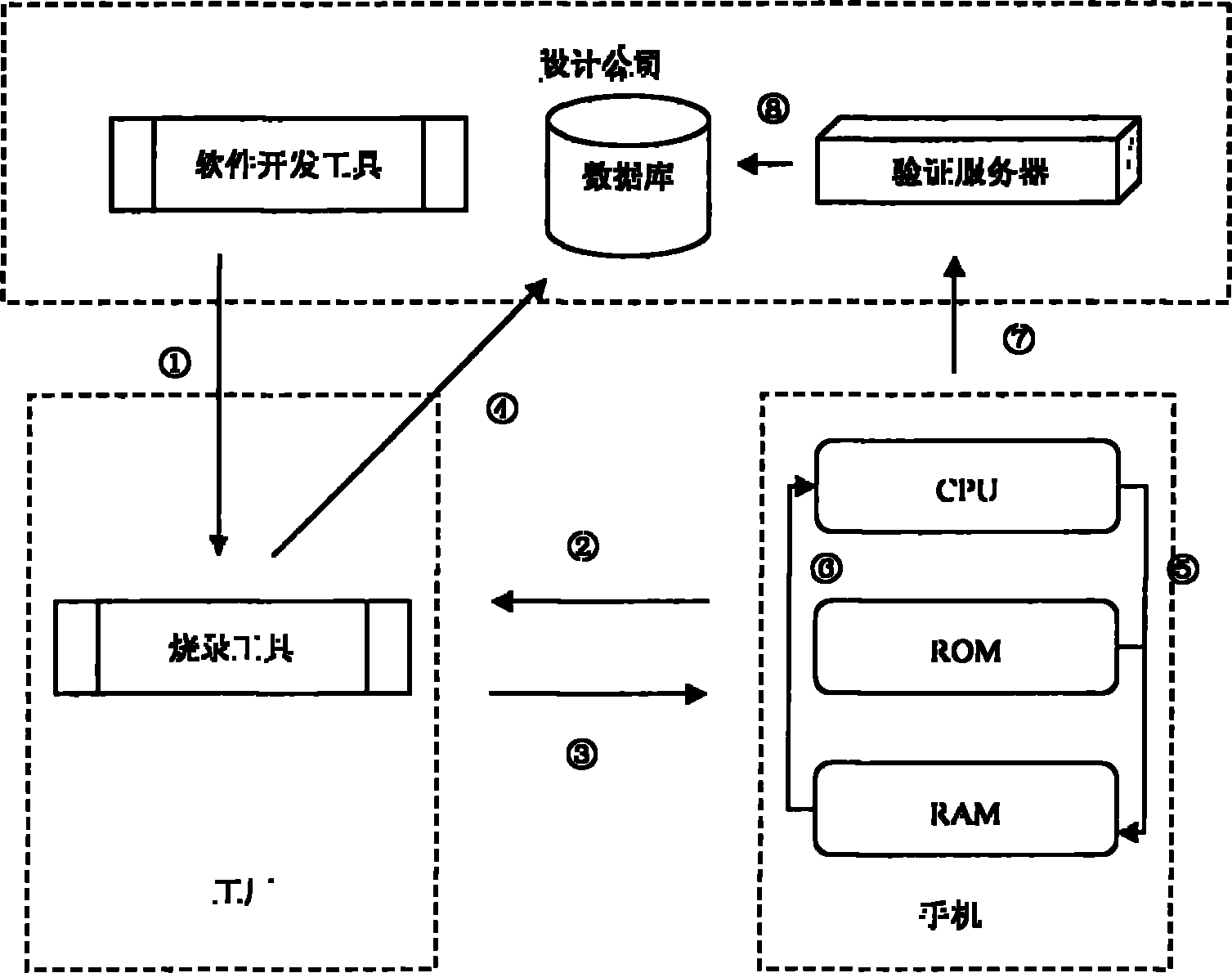
[0016] refer to figure 1 Shown, a kind of mobile phone software encryption method of the present invention comprises the following steps:
[0017] S1. After the design company completes the development of the mobile phone software, it compiles and connects it to a BIN file for burning in the factory;
[0018] S2. The mobile phone burning software first reads the unique identification code UID of the mobile phone CPU when burning, and the UIDs of any two CPUs are different;
[0019] S3. The mobile phone burning software uses the UID as the key to encrypt the key part of the code in the BIN file, and then burns the processed BIN file into the mobile phone;
[0020] S4. The mobile phone burning software records the UID of each mobile phone and imports them into the UID database of the verification server in batches;
[0021] S5. After the mobile phone is turned on, read the...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com